![Facebook acknowledges messaging vulnerability that allows sending of malicious files [Updated]](https://img-cdn.tnwcdn.com/image?fit=1280%2C720&url=https%3A%2F%2Fcdn0.tnwcdn.com%2Fwp-content%2Fblogs.dir%2F1%2Ffiles%2F2011%2F10%2Ffacebook_wallpaper_glow_by_will_yen1.png&signature=05bd018e8c11658f8e7a0c9857fe0921)
This article has been updated, see below for details.
A security researcher has detected and disclosed a new vulnerability on Facebook that allows a third-party to use the social network’s Messages service to attach malicious files and send them to any user registered on the website.
The exploit, which focuses on how Facebook interprets file uploads within messages, was submitted to Facebook September 30 by penetration tester Nathan Power and was recognised by the company on Wednesday.
By default, Facebook blocks malicious file uploads, preventing users from attaching executable or batch files that would be able to infect a computer if downloaded and run. Facebook would typically issue the response: “Error Uploading: You cannot attach files of that type.”
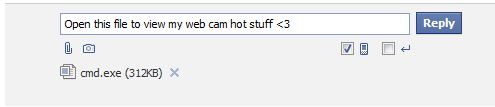
However, Power was able to analyse the responses that the Facebook website returned when his browser made a POST request to its webserver, finding a variable that would tell the system that a filename had been attached and determine whether it would be approved for sharing via the service:
Content-Disposition: form-data; name=”attachment”; filename=”cmd.exe”
Power amended the POST request, adding a space to the filename variable, allowing him to bypass the filename check and attached a potentially malicious executable file.
Due to the nature of Facebook’s messaging system, it could potentially allow an attacker to send messages to anyone on the service, regardless of whether they were friends.
Power notes that Facebook is aware of the issue, which is as much to say that the vulnerability may have already been patched by its development team, which is primarily located in California.
Yesterday, we reported that Facebook’s cyber-security system processes and checks 650,000 actions every second to keep its users safe from spam and cyber-attacks on the social network. The Facebook Immunity System (FIS), as it’s known, is said to highly efficient also, with just 1% of users reporting issues as spam.
We have contacted Facebook for comment and will update the article should we received a response.
Update: Facebook’s Security Manager Ryan McGeehan had this to say:
This finding will only allow one user to send an obfuscated renamed file to another Facebook user. The proof of concept, as is, would not execute on a recipients machine without an additional layer of social engineering. Beyond that, we are not going to rely solely on string matching as a protective measure, since zip files and other things could also have unpredictable behaviors when sent as an attachment.
We are AV scanning everything that comes through as a secondary measure, so we have defense in depth for this sort of vector. This puts us at a similar level of protection as most webmail providers who deal with the similar risk, and this finding is a very small part of how we protect against this threat overall.At the end of the day, it is more practical for a bad guy to hide an .exe on a convincing landing page behind a URL shortener, which is something we’ve been dealing with for a while.
Get the TNW newsletter
Get the most important tech news in your inbox each week.