
The first Sony executives knew about the calamitous data breach, which would send their emails spilling across the Web, was an image of a skeleton flashing up on their computers screens with the warning: “…this is just a beginning.”
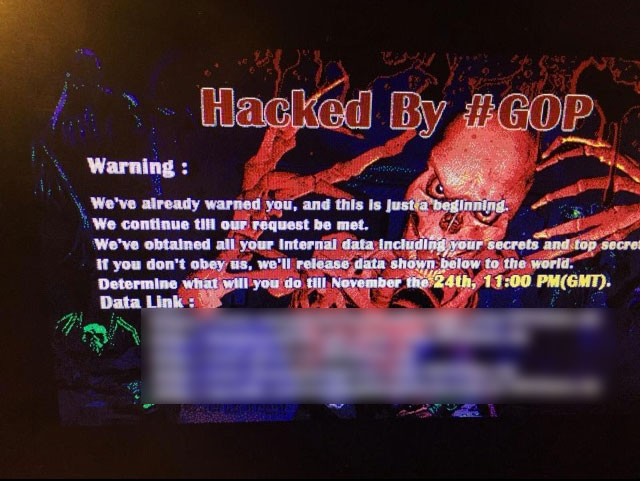
If the hackers hadn’t decided to publicly embarrass the company, it’s likely that many weeks, if not months, could have passed before it became aware of the leaks.
A report by the Ponomon Institute, a privacy and data security research center, found the average time to detect an attack in 2014 was 170 days, rising to 259 days if an insider with access to a company’s network was involved.
That’s where Terbium Labs, a Baltimore-based startup founded by a pair of academics with backgrounds in large scale data analysis, quantum cryptography and working with the intelligence services, comes in.
The company’s first product, Matchlight, is a data intelligence system that it claims can instantly locate stolen data on the dark Web as soon as it appears, as well as on more publicly accessible sites and forums.
The principle is not to claim that the horses will never bolt, but to make it much easier to find out where they end up once the stable door is broken.
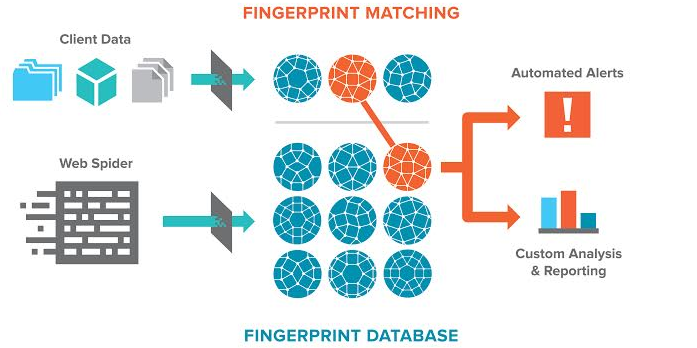
Terbium Labs CEO Danny Rogers explained to me how Matchlight can scan for a company’s data without having to actually store or have permanent access to that sensitive information:
We use cryptographic hashing to break the data into small pieces. We maintain a fingerprint – a large set of cryptographic hashes – and search for the equivalent values as we crawl the internet.
Delving into the dark Web
The system can identify chunks of information as small as 14 characters and uses a Web crawler with a particular focus on the dark Web.
The company CTO, Michael Moore, expands on that:
We seed the Web crawler with sites and allow it to find new links, like most other crawlers out there, but we also look at Tor Hidden Services and I2P. We discover new marketplaces and forums by looking for people talking about them online and sharing new links.
Rogers believes Sony would have been notified of its dramatic data loss within minutes or even seconds if it had been using Matchlight and offers the example of one of the company’s beta testers, one of the ‘big five’ banks:
Our system identified about 3,000 of its credit card numbers appearing on a dark Web marketplace within about 30 seconds of that leak. That allowed it to know which accounts were compromised before any fraudulent transactions occurred.
In the wake of the Silk Road, whose apparent mastermind Ross Ulbricht was jailed for life last week, there has been a significant growth in decentralized dark Web marketplaces. Rogers argues that Matchlight will do something human analysts simply can’t:
All these dark Web markets are still accessible. A lot of the time data is being gathered by human analysts but there’s no way they can keep track on the expansion of these services. Our crawling technique automatically discovers and fills in those gaps. We’re reading the internet at computer speed, not human speed.
A light defence
The name “Matchlight” is inspired by The Christophers mission statement – “It’s better to light one candle than to curse the darkness.” – and it’s certainly a more pragmatic approach than believing that building up your defences against attacks will ever be enough.
Rogers argues:
In an era when threats are getting increasingly sophisticated, businesses need to look beyond their own borders. They need to know that data will leak and deal with that. It’s a risk management problem, not just an IT problem.
Terbium has been running a private beta programme for Matchlight since January with five Fortune 500 and Fortune 5000 companies. From today, it’s opening up that effort to more companies.
While the Sony leak was manna from heaven for the media, it caused a long, painful hangover for hundreds of people. If Matchlight is successful, we could end up seeing data breaches been mopped up quicker and their effects minimised. That’ll make for less dramatic copy, but much better business.
Read next: Silk Road, the dark net and still being the Bill in ‘Bill & Ted’: We talk to Alex Winter
Feature image credit: Godruma/Shutterstock
Get the TNW newsletter
Get the most important tech news in your inbox each week.





