
Unless you’re purchasing a Pixel phone — which promises a stock user experience — pre-installed apps from Android handset manufacturers are a given. Turns out, they’re not only bloatware, but are also full of security flaws.
Researchers at Kryptowire have uncovered 146 security vulnerabilities in pre-installed apps across 29 Android OEMs (aka original equipment manufacturers), underscoring the vast scope of the problem.
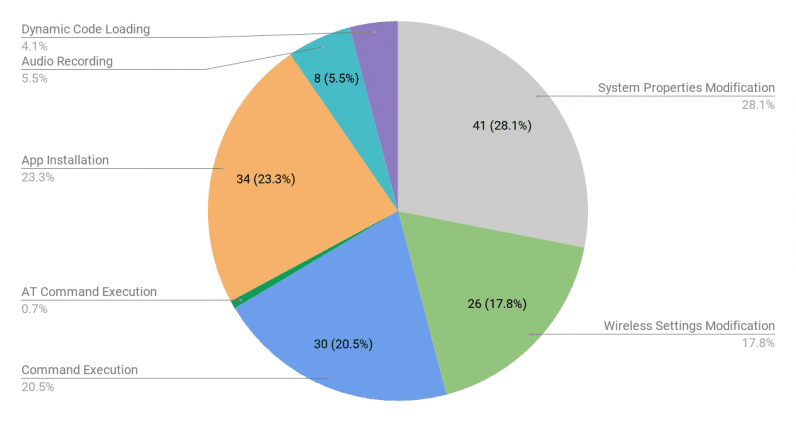
The shortcomings discovered in the study — funded by the Department of Homeland Security — range from unauthorized app installs to the ability to modify system and wireless settings, and even record audio.
More troubling, it includes apps from some well-known OEMs like Asus, Samsung, and Xiaomi.
Samsung disputed the findings in a statement to Wired, stating “we have promptly investigated the apps in question and have determined that appropriate protections are already in place.”
Since last year, Google has leveraged a system called Build Test Suite (BTS) to scan for potentially harmful pre-installed apps across custom Android builds for devices that ship with its services.
As the company explains in its “Android Security 2018 Year in Review” report released earlier this March:
OEMs submit their new or updated build images to BTS. BTS then runs a series of tests that look for security issues on the system image. One of these security tests scans for pre-installed PHAs included in the system image. If we find a PHA on the build, we work with the OEM partner to remediate and remove the PHA from the build before it can be offered to users.
But despite these security checks in place, questionable apps continue to slip through the cracks, as evidenced by Kryptowire’s research.
What makes the present situation more insidious is the fact that these are OEM apps. When third-party apps downloaded by users are found to contain malware, they can at least be removed from the infected phones.
With pre-installed apps, on the other hand, there is no option to get rid of the offended functionality. Worse, there’s no guarantee that OEMs will even issue a patch for older devices.
Google, for its part, has been actively tring to weed out harmful apps from the platform. It recently partnered with ESET, Lookout, and Zimperium to identify shady third-party apps before they end up on users’ devices.
Perhaps it’s time to apply the same stingent checks for OEM-made apps too.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





