Sarahah, a ‘compliments’ app (think ask.fm) popular with teenagers, is reportedly rife with security issues, according to a UK researcher.
The issues pertain to the web version of the Sarahah service, and not the mobile application.
Scott Helme, the researcher who took a pop at the site, described Sarahah’s CSRF (cross site request forgery) protections as “fairly trivial to bypass.” CSRF is a highly dangerous form of attack, which could see a bad actor perform actions on the account of someone already logged in to the service. In this instance, Helme pointed out that an attacker could exploit this in order to force an account to favorite specific posts.
He also pointed out that in August, another researcher, Rony Das from Defencely, an Indian infosec consultancy firm, identified a stored XSS (cross site scripting) vulnerability, which could see an adversary upload content containing specially-formatted HTML and JavaScript, which would then be rendered and executed in the browser. Stored XSS attacks can be used to redirect users to other sites, which may contain malicious content, like viruses and spyware.
Helme identified serious issues with Sarahah’s security headers, which he says will prevent the site from using the HSTS (HTTP Strict Transport Security) protocol, which is an increasingly used tool to protect users from cookie hijacking and protocol downgrade attacks.
A focus of Helme’s research is on how the site filters content and protects its users. Its biggest rival, Ask.fm, has been dogged with allegations that the site is a haven for bullies, and Sarahah would be wise to learn from its mistakes.
Sarahah has a filtering system, which ostensibly discards posts depending on the words used. So, as pointed out by Helme, “I would kill for a cheeseburger right now” isn’t kosher, because of the word “kill.” However, if you put a period before “kill,” the post is shared without issue.
Amusingly, the word “script” is on Sarahah’s list of mal mots, presumably as a ham-fisted way to nullify any XSS attacks. This is terrible news for Sarahah members that are film studies majors, or fans of twee Irish pop band The Script. It’s also a pretty ineffective way to mitigate against XSS, as there are a myriad of ways to inject your own JavaScript without using the script tag. I really hope this isn’t the only countermeasure the site is taking.
Helme also discovered that Sarahah lacks any kind of rate limiting, allowing a user to send messages en-masse. He correctly points out that this is an issue from a safety and community standards point of view: first, because it means that a bully would be able to bombard a victim with an infinite number of harassing messages, just by writing a pretty basic script.
Sarahah also lacks a bulk delete function, forcing the victim to read — or at least look at — every harassing message they receive.
He also raised concerns with how the site handles password resets, and brute-force login attempts. These can be used in a way that can be construed as harassing. To reset a password, Sarahah only requires the email address associated with the account. The site will then auto-generate a new password, and email it to the user. This too isn’t rate-limited, and Helme pointed out that it’d be trivial to write a script that changes the password to an account every thirty seconds. This would not only fill the victim’s inbox, but it would make it harder for them to log in to their account.
The same script could be used to deny the user service to their account, by way of failed logins. After ten login fails, Sarahah locks the account for an apparently-random period of time. By bombarding the site with bad email-and-password combinations, an attacker can essentially prevent a user from gaining access to their account.
Following responsible disclosure best practices, Helme reached out to Sarahah several months ago, in order to inform them of these issues. After months of (what appears to be) following up and being given the run-around, he disclosed his findings publicly on his blog.
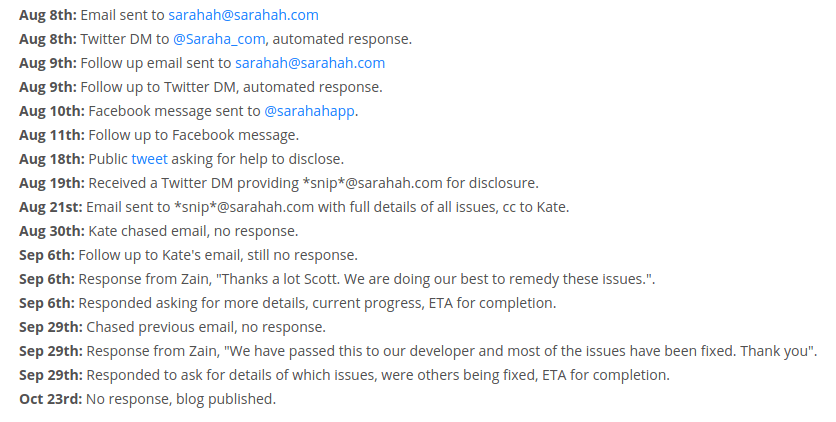
Over email, Scott Helme said that his biggest concern with the site is the ostensible lack of professionalism. “Given what I’ve found and how the vendor responded, I really wouldn’t use the service myself. Sarahah have not done close to enough to prove that they are a responsible service provider worthy of me trusting them with my communications,” he said.
For a brand new application I’d expect it to have been cutting edge with a good focus on security and privacy which is basically expected in the modern world. The issues I found simply shouldn’t exist in an app like this, the vendor response wasn’t great and I just don’t get a good overall feeling. Given that this is a private messaging service people could be trusting them with the secure delivery and storage of anything from mundane conversations to private, sensitive or intimate messages.
I’d like to see Sarahah provide information on how messages are protected during transmission and storage. A huge range of apps like WhatsApp, Facebook Messenger and Signal have put a massive focus on end-to-end (E2E) encryption and the privacy of their users, what steps are Sarahah taking? Can they read our messages? If they were breached could a hacker read our messages? Their lack of 2FA or 2SV is also an obvious opportunity for them to improve and better protect their users.
This isn’t the first time Sarahah has attracted the ire of the security community. A few months ago, the service was under fire after it was caught uploading the entire contacts list of its users for a feature that didn’t actually exist.
We’ve reached out to Sarahah, and if we hear back from them, we’ll update this post.
Get the TNW newsletter
Get the most important tech news in your inbox each week.