
A Belgian security researcher has discovered a vulnerability on the website of Vatican News — the official news publication of the Holy See — that could allow anyone to publish their own fake news.
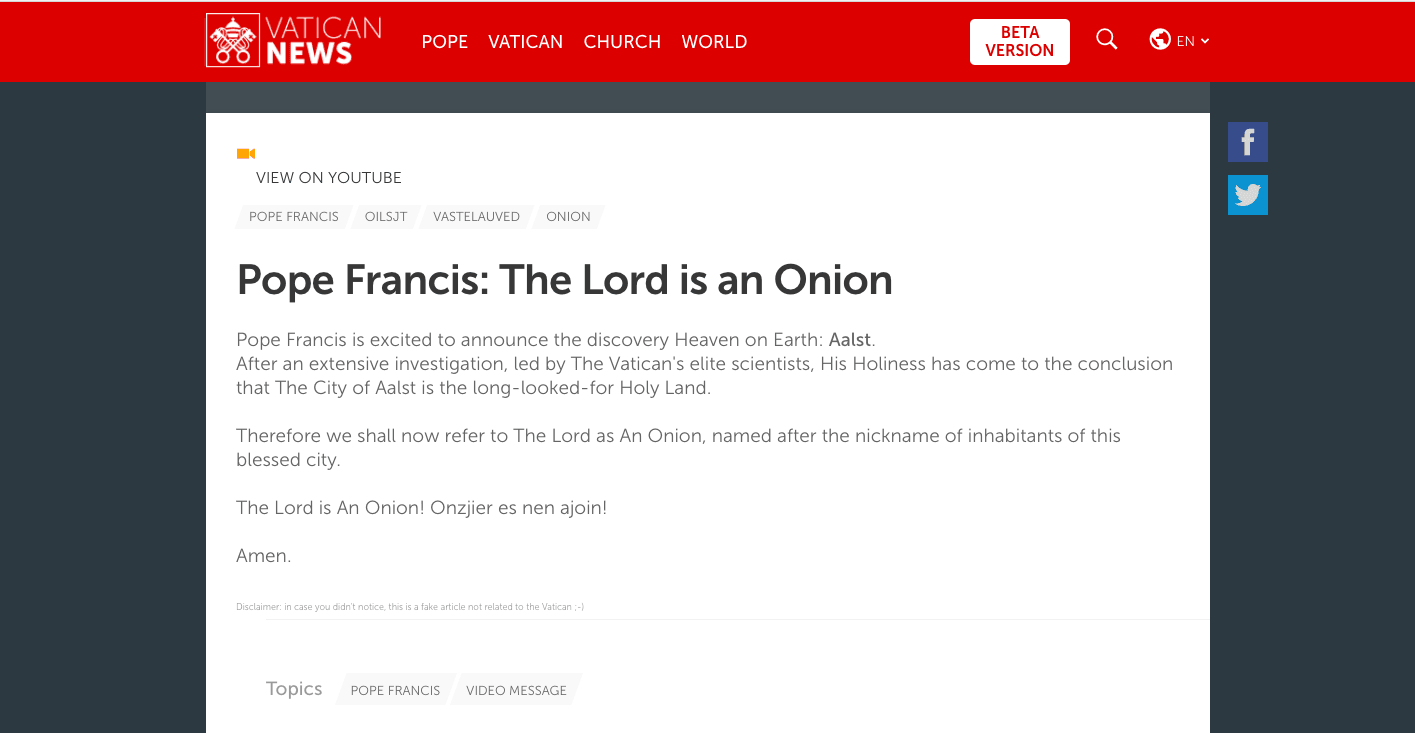
The vulnerability was discovered by independent researcher Inti De Ceukelaire. Proving his work, he tweeted a picture of Vatican News falsely stating that Pope Francis had declared God to be an onion.
GOD = AALSTENAAR. Niet mijn woorden, die van de paus. Merci, @Pontifex! ? ? LINK: https://t.co/GbOQrr2NJg (1/2) pic.twitter.com/FsvVeniycg
— Inti De Ceukelaire (@intidc) February 8, 2018
De Ceukelaire (who we’ve previously profiled) has been behind some high profile discoveries. In September, he disclosed ways to access corporate messaging apps like Slack and Yammer by exploiting publicly-accessible help-desks and bug trackers.
Last February, De Ceukelaire earned notoriety after he redirected several links in Donald Trump’s old tweets to content that would otherwise be embarrassing for the now-occupant of 1600 Pennsylvania Avenue. He did this by identifying websites Trump had tweeted out whose domain names had been allowed to expire. He then re-registered them under his own name.
I'll be speaking tomorrow at the San Jose Convention Center (CA) for the first- ever National Achievers Congress http://t.co/m4JN2oIw
— Donald J. Trump (@realDonaldTrump) April 11, 2012
Keeping with the Trump theme, he used publicly accessible online information to find the contact details of Melania Trump. He used this to invite FLOTUS to his home town.
In the case of Vatican News, De Ceukelaire encountered an unpatched cross site scripting (XSS) vulnerability, and exploited it to inject the blatantly fake news.
In the broadest sense, XSS is where an attacker injects their own code into a webpage. This gets rendered in the user’s browser, and can either fundamentally change the appearance of a page, or introduce undesired behavior.
So, if someone wanted to exploit an XSS attack to install some malware on a user’s computer, they could introduce a redirect in a legitimate page — like Vatican News — that takes people to another website. Then, it’s either a matter of social engineering the user into downloading something malicious, or exploiting a flaw in the browser to run a drive-by download.
De Ceukelaire didn’t want to do that. He just wanted to make a point about the importance of website security, while having a bit of fun. He succeeded.
XSS vulnerabilities fall into two categories: reflected and stored. In the case of stored XSS vulnerabilities, they’re saved somewhere — usually a database. With stored vulnerabilities, anyone who visits a particular page is hit.
Reflected XSS attacks are more ephemeral. Instead of being saved on the website, the injected code is often passed within the URL. To weaponize this, the attacker has to do more work. They have to actively share a particularly malicious link, which limits the damage.
In the case of Vatican News, De Ceukelaire found a reflected vulnerability. Although the issue continues to exist, no permanent damage has been done. If you go to Vatican News and search for “pope” and “onion,” you won’t find anything.
Speaking to TNW over email, De Ceukelaire said he’d warned Vatican News about the issue on nine separate occasions. Unfortunately, the publication failed to resolve the issue, and De Ceukelaire’s hand was forced. He had to disclose the issue.
For a bit of context, security researchers abide by something they call ethical disclosure practices. In a nutshell, it means that researchers give vendors and websites a reasonable chance to fix issues before they’re made embarassingly public.
But if a vendor fails to address an issue, the issue is disclosed publicly. The reason for this is twofold: firstly, it means people are in a position to make informed decisions about the software they use. It also puts a bit of fire underneath the vendor’s feet. As the bad press mounts, they’re motivated them to take action.
Because Vatican News failed to act, De Ceukelaire decided to disclose the issue through his Twitter account to his thousands of followers.
“I saw the Vatican had a new website a while ago. Whenever a huge website launches a new communication platform, I check it out. I want to see what technologies or software they’re using, how they follow design trends and whether they have innovative features. I don’t necessarily look for vulnerabilities, but this one was pretty obvious,” he explained.
De Ceukelaire says the webmaster of the Vatican News read his emails. He also said he would never publicly disclose a vulnerability that a vendor had shown interest in fixing. But the silence was deafening. His hand was forced.
“Two weeks ago, I told them that if they would not state they were going to fix this, I’d do responsible full disclosure. Not to harm them, but to show that fake news can easily be spread. Pope or not, you need to comply with security standards,” he argued.
Last month, Pope Francis declared fake news to be ‘satanic’ and condemned its use in politics. It’s not clear how he feels about security researchers pulling sophomoric pranks, however.
We reached out to Vatican News for comment. At the time of publication, they’re yet to reply. If that changes, we’ll let you know.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




