A new piece of malware that takes the form of fake extensions for Google Chrome and Mozilla Firefox which in turn hijack Facebook, Twitter, and Google+ accounts has been discovered. Users of these browsers and social networks are lured into downloading what they think is a video player update. To make matters worse, the threat is digitally-signed.
The malware, which was first discovered by security firm Trend Micro, is detected as TROJ_FEBUSER.AA. It installs a browser extension for Chrome and an add-on for Firefox, but doesn’t adapt itself to Internet Explorer, Safari, nor Opera.
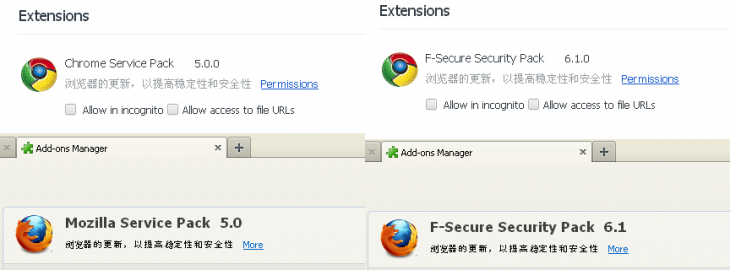
The threat in question tries to trick the user by claiming to be a “service pack” for either Chrome or Mozilla, depending on what browser is accessing the page, and newer versions use the name “F-Secure,” in reference to the security company:
Once installed, the malware calls home to download a configuration file, which in turn includes details for hijacking the user’s social media accounts. It can then perform the following actions, without any authorization from the user: Like pages, share posts, join a group, invite friends to a group, chat with friends, post comments, and update statuses.
That description seems to be very Facebook-specific, and is quite similar to a Facebook threat Microsoft discovered two months ago, but Trend Micro insists that Twitter and Google+ accounts are affected as well. The company further notes that because of these actions, the attackers could, for example, use the accounts to spread malicious links to their threat or others.
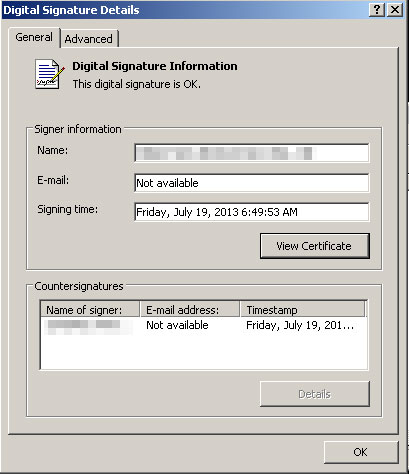
Since the fake video player update is digitally signed, users might be tricked into thinking the file comes from a legitimate source. As we know, that’s not necessarily true; here’s what Trend Micro has to say about the digital signing:
Digital signatures are a way for developers and publishers to prove that a file did come from them and has not been modified. Potential victims may take this to mean that the file is legitimate and harmless. It is not yet clear if this signature was fraudulently issued, or a valid organization had their signing key compromised and used for this type of purpose.
Malware authors like to target popular browsers as it means they can attack users regardless of the operating system they are running. A word of advice to both Chrome and Firefox users, especially given the digital signature: make a point to only install browser extensions and add-ons from trusted sources such as the Chrome Web Store and Add-ons for Firefox.
See also – Google further secures Chrome against malicious extensions and Latest study finds IE10 is better at blocking malware than Chrome, Safari, Firefox, and Opera
Top Image Credit: Dimitris Ouzounis
Get the TNW newsletter
Get the most important tech news in your inbox each week.