On Tuesday we broke the news that a new Trojan for OS X had been discovered, the first fake malware installer for the platform. Apple on Thursday added definitions for the malware to its “Xprotect.plist” blacklist, according to MacRumors.
Two days is a very quick turnaround and Apple should be applauded for taking initiative to mitigate the issue. The definitions are part of the company’s basic anti-malware tools launched with OS X Snow Leopard in August 2009.
The original version required users to update definitions manually, but as malware threats against OS X grew, Apple last year instituted automatic daily checks to keep users protected. This means most Apple users should be protected from this new threat as of today, assuming they have automatic updates turned on.
The malware discovered on Tuesday attempts to monetize its attack by having users enter their mobile phone numbers for the purpose of “activation.” The threat, detected as “Trojan.SMSSend.3666” by Russian security firm Doctor Web, is similar to fake installer schemes that previously only existed on Windows.
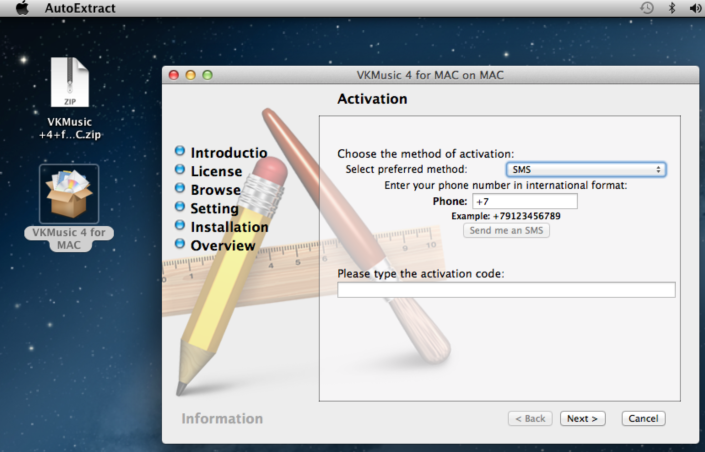
In case you missed it yesterday, here’s how the scheme works. When a user launches the fake installer on OS X, he or she is presented with an interface that imitates the installation wizard of a corresponding application:
In order to continue the “installation process,” the user is prompted to enter their cellphone number into the corresponding field and then input a code they are to receive via SMS. By doing so, the user is charged a subscription fee debited to their mobile phone account on a regular basis.
After that, the cybercriminal has achieved his or her goal, and the installer either installs the legitimate app it claims to mimic, which is naturally also available for free on its corresponding official site, or just spits out meaningless data. It’s not the most effective attack, as many users would not enter their phone number in the app.
Naturally such an attack is more successful on mobile platforms such as Android, but as I pointed out yesterday, cybercriminals clearly have found the scheme works on desktops too. It appears Apple agrees and has worked quickly to help its customers stay protected.
Image credit: David Tipton
Get the TNW newsletter
Get the most important tech news in your inbox each week.