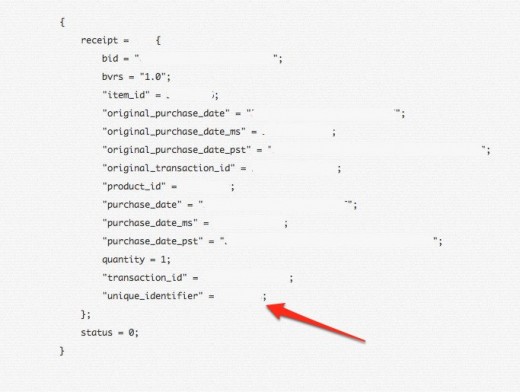
Apple has begun adding a new field to its in-app purchase receipts entitled ‘unique_identifier’. The addition of the field was reported by Macrumors, but contrary to its article, it does not appear to contain a Unique Device Identifier (UDID), something that Apple has been instructing developers to move away from. Update at bottom of post.
Instead, the field contains a unique string of numbers that could be any number of things ranging from a randomly generated value that is unique to a device, to a cryptographic hash of the UDID that accomplishes the same thing.
Either way, it’s hard to say at this point whether this has anything to do with the recent in-app purchase bypass, which has allowed over 8,460,017 free purchase transactions, according to stats provided by the hacker. It’s simply too early to say whether this is related to that, or to a particular new App Store feature for developers that Apple will launch with iOS 6.
Since the change, which Macrumors says developers noticed as of today, comes in close proximity to the hack, it’s definitely possible that the two are related, but this identifier won’t do anything to prevent the hack as it stands. Apps will have to be updated to check the value, first and foremost, but proactive receipt validation with Apple’s servers that checks agains the ‘unique_identifier’ value is the only way this is going to do anything real from preventing a hack like this from happening again.
That doesn’t mean, however, that Apple isn’t working to circumvent the hack. It has already taken action by blocking the first servers used to implement the bypass and released a statement saying “we take reports of fraudulent activity very seriously and we are investigating.”
If you’re a developer that has been using in-app purchase features in your apps, and you currently don’t validate against an external server, you might check out Beeblex, an encrypted plug-and-play solution for protecting in-app purchasing from exploits like the recent one.
Update: The source who contacted Macrumors also got in touch with us. They say that a UDID is definitely showing in that slot for them, but they also have not updated their app to remove references to the UDID, something that Apple has been recommending for some time. Developers that have been submitting app updates recently have found the apps being rejected for using the identifying string. This new use of an identifier may be Apple implementing its recommended UUID standard for new devices while still allowing apps running on older versions of the OS to use a UDID.
Get the TNW newsletter
Get the most important tech news in your inbox each week.