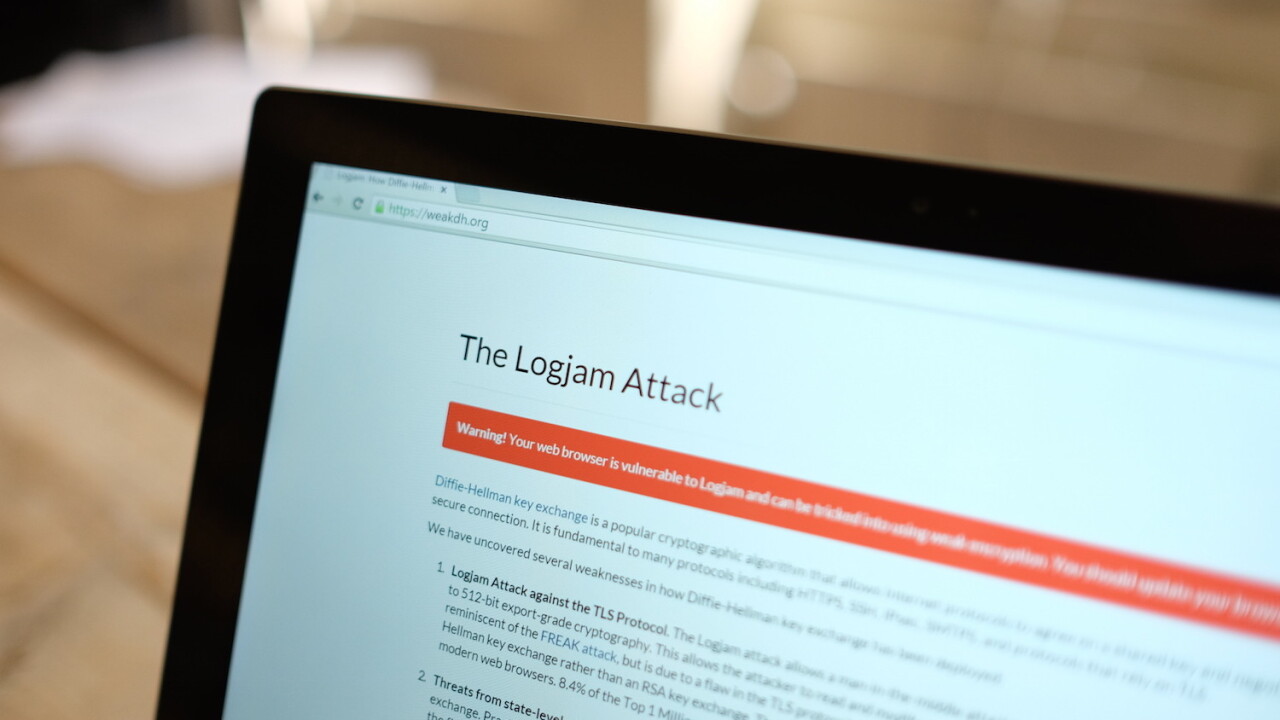
It seems like we just got over the Heartbleed vulnerability, but there’s another major flaw with SSL called “logjam” that affects a number of fundamental Web protocols.
The bug affects an algorithm called the “Diffie-Hellman key exchange” which allows protocols such as HTTPS, SSH, IPsec, SMTPS to negotiate a shared key and create a secure connection.
Researchers from a number of universities and organizations discovered a number of weaknesses in the algorithm and published a technical report that details its flaws.
The attack allows a man-in-the-middle to downgrade security of connections to a lower level of encryption — 512 bit — which can be read and attacked with relative ease.
It also means that organizations who have large amounts of computing power available to them, such as the NSA, could break even stronger encryption that uses the algorithm.
The report estimates that up 8.4 percent of the top 1 million domains are vulnerable, along with a huge number of email services and other systems.
You can check if your browser is vulnerable here. At time of writing the major browsers are still open to the attack, however Google is already working to increase the SSL requirement in Chrome to 1024 bit.
Those operating Web servers are advised to follow these step-by-step instructions to ensure they’re protected.
➤ Logjam TLS attack [Weak DH]
Read Next: OpenSSL has a critical security vulnerability that needs to be patched right away
Get the TNW newsletter
Get the most important tech news in your inbox each week.




