Passwords may not have been much of an annoyance back in the 1960s, when they were first believed to have been introduced to the world of computing. But as we’ve increasingly adopted a wide range of personal gadgets and online services, they’ve become a pain to manage, and a point of vulnerability that hackers can exploit when conditions are in their favor.
From what I’ve learned researching upcoming security measures, it looks like passwords aren’t going away anytime soon. For at least a few years into the future, we’ll continue to rely on them as a mode of authentication. But now for the good news: soon, you won’t need to bother with them quite as much as you do now.
Why can’t we get rid of passwords already?
Security expert Troy Hunt, who runs the well-known Have I Been Pwned? service that helps people determine if their online account details are out in the wild, told me, “We’re really not seeing anything that’s reducing the total number of them we still have. But over time, the prevalence with which we use passwords will change.”
It’s easy to imagine why. Passwords, for better and for worse, are human-readable, and are one of the easiest ways to authenticate users. They don’t require special hardware to let you key them in, and they allow for the simplest method for registering new users with online services, or for creating accounts for personal devices like phones and tablets.
The trouble is, they’re often stored insecurely by service providers, and people tend to use the same password for multiple services – which means that if one of your accounts’ credentials are exposed in a breach, a hacker could gain access to your other accounts with minimal effort.
To put in perspective the scale of the problem that passwords pose, consider the fact that billions of account credentials are stolen and leaked each year. And that, according to password management service Lastpass’ report from 2017 (PDF), business users of their service each have 191 online accounts to their name on average.
Can we make authentication suck less?
The way out of this hell – in which we frantically mash up our pets’ names with the year of our birth and some random special characters every time we want to use a new service or device – actually involves using additional ways to confirm our identities.
The idea of multi-factor authentication isn’t at all new; you might already be using such systems for your social networks, email, or work accounts. But the future will see a significantly wider adoption of these methods, and less friction when it comes to using them. The end result: fewer accounts compromised every time there’s a security breach.
What’s multi-factor authentication like?
One of the most popular methods of multi-factor authentication over the past couple of decades involves using a hardware token that lives on your keychain and displays a numerical passcode, which changes every few seconds in sync with a server. When you need to login to an account, you enter your username along with the passcode displayed on your token before the clock runs out.
Today, we have mobile apps that replicate this functionality, in the form of Authy, Google Authenticator, and Microsoft Authenticator. Some services generate and send you a one-time password (OTP) over SMS or via email – which is good for a single use within a certain period of time (say, an hour or 24 hours) – that you can use in lieu of a password that you need to remember.

Some online services, including Google and Yahoo’s suite of email and productivity tools, offer Account Keys, which basically have you enter your username and password as usual on a device, then confirm that it’s really you by responding to a push notification on your phone.
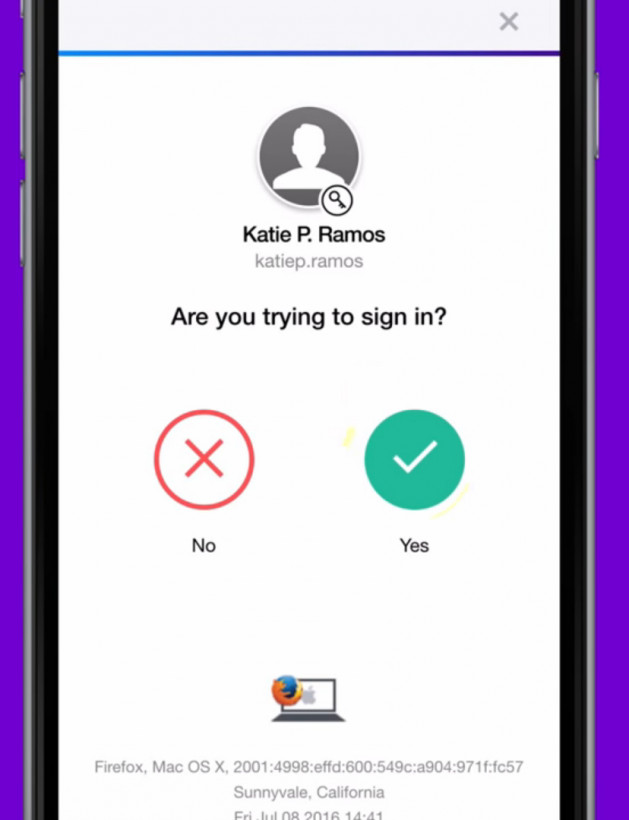
Want to go further? You can consider using an implementation of the Universal 2nd Factor authentication (U2F) standard, which requires you to connect a secure hardware key into your device to log you in. The keys are basically USB sticks – or contactless Bluetooth/NFC-capable tokens – for your phone or computer, and they can be configured to securely log you into multiple accounts, as long as the services you use support it.

The U2F open standard was initially developed by Google and California-based Yubico; it’s now managed by the FIDO Alliance. While various companies make U2F keys, Yubico’s offerings are the most popular on the market. You can get keys that connect via standard USB, USB-C, or Bluetooth and NFC if you’re looking for contactless solutions. You can also get keys that verify your identity by requiring a fingerprint before granting access.
Google recently launched an Advanced Protection Program for its users, which requires you to have two keys: a primary one that you’ll keep on hand for logging in wherever you go, and a backup in case you’re locked out. These keys together cost about $35-$45 per set, and Google’s service is free. Once you’ve signed up, you’ll need to use your keys to log in every time you want to access your account.
In the future…
We already use biometrics-based methods of authentication on our personal mobile devices to unlock them: fingerprint, iris, and facial recognition have all been around for a while now, and are increasingly becoming available even on low-cost products.
At the same time, it’s worth noting that they’re not exactly foolproof. It’s possible, in some instances, to trick fingerprint sensors and basic facial recognition systems. But Aman Khanna, VP Products, ThumbSignIn – a company that provides secure authentication solutions – notes that instead of doing away with biometrics, we’ll see the use of a combination of biometric authenticators:
From a security perspective, we expect to see the industry move in the direction of multi-mode biometrics, which combines identifiers like fingerprints, voice, face recognition, iris patterns, and gait analysis to produce high-reliability biometrics matching. Combining biometric factors in this manner can produce nearly flawless biometric matching that is hundreds of times more reliable than using a single factor.
The challenge is in making these authentication systems frictionless, so they provide security without all the fuss of physically proving we are who we say we are. In the next couple of years, we can safely assume that more services will require multi-factor authentication, and devices like U2F keys will become cheaper and more commonplace.
You can also expect to worry less about authenticating yourself in physical locations like offices and banks. Khanna noted:
“Silent authenticators” will become increasingly common and users will no longer be required to “present” their biometric identifiers. Instead, a number of biometric factors will be automatically captured on a continuous basis as needed by the systems being accessed. Machine learning algorithms will combine multiple “behavioral biometric” factors such as the way we type on our device, the way we walk (gait analysis) or our geolocation using environmental factors including signals from nearby Bluetooth devices and Wi-Fi networks.
Behavioral biometrics looks at digital end users – anyone accessing their account via PC, smartphone, tablet, etc. The data that the system collects is how the user interacts with the application: they way they hold and touch the device, the way they move the mouse or type. So it’s all digital. As a point of reference, many of the US credit card issuers have or are about to deploy the tech for online account opening: that’s when you apply for a credit card online. And, most of the UK top tier banks use the tech to verify it’s the real user in online and mobile banking. This resulted in a sharp decline of digital fraud in the UK since the tech got to be deployed by the local banks in 2016.
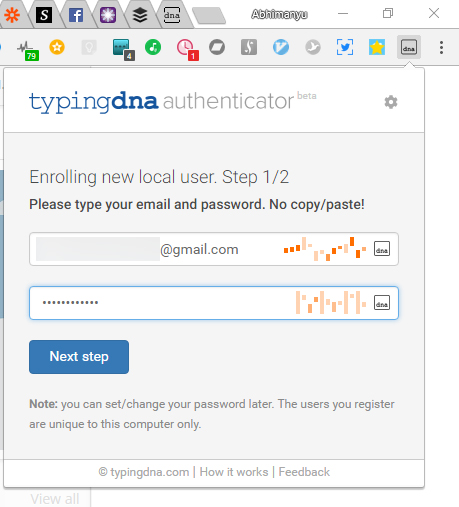
The behavioral biometrics magic at work here involves watching your typing pattern as you key in the password; if someone learns your password but enters it differently than the way you do (typing faster or slower, or making more mistakes than usual, for example), they won’t be able to access your account.
The future of authentication is about using more ways to convince machines that we are who we say we are. Hopefully, that will reduce our vulnerability to security breaches as well. Until then, your best bet is to use a combination of authentication factors wherever possible. Oh, and get a password manager too.
Get the TNW newsletter
Get the most important tech news in your inbox each week.






