Yahoo Mail users are once again having their accounts compromised in attacks that are very similar to the ones seen just a few weeks ago. Attackers are gaining access after leveraging a flaw in the company’s YDN blog page by means of a link sent to victims’ inboxes.
This is part of a bigger story that deserves some background. Here’s the timeline so far.
On January 7, we wrote about the Yahoo Mail users having their accounts hacked after a lone hacker by the name of Shahin Ramezany, whose Twitter account has curiously gone silent, uploaded a video to YouTube demonstrating how to compromise a Yahoo account by leveraging a DOM-based cross-site scripting (XSS) vulnerability exploitable in all major browsers. The same day, Yahoo got back to TNW with two statements, first saying it is investigating and secondly confirming it fixed the flaw.
On January 8, researchers from Offensive Security let us know they had discovered that the vulnerability is still present, demonstrating a workaround showing they can still exploit the flaw in question. On January 11, Yahoo issued a third statement to TNW: “The cross-site scripting vulnerability that we identified on Friday was fixed the same day. We can confirm that we’ve now fixed the vulnerability on all versions of the site.”
On January 28 and January 30, two Yahoo users contacted me to say that their account was compromised via what they believed was the same way that was described in my previous articles. I went looking to see if anyone else had noticed and discovered that Bitdefender Labs has offered more details regarding this particular attack.
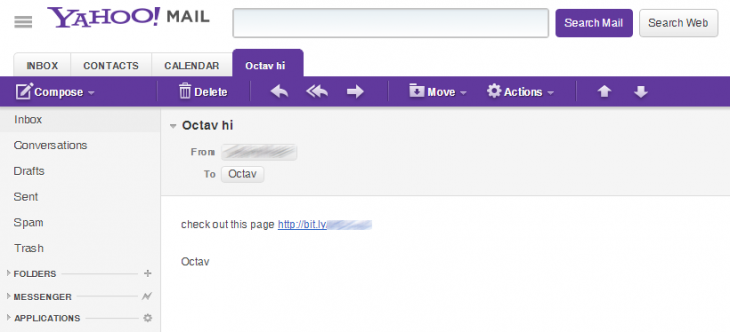
The security firm’s report is in line with what we’ve seen so far: it says the spam in question has been circulating for roughly a month and “is stealing Yahoo login credentials by exploiting an old – yet unpatched – vulnerability in a component of the Yahoo Developers blog.” The message features a simple “check out this page” message followed by a bit.ly shortened URL:
The link in question takes the user to a web page impersonating MSNBC, which is actually on a series of subdomains on com-im9.net. For the record, a WHOIS check shows the domain was bought in Ukraine and hosted in a data center in Nicosia, Cyprus.
Once the user is there, a piece of JavaScript code inside tries to exploit a known vulnerability (CVE-2012-3414) in the SWF Uploader component of Yahoo’s developer blog, which is powered by WordPress. This particular security flaw has reportedly been patched since WordPress version 3.3.2.
Bitdefender goes into more detail, but doesn’t reveal too much information since it says the security hole is still open:
Since the exploitable component is located on a sub-domain of the target website, the same-origin policy does not prevent the exploit code access to cookies, which are subsequently sent to the attacker. Once they have the log-in cookie, they can authenticate into the victim’s account and send spam or harvest contacts’ e-mail addresses for other spam campaigns. We believe this is the account recruitment stage of the operation and we expect the next wave of messages to feature links to malware.
In other words, once the attackers compromise your account, they send the same message to all your friends. If Yahoo’s latest statement from January 11 is to be believed, the company addressed the XSS flaw in question, just apparently not on its developer page.
We have once again contacted Yahoo about this issue (and so has Bitdefender, with proof-of-concept documentation). We will update this article if we hear back.
In the meantime, we recommend the same thing we did earlier this month. Users with a Yahoo account should make a point not to click on any suspicious links they receive by email or from anywhere else. In fact, that goes for all users; don’t click on random links, even if you get them from a friend. If you think your account has been compromised, also change your password on any related accounts, especially if you use the same one elsewhere.
Update at 5:30PM EST: Yahoo says is has fixed the problem. “Yahoo! takes security and our users’ data seriously,” a Yahoo spokesperson told TNW. “We recently learned of a vulnerability from an external security firm and confirm that we have fixed the vulnerability. We encourage concerned users to change their passwords to a strong password that combines letters, numbers, and symbols; and to enable the second login challenge in their account settings.”
Hopefully this particular saga is finally over.
Image credit: Justin Sullivan/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.