
A hacker has launched a cyber attack on a number of servers owned by the Pakistani government, causing a number of official departmental websites, including the Ministry of Science and Technology, Ministry of Information Technology and Ministry of Economic Affairs & Statistics, to crash.
The Hacker News has reported that an anonymous Indian hacker, known simply as ‘Godzilla’, is still targeting the Pakistani government because of its alleged support for terrorism activities.
The hacker is cited as saying: “All network owned including switches because they deserve it, I have not touched any innocent website because target is only Government.”
The following websites are currently affected as a result of the security breach:
- www.moitt.gov.pk
- www.railways.gov.pk
- www.ead.gov.pk
- www.interior.gov.pk
- www.ipc.gov.pk
- www.mora.gov.pk
- www.establishment.gov.pk
- www.housing.gov.pk
- www.mosp.gov.pk
- www.planningcommission.gov.pk
- www.minorities.gov.pk
- www.lgrd.gov.pk
- www.moenv.gov.pk
The Hacker News also reports that the portal website for the Pakistani government went down for more 24 hours. The authorities have since managed to recover the server, and at the time of writing appears to be working normally.
Anyone attempting to access one of the affected websites will see the following screen:
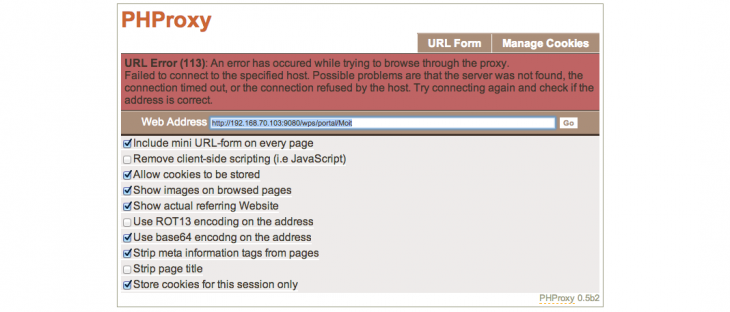
The Indian hacker claims to have breached the Pakistani government’s centralized IBM server with a Layer 2-3 Gigabit Ethernet Switch Module for IBM eServer, BladeCenter. The affected server was then connected to 22 local machines, which were used to build a proxy server that bypassed the security measures in place.
Image Credit: Arif Ali/AFP/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.




