Given their popularity, Apple’s iOS devices are constantly being probed for vulnerabilities, whether it be within the filesystem, kernel or their applications.
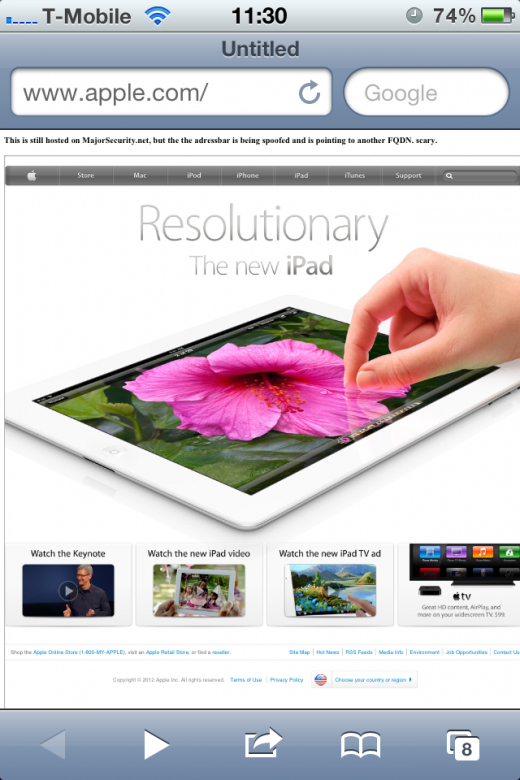
Today, a new vulnerability has been brought to our attention that focuses on how the Safari browser on iOS 5.1 renders website addresses, which can be used to display a different URL to that of the actual website you are visiting.
It was discovered by David Vieira-Kurz of MajorSecurity and the associated advisory details an error in how Safari handles the JavaScript window.open() method (which opens a new browser window). This could potentially be used to “trick users into supplying sensitive information to a malicious web site.”
The vulnerability has been reproduced on the iPhone 4, iPhone 4S, iPad 2 and new iPad running iOS 5.1. As a result, the Dutch Ministry of Security and Justice has issued a warning about it.
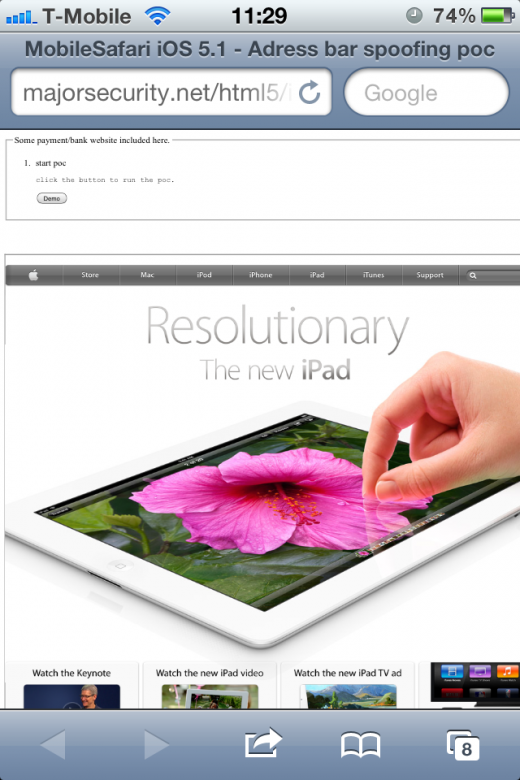
Viera-Kurz has offered a demonstration of the code, so if you own an iOS device and want to reproduce the bug, hit this link and then run push the ‘Demo’ button on the resulting page. A new website will be loaded in a new window but the address bar will still display apple.com.
Of course, you will need to access the link using your mobile device.
The vulnerability was identified in iOS 5.0 initially and then reproduced on March 1. Apple was notified the following day and acknowledged the bug on March 3. With Apple aware of the issue, it’s just a matter of time until Apple pushes a fix for the Webkit issue in its next iOS 5 update.
We also recommend that you don’t open any links that you don’t trust and be aware if any website asks for your personal details.
Get the TNW newsletter
Get the most important tech news in your inbox each week.