Update on December 13: Two days after first OS X fake installer malware found, Apple updates definitions to fight SMS scam
A new Trojan for Mac has been discovered that mimics the actions of an installer. The malware attempts to monetize the attack by having users enter their mobile phone numbers for the purpose of “activation.”
The threat, detected as “Trojan.SMSSend.3666” by Russian security firm Doctor Web, is believed to be the first fake installer for Mac according to the company. Until now, this fake installer scheme only existed on Windows. It is reportedly available “in large numbers” on “various sites” under the guise of legitimate and useful software.
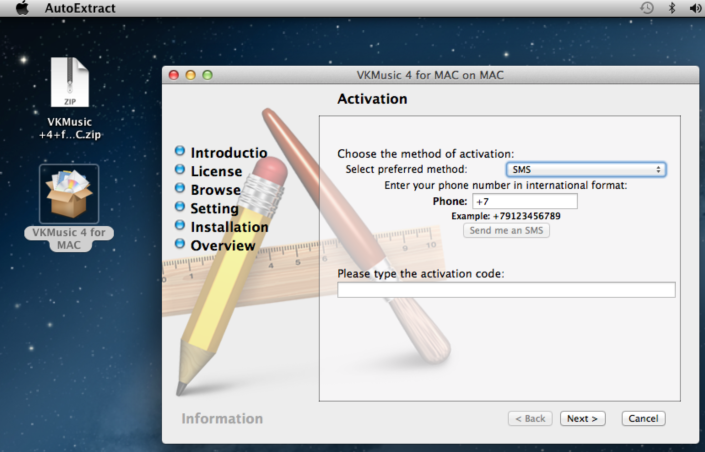
Here’s how it works. When a user launches the fake installer on OS X, he or she is presented with an interface that imitates the installation wizard of a corresponding application:
In order to continue the “installation process,” the user is prompted to enter their cellphone number into the corresponding field and then input a code they are to receive via SMS. By doing so, the user is charged a subscription fee debited to their mobile phone account on a regular basis.
After that, the cybercriminal has achieved his or her goal. The installer in question doesn’t even have to complete: Doctor Web says it has found installers that install the legitimate apps they claim to mimic, which are of course also available for free on their corresponding official sites, as well as ones that contain meaningless data.
Many would point out that having users enter their phone number into an app is very unlikely to work. While I would tend to agree, clearly cybercriminals have found the scheme works. Naturally such an attack is more successful on mobile platforms such as Android, but that doesn’t mean it won’t work on desktops. As more and more services ask for phone numbers, including massively popular social networks like Facebook and Twitter, this is only going to become more and more common in the malware world.
That being said, it’s quite telling that this type of attack has arrived on OS X before iOS: that’s how much harder it is to get malware on the latter than the former, arguably thanks to the Apple App Store. Yes, Windows and Mac app stores exist, but they are optional, and Android malware mainly spreads through app sideloading, not Google Play.
Update on December 13: Two days after first OS X fake installer malware found, Apple updates definitions to fight SMS scam
Image credit: Carlos Gustavo Curado
Get the TNW newsletter
Get the most important tech news in your inbox each week.