The personal records of PayMyTab customers have been left exposed online due to an unsecured Amazon data storage bucket.
According to cybersecurity company vpnMentor, the database was brought to its attention via Helen Foster, a partner at Davis Wright Tremain, who shared the findings exclusively with TNW.
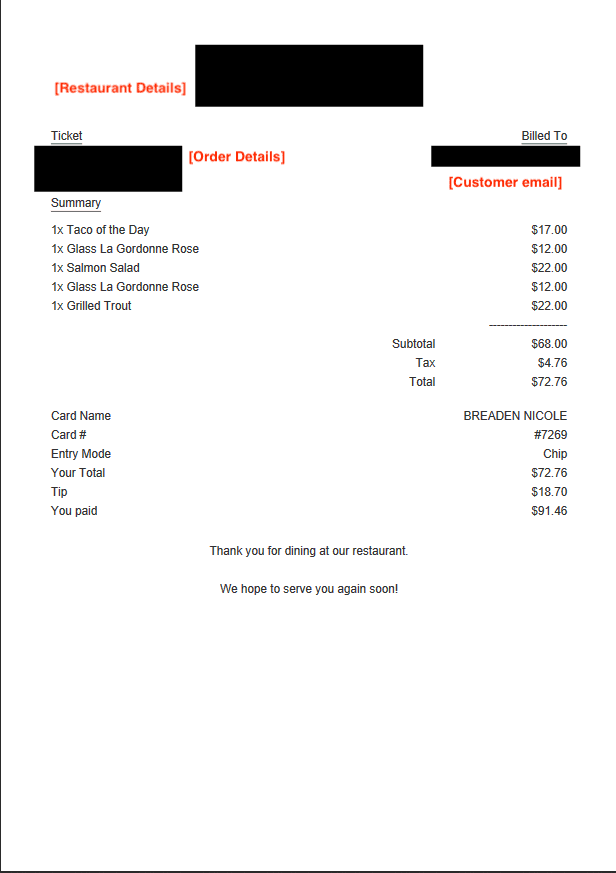
PayMyTab — an at-table payment system — is a mobile app and device that enables diners to settle their checks using their secure EMV chip-enabled credit card. It also enables guests to split the bill and pay it, tip included, directly from their own phones.
The leaked personal information included the following details:
- Customer’s name
- Email address or cell telephone number
- Last 4 digits of the payment card number
- The meal items ordered
- The date, time, location, and the name of the restaurant visited
vpnMentor said it was alerted to the data leak on October 18, after which the researchers reached out to PayMyTab and Amazon to plug the security lapse on November 5.
As a result, any customer who used PayMyTab to pay for their meals between July 2, 2018 to early November of this year could have had the aforementioned details exposed this way.
We’ve reached out to PayMyTab for further details, and we’ll update the story if we hear back.
“The S3 bucket contained detailed records of any customer at a restaurant using PayMyTab, who had chosen to have their receipt emailed to them after a meal,” vpnMentor stated. “By providing their email address, they could view their receipt online from their email inbox.”
Over the years, Amazon’s Simple Storage Service (aka S3) has become a popular data storage solution that comes as part of Amazon Web Services (AWS) cloud hosting service. It’s also led to a spike in the number of security incidents where businesses have left S3 servers unintentionally exposed online, leaking private information in the process.
While the database storage bucket may have been secured now, the possibility that criminals could use the exposed customer information to stage a variety of spearphishing attacks still remains.
Businesses, for their part, need to protect their servers and implement proper access controls in place to prevent such attacks in the future. It’s worth pointing out that Amazon rolled out a new security feature to AWS account owners last year explicitly meant to avoid such accidental data exposures caused by the misconfiguration of S3 data storage buckets.
This is not the first time that vpnMentor has discovered databases and servers left wide-open to the public. The company has previously disclosed a massive data breach impacting Ecuadorian citizens, Chinese e-commerce firm Gearbest, and a hotel reservation system used by resorts to manage web bookings.
It goes without saying that database leaks of this kind have huge security ramifications, including providing hackers easy access to sensitive information, thereby serving as a springboard for mounting other kinds of phishing exploits.
Therefore, it’s crucial that you watch out for any suspcious emails, enable two-factor authentication, and not click any links that could trick you into revealing private or sensitive information.
Get the TNW newsletter
Get the most important tech news in your inbox each week.






