While users were struggling to use Gmail’s services yesterday for a long time, Google fixed a critical bug that might’ve let attackers send spoofed emails. It took Google a whopping 137 days to close the bug after security researcher Allison Husain first reported it to the company.
Husain noted that the bug didn’t allow classic email spoofing where you can put any value in the sender’s field. But it could mimic any Gmail or GSuite user to send emails. The bug could also let attackers bypass protection protocols such as Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting and Conformance (DMARC) that protect you from spoofing.
These techniques compare the sender’s IP address to a pre-approved list of IPs from the domain that is allowed to send emails. If the IP is not on the list, the spoofer’s jig is up, and the server rejects the email.
[Read: Most mobile apps suck — here’s how to fix them]
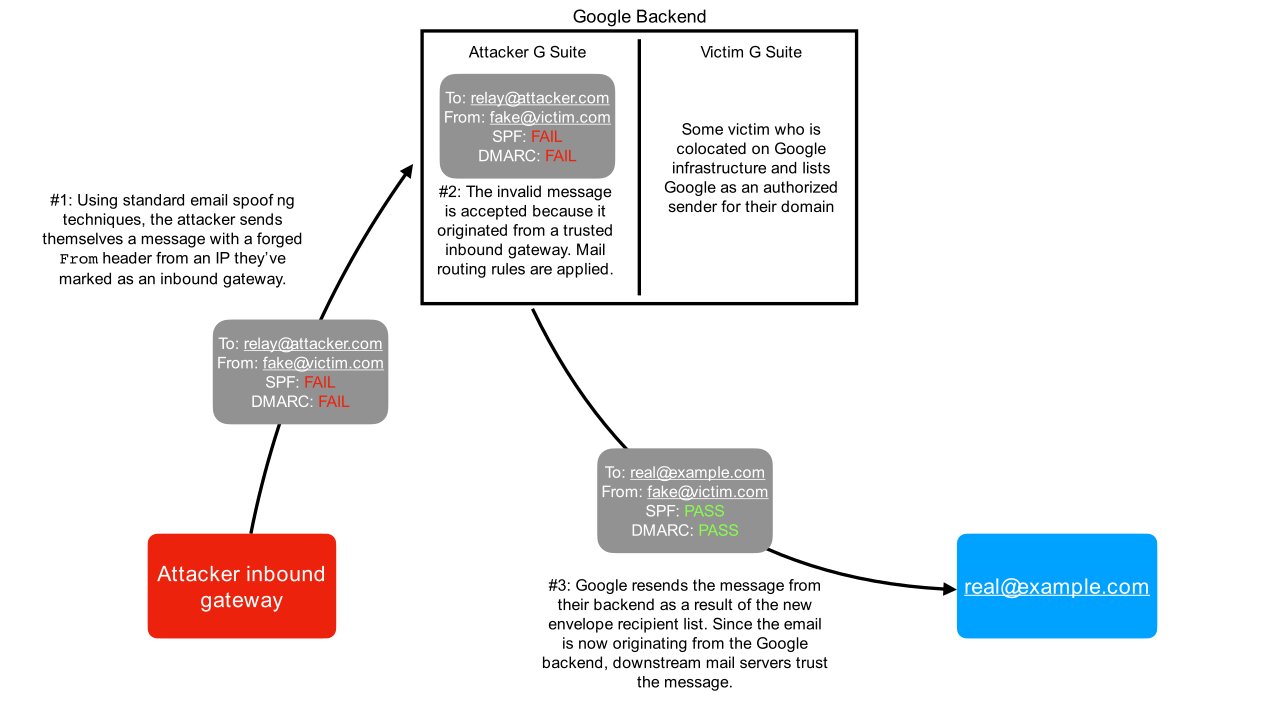
The bug worked in two phases. First, attackers would set up an “inbound gateway” through Gmail settings to one of their own email addresses (IPs). Usually, the inbound gateway’s role is to process all emails including archiving and filtering spam. Think of it as Gandalf, but for email. Because of this bug, attackers could allow spoofed emails from an IP (i.e., their original email address). Because of this, even if the original email failed the SPF and DMARC test, the spoofed email would end up in the attacker’s second inbox because the IP was put in the allowlist.
Once the email is in the attacker’s second G suite inbox, they could configure a random recipient through Gmail’s “Change envelope recipient” function. Plus, Gmail’s routing rules allow you to modify headers and subject lines. And since the email is going through Google’s own servers, it would pass all spoof detection tests. You can check out the flow of the attack in the diagram below.
Husain said that she notified Google about the bug in April, but the company only fixed it seven hours after the blog post was published
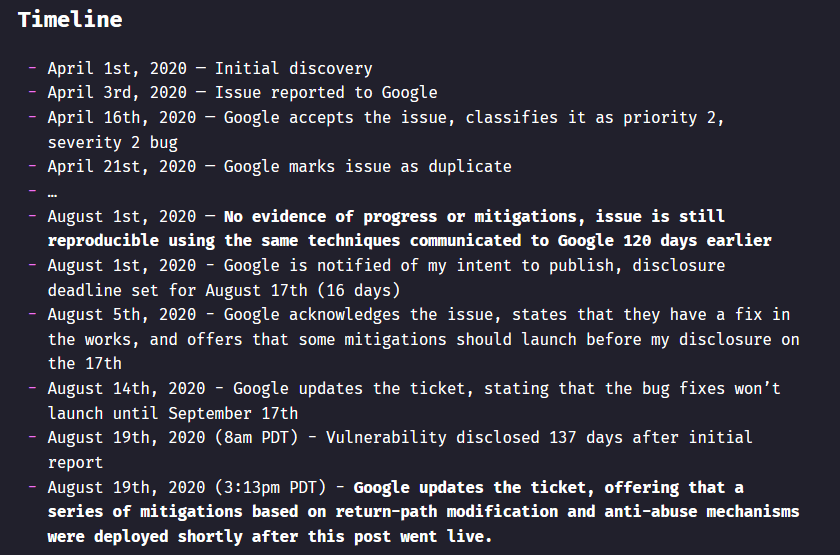
This was a very serious bug that could’ve been exploited by attackers or spammers to design targeted hacks. Google should’ve paid more attention to the bug and fixed it before it was disclosed.
Did you know we have an online event about ecommerce coming up? Join the Checkout track at TNW2020 to explore the latest retail tech innovations and best practices.
Get the TNW newsletter
Get the most important tech news in your inbox each week.