On Wednesday, security professional Gaurang Pandya outlined how Nokia is hijacking Internet browsing traffic on some of its phones. As a result, the company technically has access to all your Internet content, including sensitive data that is sent over secure connections (HTTPS), such as banking credentials and pretty much any other usernames and passwords you use to login to services on the Internet.
Update: Nokia has confirmed the behavior, but says it is nothing to worry about, as outlined in the update at the bottom of this article.
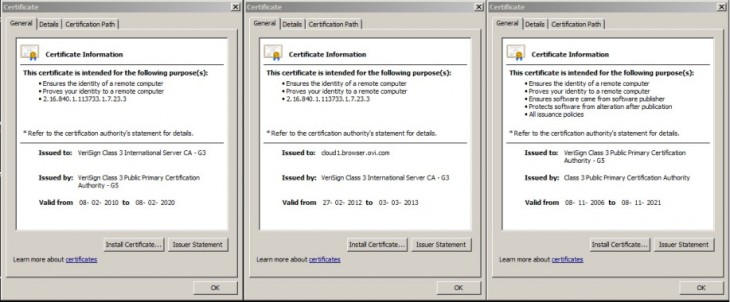
Last month, Pandya noted his Nokia phone (an Asha 302) was forcing traffic through a proxy, instead of directly hitting the requested server. The connections are either redirected to Ovi proxy servers if the Nokia browser is used, or to Opera proxy servers if the Opera Mini browser is used (both apps use the same User-Agent).
While there was no indication that Nokia is conducting a man-in-the-middle (MITM) attack, it certainly could be. This led him to wonder about what Nokia could be doing behind the scenes with all this information, and a new investigation this month. He wanted to verify that HTTPS traffic, at the very least, is being transferred without any intermediate host inspecting it.
Pandya attempted to verify this by checking if DNS requests are sent for the requested website and if the certificate is sent from the server. He couldn’t confirm the former wasn’t happening with certainty but he did prove the latter isn’t happening.
Here is his conclusion:
From the tests that were preformed, it is evident that Nokia is performing Man In The Middle Attack for sensitive HTTPS traffic originated from their phone and hence they do have access to clear text information which could include user credentials to various sites such as social networking, banking, credit card information or anything that is sensitive in nature. In short, be it HTTP or HTTPS site when browsed through the phone in subject, Nokia has complete information unencrypted (in clear text format) available to them for them to use or abuse.
The goal here is to save bandwidth, but the way it is being done is rather questionable. We were aware that Opera does this in order to speed up site loading, but Nokia’s approach, which is different than Opera’s when it comes to HTTPS, is worth discussing further.
We have contacted Nokia about Pandya’s findings. We will update this article if we hear back.
Update on January 10: Nokia has released the following statement.
We take the privacy and security of our consumers and their data very seriously. The compression that occurs within the Nokia Xpress Browser means that users can get faster web browsing and more value out of their data plans. Importantly, the proxy servers do not store the content of web pages visited by our users or any information they enter into them. When temporary decryption of HTTPS connections is required on our proxy servers, to transform and deliver users’ content, it is done in a secure manner.
Nokia has implemented appropriate organizational and technical measures to prevent access to private information. Claims that we would access complete unencrypted information are inaccurate.
We aim to be completely transparent on privacy practices. As part of our policy of continuous improvement we will review the information provided in the mobile client in case this can be improved.
Image credit: Mateusz Stachowski
Get the TNW newsletter
Get the most important tech news in your inbox each week.