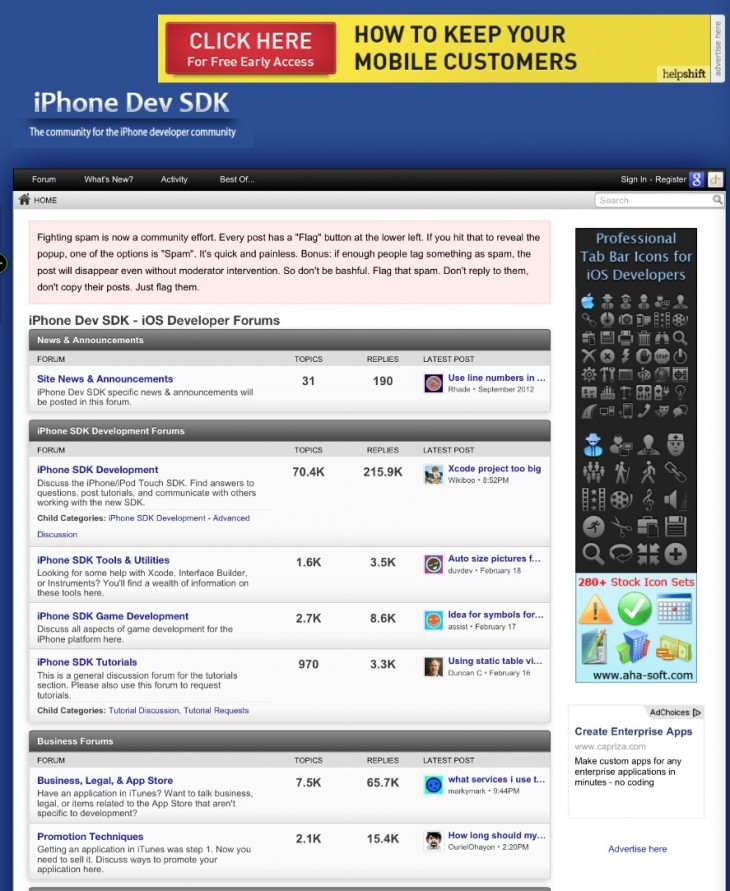
Since the Facebook hacking a few weeks ago and the Apple hacking announcement today have had one common thread: an unnamed mobile development site. This site had been frequented by members on the development teams, specifically the iOS development teams, of all of these companies.
The site’s name, which has also been exposed in reports by All Things D and The New York Times, is iPhoneDevSDK. Absolutely, positively do not visit this site, at all. If you do, you run the risk of being infected as the site is believed to still be infected by the malware which exploits a vulnerability in Java to install itself onto visiting computers. The information that this is probably the site in question comes from sources close to the Facebook hacking investigation.
Though it wasn’t mentioned, it is extremely likely that visits to this site were also behind the hacking of Twitter, as the company’s disclosure also mentions that a Java vulnerability was exploited there, and recommends disabling it.
Earlier today, Apple said the following:
Apple has identified malware which infected a limited number of Mac systems through a vulnerability in the Java plug-in for browsers. The malware was employed in an attack against Apple and other companies, and was spread through a website for software developers.
On its hacking, Facebook’s statements had a similar tone:
Last month, Facebook Security discovered that our systems had been targeted in a sophisticated attack. This attack occurred when a handful of employees visited a mobile developer website that was compromised. The compromised website hosted an exploit which then allowed malware to be installed on these employee laptops.
Because the vulnerability used was not protected against either by Apple’s patches or common anti-virus software, it was able to infect the machines that had visited the site. It’s not clear what triggered the infection, though this is a prime example of how the vectors of infection are changing. Rather than targeting individuals via links in emails, the hackers here targeted a location that would be visited by developers across various companies, as long as they had an interest in iOS. This is commonly called a ‘watering hole’ attack.
The site contains forums with up to 70k topics under the category of iPhone SDK Development, as well as those dedicated to tools and utilities, game development and legal advice about selling on the App Store. Currently it is not known if the site had any active role in the hacks, though it seems likely that it was the work of a third party. Both Apple and Facebook say that they are working with authorities to track down the hackers.
The issues surrounding the site are interesting, as it is an extremely common and popular destination for iOS developers. This means that many more companies could be affected by it. If there is an iOS development team on a company’s staff then this could be (and probably is) one of its resources, and if it is, then there’s a definite chance that the hack could have affected it as well.
Currently, iPhoneDevSDK has been placed into maintenance mode, likely while it is being investigated for evidence of the Java exploit by its owners or investigators.
Apple has been agressive recently about blocking Java plugins on Mac machines entirely, and released a patch today to fix this vulnerability on newer machines. Still, if you or anyone at your company has visited the site recently, then you should apply the latest Apple Java updates and check your system for malware.
Image Credit: Justin Sullivan/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.