Videoconferencing is almost always terrible at the best of times, but can you imagine someone taking control of your screen during a meeting and sending inappropriate messages to the other attendees? Zoom patched this kind of vulnerability in the desktop app for its video chat service last week to save people from a conference call from hell.
A researcher named David Wells from a cybersecurity company Tenable discovered the bug in Zoom’s desktop app, which let an attacker take control of a user’s screen, send chat messages on their behalf, and kick people out of the meeting.
The company acted immediately after Wells reported the bug to them, and patched its server to guard users against any potential attack. It also released updates to its Windows, MacOS, and, Linux apps to fix the issue. However, users will have to update the app manually to protect themselves from being hijacked mid-call.
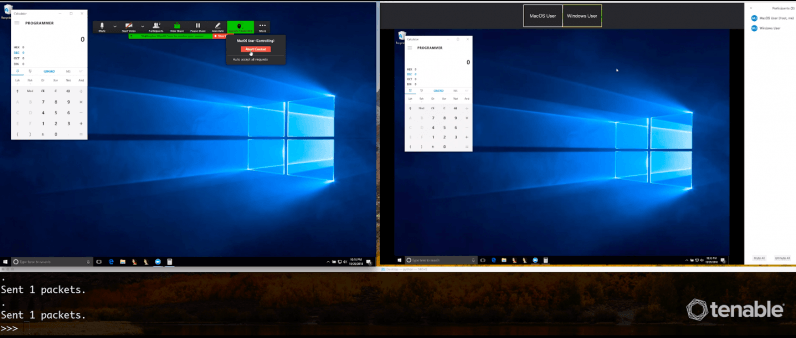
To take control of a Zoom user’s screen, an attacker would have to send commands through UDP (User Datagram Protocol) packets. Due to the bug, Zoom’s client software considered them legit and allowed the attacker to execute commands. After taking control of the screen, the hacker could potentially download malware on the user’s computer as well for other attacks.
Zoom’s website notes that over 750,000 companies use its solutions. That means that an attacker could have caused serious damage to a sizable organization. But thanks to an alert security researcher, the company avoided a major disaster.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





