We’ve all heard of phishing attacks, but a new type of social engineering hack that uses your mobile phone to trick you is a little scarier.
I came across a Symantec video that explains a new way that attackers are trying to get into your email account. The idea is simple: if you want to reset someone’s password, all you really need is their mobile number.
The anatomy of the attack in the video is fairly simple, but surprisingly effective:
- Send the victim a text from an unknown number, warning them that they’re about to receive a code to ensure their Google account is secure and asking them to reply with the code to confirm
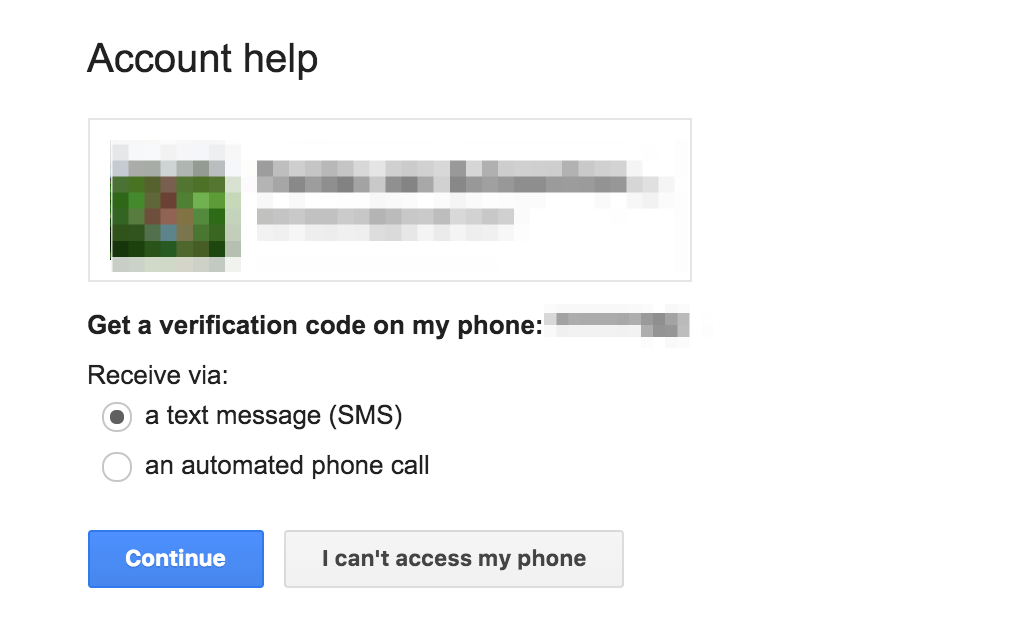
- Trigger the Gmail password reset process, which sends a message containing an unlock code to the registered phone

- The user receives the code they’ve been warned about and sends it back to the attacker
- Attacker logs in to Gmail account without detection
Before I saw this video, I’d never thought of such a method being used to get into someone’s account.
When I had imagined a hacker using social engineering to get into my account, I’d imagined them calling a help desk to trick them into giving out my information or simply sending me a phishing email.
For some reason, this is a dangerously potent trick that even I would probably have fallen for if I hadn’t heard of it.
Most people would likely reply to an unknown number simply assuming it really is the company, because receiving messages from companies on unknown numbers isn’t all that uncommon.
With the advent of services like Twilio and Nexmo that allow you to send a message directly from your computer with few traces, it makes it far easier to orchestrate this type of attack, given the right skills.
I wondered if it could be taken to the next level — some services actually allow you to send a text message that identifies as a company or person on the victim’s phone — so set out to send a message to myself with a familiar name rather than an unknown number.
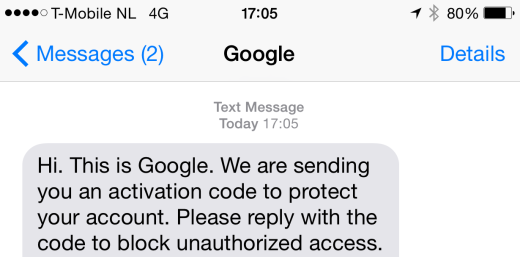
Within ten minutes of setting out to try it out, I had sent myself a text messaging from my Mac’s terminal posing as Google. It’s as easy as assuming any other company name by simply changing a word in the command.
That’s more than enough to fool even some of the smartest people into replying with their verification code, ultimately letting you into their accounts. It’s trivial to send a message with the name of any company, so this could be used to attack many services.
This attack could also be used to circumvent services that utilize two factor authentication, though it’s worth noting that Google will not send an SMS for your second factor if it’s already set up.
The problem with this type of attack is that it’s relatively hard to stop, outside of educating people to never reply to any sort of SMS that asks for a password or authentication code.
Many services now rely on sending an SMS to verify the user’s identity if you’ve forgotten your password, since a phone is an intimate device that’s most likely to be with you. This type of social engineering attack shows it’s still incredibly easy to fool people who have no way to know any better.
If you ever receive a message from any number asking for your password, login, confirmation code or any other personal information, we urge you not to reply to it. There’s simply no reason for companies to be asking for that — or any other information — over SMS.
Get the TNW newsletter
Get the most important tech news in your inbox each week.