
Security researchers have identified a flaw with older versions of the software updater Sparkle, used by certain iterations of Mac apps like uTorrent, Camtasia and Sketch that leaves them vulnerable to man-in-the-middle attacks.
Attackers can exploit the vulnerability in certain apps that use both the identified versions of Sparkle to send and receive updates, as well as an unencrypted HTTP channel, to install malicious code on your machine.
This would typically be done over an unsecured Wi-Fi network and the researchers found this is even the case if you’re using the latest version of Mac OS.
A confirmed list of vulnerable apps seen by Ars Technica includes Camtasia 2 v2.10.4, uTorrent v1.8.7, Sketch v3.5.1 and DuetDisplay v1.5.2.4, but one of the researchers said the numbers affected could be “huge.”
Although tens of Mac apps use Sparkle, those in question have to both use an old, vulnerable version (prior to v.1.13.1) as well loading assets over unencrypted HTTP.
For those with some tech know-how, a commentator has written a quick how-to to help you identify those apps that could be affected.
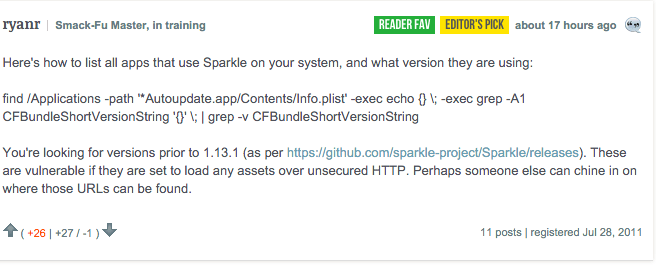
Essentially the app owners have to update the Sparkle software inside their app and work out how to use the secure HTTPS protocol instead of HTTP to fix the problem.
Just remember, no matter what people think, Macs can be hacked and third-party software can often be the weak link.
➤ “Huge” number of Mac apps vulnerable to hijacking, and a fix is elusive [Ars Technica]
Get the TNW newsletter
Get the most important tech news in your inbox each week.





