Microsoft’s attempt to kill the password is going ahead with full steam.
The company has announced that Windows Hello, the passwordless authentication method that allows Windows 10 users to sign in to their devices using biometric information, is now a FIDO2 certified authenticator, joining the list of hardware-based security keys like Yubico’s YubiKey.
Passwordless authentication leverages the FIDO U2F (Universal 2nd Factor) open standard, making it easy for users of such hardware to seamlessly sign into online services and apps using Bluetooth, Near-field Communication (NFC) or USB. It was developed jointly by Google and Yubico, before it came to be overseen by the FIDO (Fast IDentity Online) alliance in 2013.
What makes the revamped Windows Hello login platform different is that it’s built into the massively popular Windows 10 operating system, thereby obviating the need for separate specialized hardware.
Last November, Microsoft took it a step ahead, adding capabilities to use Windows Hello or a FIDO2-compliant external authenticator to securely sign in to your Microsoft account on the web without having to use a password.
“No one likes passwords (except hackers),” wrote Yogesh Mehta, head of Microsoft’s crypto, identity and authentication team in Azure Core OS, in a blog post. “People don’t like passwords because we have to remember them. As a result, we often create passwords that are easy to guess – which makes them the first target for hackers trying to access your computer or network at work.”
The move is also expected to accelerate the transition towards a passwordless web, and comes months after Google Chrome, Mozilla Firefox, Microsoft Edge, and Opera all added support for WebAuthn — a key standard that defines the implementation specifics of authenticating users to web-based apps and services.
But how does it actually work?
In a typical scenario, when you are prompted to sign in to a service, you use a username (or email or phone number) and a password, both of which are sent over the web securely to the website that then verifies the username/password combination to ascertain your identity before letting you in.
The important aspect here is that once you have shared your credentials with the service, you have no control over what it does with the data, including if it stores them securely so that your personal information doesn’t get leaked in the event of a breach.
FIDO2 is different in that you won’t have to deal with passwords, and most importantly, trust the website with your credentials.
This is because it makes use of public key encryption (PKE) for authentication, which involves using a pair of cryptographic keys: a private key that’s a secret, and a public key that is widely disseminated.
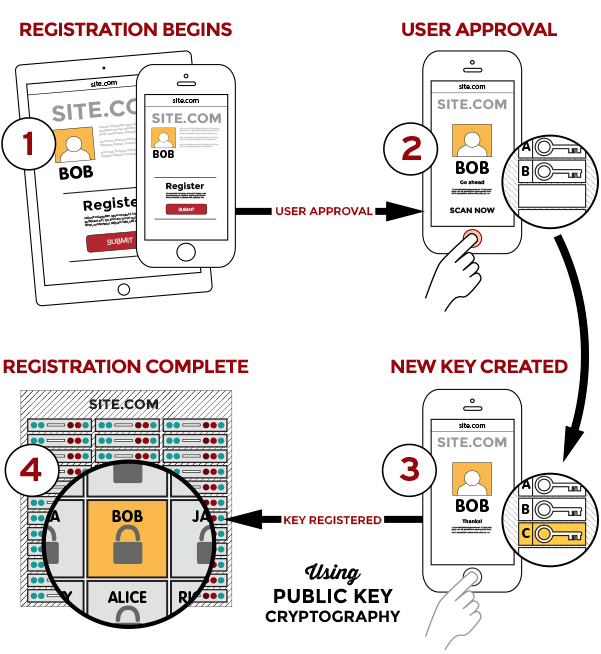
The idea behind PKE is as follows: if Alice is sending a message to Bob and doesn’t want anyone else to read its contents, she would encrypt the message with Bob’s public key. When Bob receives the encrypted message, he would use his private key to decrypt and read it.
Alternatively, it can also be used to verify your identity. In this scenario, Alice, the sender, encrypts the message with her private key and sends it to the recipient, who can then decrypt the message with Alice’s public key, hence confirming that the encrypted message came from her.
FIDO2 makes use of the second approach for authentication. So, when you attempt to sign up for a service, instead of presenting you with a regular login form where you enter your username and password, the website can authenticate you simply by using special JavaScript code embedded in its web page.
That special code adheres to the WebAuthn API standard, allowing your web browser to create and manage the cryptographic credentials required for signing you in to the website. In short, it’s nothing but a JavaScript-based password autofill, which also acts as middleman between the client (your browser) and the website’s web server.
How do you generate the keys?
This is where the authenticators come into picture. They can be either natively integrated into the OS, like Google’s Android (more details here) and the Windows Hello facial recognition system, or an external authenticator like YubiKey or even your smartphone.
But in order to support a wide range of authenticators, it’s also important that the makers agree to a common set of protocols regarding how the browsers and authenticators can talk to each other efficiently. These rules are collectively called CTAP (Client to Authenticator Protocol), and they enable your browser to communicate with external authenticators over a variety of methods like Bluetooth, NFC or USB.
So, when you are logging in to a website using Chrome or Firefox, the server sends over a challenge (generally a very large random number) and the JavaScript code in the login page uses the WebAuthn API to prompt your browser to encrypt the message using your private key. The browser, in turn, offloads the challenge to the authenticator, and the authenticator prompts for your permission to do so.
At this stage, you place your finger on the authenticator’s fingerprint scanner or get your face scanned (in case of Windows Hello). Once the authenticator confirms your biometric information, it encrypts the challenge using a private key and passes it back to the web browser, which passes it back to the website’s client-side JavaScript code, which then hands it back to the website’s server.
The server, now having received the encrypted message, successfully decrypts the challenge with the registered public key (refer image above) you provided when you signed up, thereby proving who you are.
What does it mean for you?
A passwordless authentication is a big win for security, and since no password is sent over the internet, there is no password to compromise either.
Although the technology behind it is a lot more complex than sending a simple username/password combination, you, as a user, have not had to remember or type a password. You proved your identity without revealing anything about you.
With platforms like Android and Windows 10 powering a combined billion active devices, the shift will lead to increased security for hundreds of millions of users. One can only hope that more systems will incorporate the standard in the future.
Get the TNW newsletter
Get the most important tech news in your inbox each week.