
Healthcare providers are facing an unprecedented level of social engineering-driven malware threats, according to new research.
The findings — disclosed by California-based enterprise security solutions provider Proofpoint US — discovered at least 77 percent of email attacks on the medical sector during the first three months of 2019 involved the use of malicious links.
“URL-based attacks are effective because although users have grown more cautious about opening attachments, they still click URLs,” Proofpoint researchers said. “That’s especially true if the URL is that of a known, trusted source such as a file-sharing service. Attackers often use these services to host malware, linking to the malicious files in a URL.”
Just as malware and ransomware attacks are exposing sensitive data and preventing access to medical care, Proofpoint’s research highlights the need for securing hospital networks from malicious intrusions.
The rise of targeting phishing campaigns
The threats come in all forms, ranging from backdoors, credential stealers to targeted phishing campaigns aimed at “very attacked people” — including those who have public-facing contact details such as email addresses — that leave the door open for threat actors to access critical information.
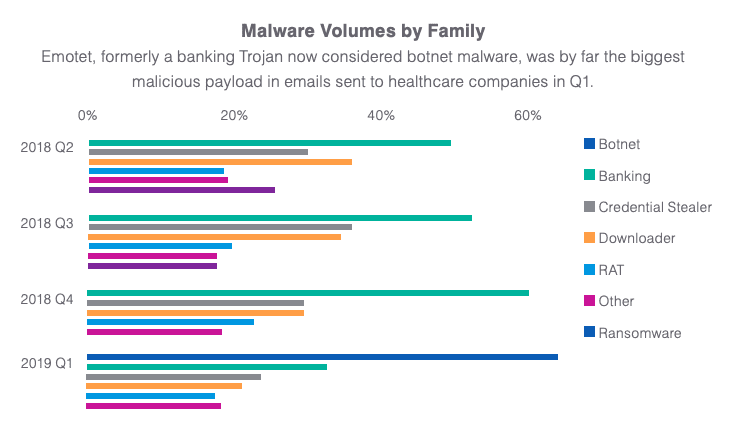
Emotet, a botnet-driven spam campaign, emerged as the biggest source of malware, morphing from its original roots as a banking Trojan to a “Swiss Army knife” that can serve as a downloader, information stealer, and spambot depending on how it’s deployed.
Ransomware threats, on the other hand, have fallen off from their 2017 highs, the report stated, citing volatility of the cryptocurrency market — which has become criminals’ preferred mode of payment in recent years — and increased security posture of organizations in response to such threats.
Notably, none of the 22 agencies involved in the Texas coordinated ransomware attack in August ended up paying the ransom despite the attackers demanding a collective $2.5 million from the agencies.
“The threat landscape is evolving to more carefully selected targets who have insurance and are likely to pay out,” Ryan Kalember, who leads cybersecurity strategy for Proofpoint, told TNW in a previous interaction.
Phishing messages, the other means of malware delivery, were found to masquerade as alerts from the US Centers for Disease Control and Prevention (CDC), increasing the likelihood that healthcare workers would open them right away.
Upon opening, the message triggered the installation of GandCrab ransomware, thereby encrypting important files in the system and asking for a ransom to decrypt them.
Although the operators behind the malware announced they were retiring in June, Secureworks Counter Threat Unit uncovered overlaps between GandCrab and a new form of ransomware called REvil (aka Sodinokibi). The connections were proved by McAfee last week in what the company says was a careful decision to retire GandCrab, in favor of REvil, to further the ransomware as a service (RaaS) offering.
It’s worth noting that REvil was the ransomware strain used in the attack on Texas municipalities as well as the onslaught against hundreds of dental offices in the US by compromising a third-party software vendor.
Other times, the impostor emails featured “payment” and “urgent” in the subject lines to grab attention, adding “the average impostor attack spoofed (posed as) 15 healthcare staff members on average across multiple messages.”
The need for improving security posture
It’s no surprise that hackers are constantly finding new ways to trick consumers into providing remote access to their computers in order to steal information. By combining sophisticated social engineering techniques with information already available about the target from other sources, the attacks have proven to be an easy vector to bypass security barriers.
“We’re living in a hyperconnected environment and healthcare systems are extremely prone to attacks,” Jonathan Langer, CEO of medical IoT platform Medigate, told TNW. “This necessitates hospitals to reassess their security infrastructure and design policies in order to address the security needs early on.”
Calling for a “people-centered approach to security,” the research recommends healthcare organizations to adopt security practices that takes into account the individual risk each user represents, including “how they’re targeted, what data they have access to, and whether they tend to fall prey to attacks.”
This also underscores the need for stopping social engineering attempts from reaching their targets’ inboxes and training people to spot mails that get through.
The fact that a market for medical data exists should incentivize healthcare institutions to invest more in data backups and auditing their security practices regularly; this would ensure critical systems aren’t open to abuse by threat actors.
“Segmentation based on digital assets is the key to combat cyber threats in hospitals, as is network isolation,” Langer told TNW. “With more medical devices connected to networks, it’s not just about protecting clinical data. It’s also about patient safety.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.





