A new Java 0-day vulnerability has been discovered, and is already being exploited in the wild. Currently, disabling the plugin is the only way to protect your computer.
Update on December 11: Oracle’s Java vulnerability left open since October 2012 ‘fix’, now being used to push ransomware
The US Computer Emergency Readiness Team (US-CERT), which falls under the National Cyber Security Division of the Department of Homeland Security, has issued the following vulnerability note:
Overview – Java 7 Update 10 and earlier contain an unspecified vulnerability that can allow a remote, unauthenticated attacker to execute arbitrary code on a vulnerable system.
Description – Java 7 Update 10 and earlier contain an unspecified remote-code-execution vulnerability. This vulnerability is being attacked in the wild, and is reported to be incorporated into exploit kits.
Impact – By convincing a user to visit a specially crafted HTML document, a remote attacker may be able to execute arbitrary code on a vulnerable system.
It appears this flaw was first stumbled upon by a French researcher who goes by the name Kafeine. In a post on his Malware Don’t Need Coffee website, the researcher claimed that the latest version, Java 7 Update 10, was being exploited on a site that receives “hundreds of thousands of hits daily” and concluded that “this could be mayhem.”
More importantly, Kafeine noted the two most popular Web threat tools used by hackers to distribute malware, the BlackHole Exploit Kit and the Cool Exploit Kit, already have this latest Java exploit. BitDefender confirmed the alleged addition of the exploit into Cool while security expert Brian Krebs confirmed the BlackHole part, as well as noted its addition into Nuclear Pack:
The curator of Blackhole, a miscreant who uses the nickname “Paunch,” announced yesterday on several Underweb forums that the Java zero-day was a “New Year’s Gift,” to customers who use his exploit kit. Paunch bragged that his was the first to include the powerful offensive weapon, but shortly afterwards the same announcement was made by the maker and seller of Nuclear Pack.
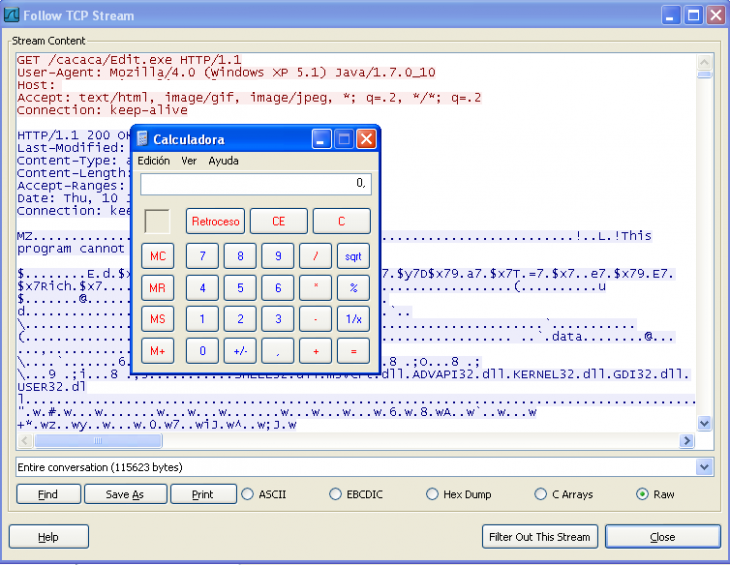
This actual vulnerability was later confirmed by security firm AlienVault Labs. With Kafeine’s help, the company reproduced the exploit on a new, fully-patched installation of Java, and used a malicious Java applet to remotely execute the Calculator application on Windows XP:
We recommend that regardless of what browser and operating system you’re using, you should uninstall Java if you don’t need it. If you do need it, use a separate browser when Java is required, and make sure to disable Java in your default browser.
We have contacted Oracle about this issue. We will update you if we hear back.
Update on December 11: Oracle’s Java vulnerability left open since October 2012 ‘fix’, now being used to push ransomware
See also – Security companies are recommending you disable Java, or just uninstall it and Mozilla joins the chorus, tells Firefox users to disable Java due to security hole
Image credit: Sander Klaver
Get the TNW newsletter
Get the most important tech news in your inbox each week.