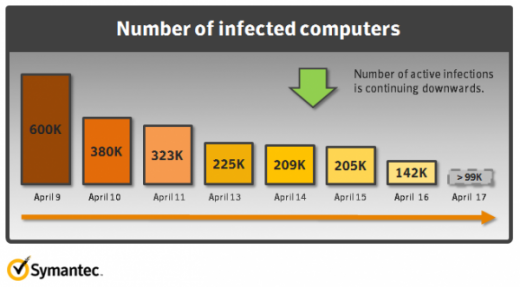
According to a post on the Symantec security blog, Apple’s attempts to get rid of the Java-based Flashback malware that affected 600,000 computers haven’t solved the problem completely.
As of today, Symanetec reports that 140,000 machines are still affected by the vulnerability. Our own Matthew Panzarino described the Flashback malware last week:
The Flashback program installs on an un-patched machine and attempts to harvest web browsing activity, usernames and passwords. It then sends that information to its network of computers across the internet. It is what’s known as a ‘drive-by’ infection because it can install itself on your machine after just a visit to an infected page, without any administrator passwords or installation procedures necessary.
Needless to say, this is a nasty attack that has affected a lot of users. There’s no way to know how much information has been collected about users who visited an infected page.
The fix that Apple released last week for users on OS X Lion plugged the hole that affects users who have Java installed. It’s suggested that you install this patch even if you don’t have Java on your machine, which is no longer a default with Lion.
This image from Symanetec shows that the latest tool from Apple is doing the job, but not as quickly as we had expected:
As we pointed out last week, this only validates Apple’s choice to not ship its OS with Java installed by default.
Get the TNW newsletter
Get the most important tech news in your inbox each week.