
Let’s imagine you’re the CEO of a major corporation. On a scale from one-to-ten, tell me how disastrous you think it would be if an adversary – like a hacker, or a rival company – was able to eavesdrop on every conversation taking place in your headquarters. Ten, right?
It’s a nightmare scenario, but it’s not out of the realm of possibility. Services like Slack and Yammer serve as the water coolers of today’s companies. One security researcher, Inti De Ceukelaire, has figured out how to gain access to company team pages, simply by exploiting faulty business logic in popular third-party online helpdesks.
And here’s the really scary part: It’s really difficult to fix.
Welcome to the team
Suppose it’s your first day at a new company, and your boss wants to on-board you onto its Slack workspace. This typically happens in one of two ways.
First, an administrator might manually send an email invitation to the user’s account. Alternatively, the administrator can permit anyone with an email address containing an approved domain name to create their own accounts.
This sounds impenetrable, right?
In the first example, the only way a bad actor can gain access to a Slack workspace is either by gaining access to the administrator’s account, or as the result of misconduct by the administrator.
And in the second example, the bad actor will have to somehow figure out how to create an email account with the company’s domain name. Provided it has its Gmail and Exchange dashboards on lock, that’s a non-starter, right?
Well, not quite.
Here’s the problem. Gaining an email with a corporate domain name isn’t as hard as you think, thanks to the existence of help desks and issue trackers.
Many of these provide users with a unique email address to write to, hosted under the company’s domain name. And while they’re unlikely to fool a human user (they often consist of random strings of numbers and letters), the likes of Slack are less fussy. They look at everything after the ‘@’ and say ‘yep, looks legit.’
De Ceukelaire created a project on Gitlab, and enabled the creation of issue tickets via email, which gave him a unique “@gitlab.com” email to correspond to. Messages sent to this address appear in the issue tracker within his project. He used this email to successfully register with the Slack team belonging to the devops giant.
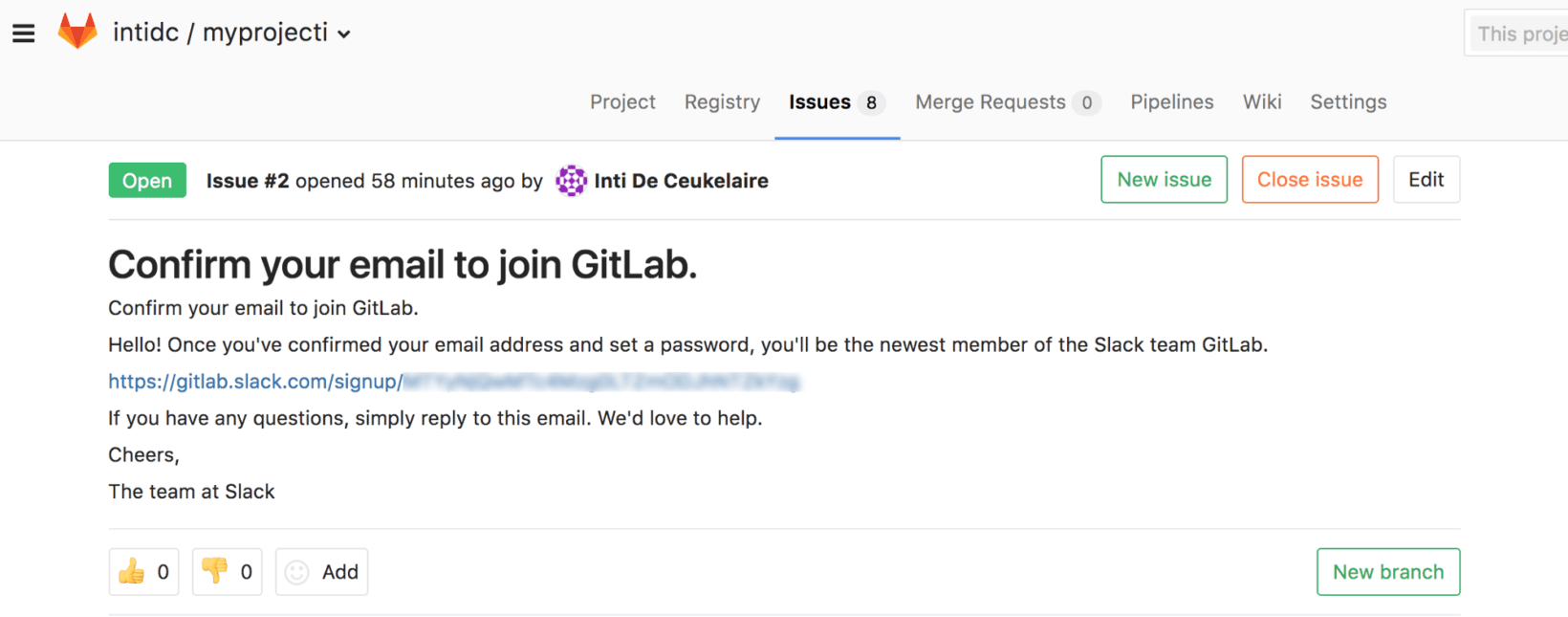
Following ethical disclosure practices, De Ceukelaire informed Gitlab, who quickly remedied the situation by making its Slack team invite-only.
Yes, it’s ironic that the very tools designed to help companies keep their customers satisfied and to identify bugs in their products are also a major security Achilles Heel.
Targeting the support desk
While many websites and online services have singular, dedicated support email addresses (like “support@example.com” thereby preventing the above attack), they rely on customer support software that is often flawed.
The biggest issue he found was a lack of user verification. Typically, when you sign up for something online, you are emailed with a link, which is used to confirm your email address. Although all the support software services De Ceukelaire tested did this (that said, he was able to bypass it in two cases), issues emerge when companies augment these packages with their own integrations. If a company introduces its own single-sign-on, but doesn’t verify the user, the helpdesk will think it’s a verified and legitimate email address.
In his words, this means that anyone could “sign up with any e-mail address and effectively read any support tickets created by that e-mail address ”
This is scarily dangerous. He knew that when you create a Slack account, emails come from feedback@slack.com. De Ceukelaire managed to access Vimeo’s support portal with that address, and subsequently create an account on Vimeo’s Slack team.
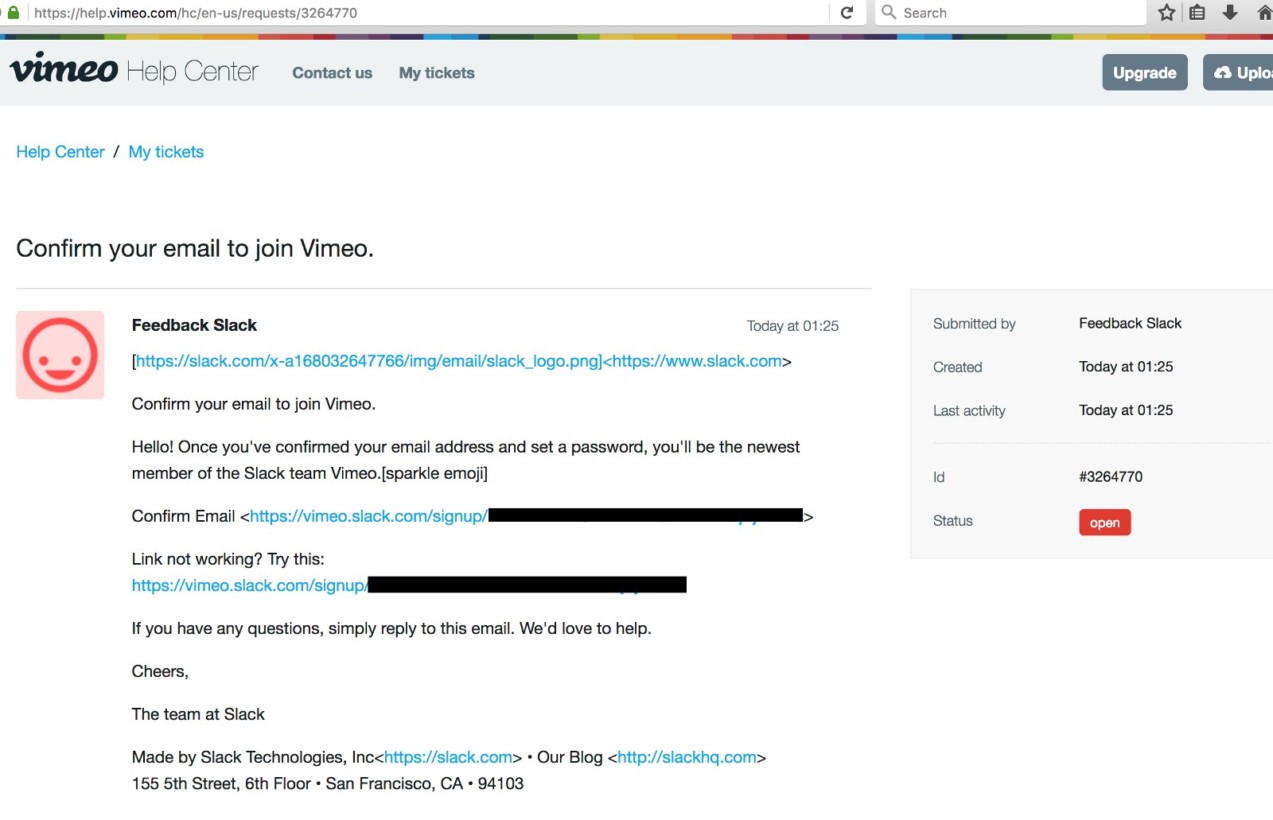
He later reported it to Vimeo, who promptly responded and issued him a $2,000 bug bounty reward.
Using the same method, De Ceukelaire identified several other services that might be vulnerable to the same kind of attack – not just Slack. He was able to create new Yammer team accounts, for example, and access Twitter password reset emails.
And as mentioned earlier, this isn’t an isolated issue. It’s something that’s endemic across the board. Half of all support desk applications examined contain the same basic flaw.
De Ceukelaire also found issues in two other support desk tools – Kayako and Zendesk – that would allow him to execute this attack, even when email verification was required.
Mitigating against the attack
Unfortunately, De Ceukelaire’s research suggests that it’s time to treat issue trackers and support software as an attack vector, ready to be exploited by an adversary.
So, how do we mitigate against it?
First, here’s the good news: Slack has created protections against the last kind of attack. It now sends emails with a random token (rather than feedback@slack.com). This is virtually impossible for an attacker to predict.
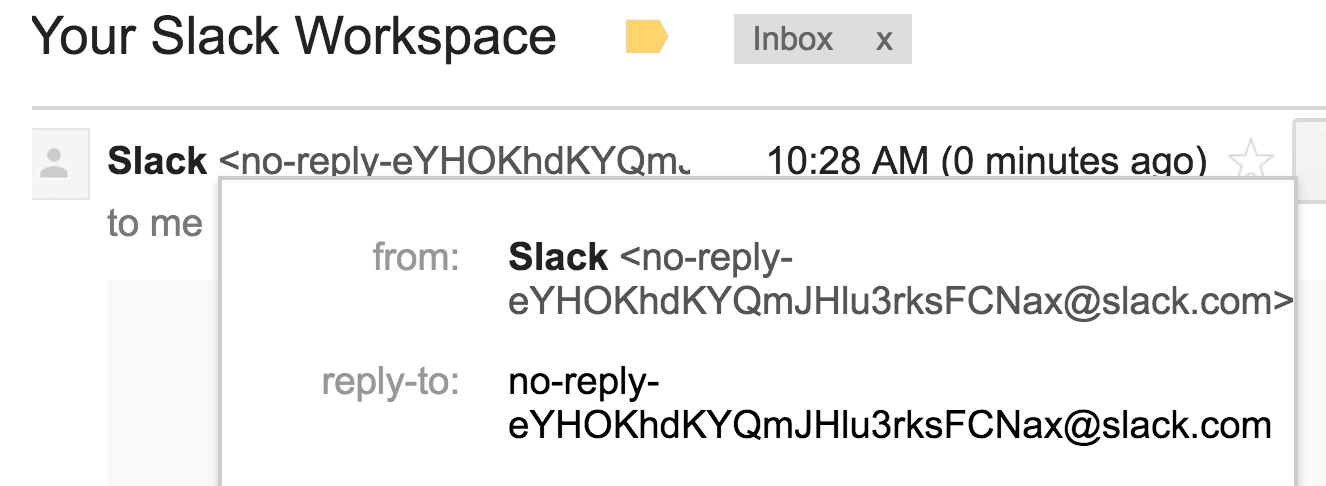
But it’s all downhill from there. Unfortunately, the first attack demonstrated still works.
Before we go forward, it’s worth mentioning that this isn’t the fault of Slack. While the popular messaging client features heavily in De Ceukelaire’s research, and indeed in this article, this is mostly due to its incumbent market position.
And to its credit, Slack took the initiative to tackle the problem. It also awarded De Ceukelaire a “critical severity bounty” for something that wasn’t its fault, but rather related to third-party services. The response from the Microsoft-owned Yammer, on the other hand, left a lot to be desired. Its response to De Ceukelaire was inadequate, and it has failed to take an proactive measures.
One potential solution to the first type of attack is for the likes of Slack to just look at email addresses, and refuse to create accounts for anything that looks suspect. If the first part of the address consists of 50 random letters, characters, and numbers, you can probably assume it wasn’t created by a human being.
Otherwise, the onus is on companies to secure their software properly. As demonstrated by Gitlab, who protected themselves by making their Slack team invite-only, the best approach is to move as much of the work to humans, rather than relying on automated processes.
Companies could also consider using different domain names for their email issue trackers. So, rather than giving literally anyone a “@gitlab.com,” address, why not use “@gitlab-issues.com” for correspondence?
This is something De Ceukelaire recommends, saying “companies like Airbnb, LinkedIn and GitHub provide e-mail addresses with a different domain, like @reply.linkedin.com or @mail.github.com. These cannot be used to sign up for services like Yammer or Slack.”
Wrapping up
This isn’t De Ceukelaire’s first rodeo. The veteran Belgian security researcher has previously showcased how to hijack links in old President Donald Trump’s tweets, and found the current FLOTUS’ email account with a bit of sleuthing.
This is in a different league, however. It involves software depended upon by businesses to communicate and collaborate. Gaining access to Slack, for example, gives you powers of surveillance that even the Stasi couldn’t have dreamed of.
And it’s still a problem. De Ceukelaire was forced to disclose the issue without contacting every customer, due to the sheer scale of the issue. It simply wouldn’t be possible to reach out to everyone.
That said, he feels companies and individuals should look at this issue with a sense of measured proportion. Speaking exclusively to TNW via email, De Ceukelaire said:
“It took me a while to disclose this issue because I didn’t really know what to do with it. I could keep it for myself and try to get as much money in bug bounty rewards as possible, but this wouldn’t benefit the community and wasn’t ethically the right thing to do. The more people that knew about this, the higher the chance it’d get exploited. So I worked with Slack in order to get prevent this at a higher level. It wasn’t exactly their fault that these vulnerabilities existed, but they did decide to act because of the widespread of the vulnerability. Thanks to some adjustments they made, it is no longer possible to execute this attack in an insecurely set up helpdesk environment. Some companies might still get hacked, but we did our best to reduce the risk.
Users shouldn’t be scared. Because the vulnerability requires an attacker to register an email address, only one person can execute it. I haven’t found a single case that indicated someone previously registered these email addresses. I’d remind companies of the importance of a solid authentication system. Because of the changes that were made to prevent this, only a small minority of companies should still be affected.”
I got in touch with Slack and Yammer. Slack declined to make a comment, while a Microsoft representative dismissed the threat to Yammer, saying: “The technique described is not a security vulnerability as it requires the attacker to first successfully compromise an account, prior to using the method described. We encourage customers to implement cybersecurity best practices to help protect against attacks. More information can be found at https://aka.ms/bm9atl.”
I also reached out to Vimeo and Gitlab. A Vimeo spokesperson said “Vimeo uses bug bounty programs like HackerOne to be proactive about security and fix vulnerabilities before they impact our business or customers. We have a security incident response policy in place that allows us to act immediately to vulnerabilities and awards appropriate bounties to those helping secure our systems.”
Brian Neel, security lead at GitLab, also spoke about the importance of engaging with the security community in order to secure its service. “We do this is by working with a bug bounty program to identify vulnerabilities within our platform and patch them before the situation escalates,” he said. “This is exactly what happened with the latest vulnerability within our Slack channel. Through HackerOne, we were immediately notified and able to take action to solve the problem by updating our Slack to invite-only and the reply-by-email documentation to better protect our internal channel.”
You can read about De Ceukelaire’s research here. And while you shouldn’t be dissuaded from using tools like Slack, it’s worth remembering that it just takes one domino to fall to set off a chain reaction, giving an attacker the keys to your kingdom.
Many thanks to Magali de Reu, who brought this to our attention. Read her interview with Inti here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





