
Apple retails its MacBooks at notoriously high rates, but hackers might have found a way to bend the system – and possibly bring the price down to a measly dollar.
Researchers from software security firm ERPScan have discovered a vulnerability in point-of-sale terminals developed by SAP and Oracle. If exploited, the flaw could grant attackers authorization to tap into the back-end system and tamper with prices and discounts for any item.
Meddling with this POS terminals, ERPScan’s Dmitry Chastuhin and Vladimir Egorov found that the system’s Xpress server suffered from a slew of missing authorization measures. What was particularly jarring about this is that, in addition to access to credit card data, it also enabled attackers to gain unfettered control over the server.
This includes the possibility to change prices and discount rates, as well as the ability to remotely start and shut down terminals.
“Broadly speaking, it’s not a problem of SAP. Many POS systems have similar architecture and thus same vulnerabilities,” said Chastuhin.
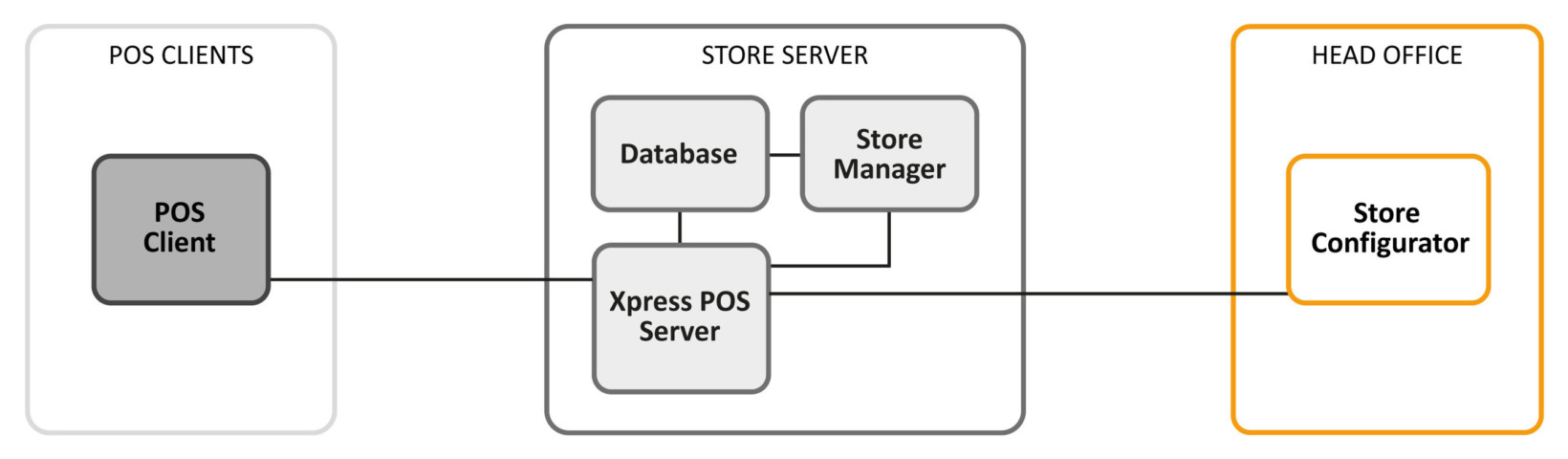
“The connections between POS workstation and the store server […] [often] lack the basics of cybersecurity – authorization procedures and encryption – and nobody cares about it. So, once an attacker is in the network, he or she gains full control of the system.”
Chastuhin and Egorov have since uploaded a proof-of-concept video to YouTube. In the clip, the researchers show how an attacker can use a $25 Raspberry Pi to acces the POS terminal backend and install malware designed to spoof the prices.
Here is the footage:
ERPScan first disclosed the vulnerability to SAP back in April this year. While the company released a patch for the bug in July, the researchers were able to exploit another flaw to perform the same attack. Following the second report, SAP has now successfully patched both vulnerabilities.
In case you happen to use SAP’s POS terminal solution, the researchers advise clients to “implement the appropriate patches (SAP Security Note 2476601 and SAP Security Note 2520064) as soon as possible to protect their business-critical assets.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.





