
Shadow IT is an issue that just about every organization faces on some level, but when I speak to executives and IT leaders, it’s simply not a topic that comes up. When I do bring it up, it quickly becomes clear that the tech industry as a whole underestimates the size and scope of the issue. And that lack of awareness and understanding is posing an ever-increasing threat to data protection and cybersecurity.
Some executives I speak with haven’t even heard the term “shadow IT,” which refers to systems, software, or applications that individuals in an organization use on a regular basis without the knowledge of executive leadership or the IT department. And when I tell them that recent research by the Everest Group found that upwards of 50 percent of technology spend in organizations lurks in the shadows, I can see their jaws drop. This means that half their budgets are being spent on software that teams, groups, and business units are purchasing (and using) without the IT department’s knowledge.
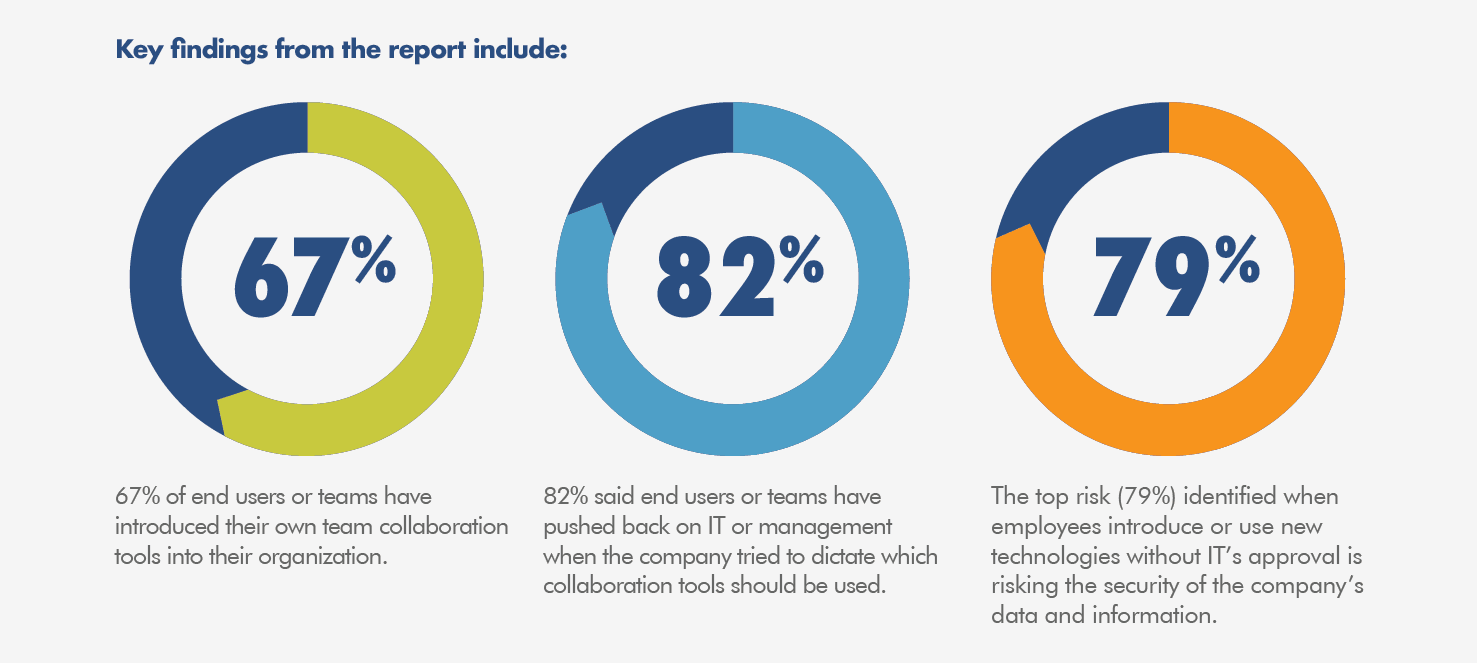
Collaboration tools represent an especially tricky category, with over two-thirds of teams telling Nexplane in a recent survey that they’ve implemented their own deployments without coordinating with IT. And some 82 percent have pushed back against IT’s attempts to implement a vetting process for collaboration tools.
While on the surface this might appear rather harmless – albeit wasteful and inefficient – I’ve grown increasingly vexed over the issue and am now bent on waking people up to the fact that shadow IT represents one of the biggest cybersecurity risks on the horizon.
The dangers are real, and enterprise companies need to tackle them appropriately.
More apps, more gaps
Anytime your IT department isn’t aware of various apps or software that are being used within your organization, the result is more potential security gaps and endpoint vulnerabilities that hackers and cyber criminals can potentially seek to exploit. IT departments I speak with know they can’t take measures to protect gaps that it doesn’t know exist, making the “app sprawl” phenomenon caused by shadow IT a major cybersecurity risk.
Moreover, PC-installed apps used in any shadow IT ecosystem will require updates and security patches at some point, and there’s no guarantee that employees using those apps will take the time and effort to do so, leaving critical data and systems at risk. Users of shadow IT apps may or may not be in compliance with any company-wide cybersecurity policy, and hackers are more than willing to use those apps as a gateway to other apps, systems, or databases.
And giving apps access to key assets can easily render your entire network vulnerable.
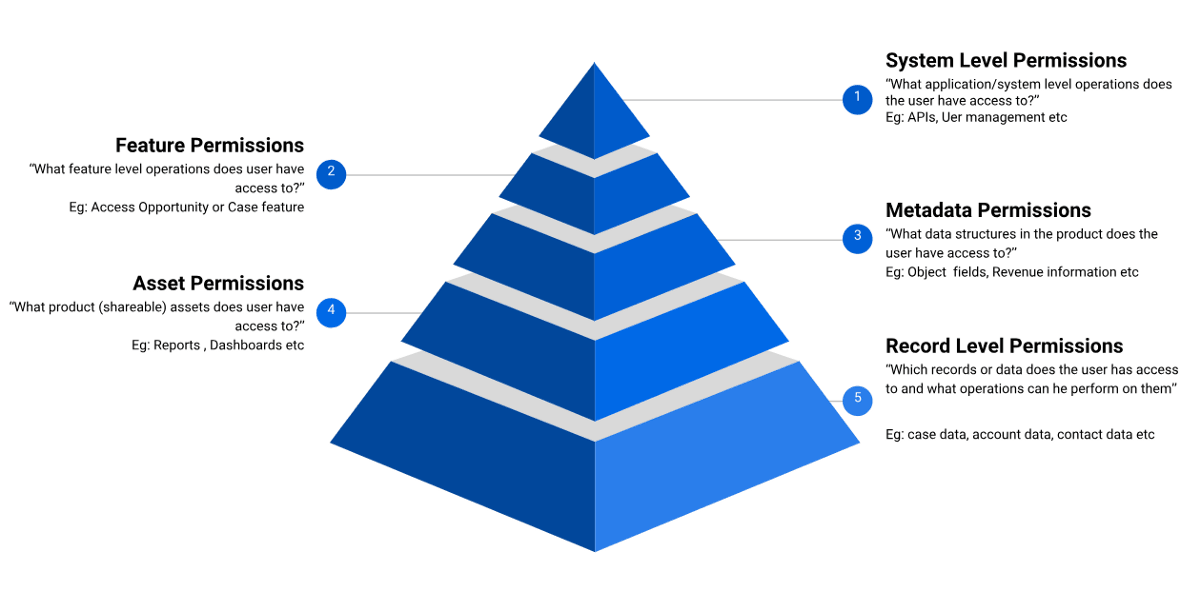
There’s also no monitoring the transition of access to key data stored in a shadow IT app should the employee change jobs. Because IT doesn’t know an employee has been using a separate CRM app to manage contacts, for example, it’s impossible to take normal protocols such as revoking access and changing passwords.
How shadow IT is exploited
In my experience, most employees who use shadow IT apps do so without intending to endanger their employers. They simply aren’t aware of the significant risks. To put the problem in perspective, IBM recently found that one out of three employees at Fortune 1000 companies regularly use cloud-based software-as-a-service (SaaS) apps that haven’t been explicitly approved by internal IT departments.
When I talk to IT leaders about the risks of employees using unapproved apps, I tell them that cybersecurity should be at the top of the list.
Employees might choose to store work-related files on their personal Dropbox, for instance, which might not have the same level of security settings as approved apps. And in the event of a breach, security administrators won’t be alerted as to the full potential scope of the threat, leaving the company unsure of what data has been compromised and when.
The use of shadow IT apps on smartphones and tablets is likewise problematic. When an employee stores confidential data on an unapproved app which they use on a mobile device, it creates a situation where data is constantly synchronized between a secured device (a work-issued laptop, for instance) and an unsecured device (i.e. personal smartphone). Indeed, we’re all guilty of glossing over the various permissions we grant our mobile apps.
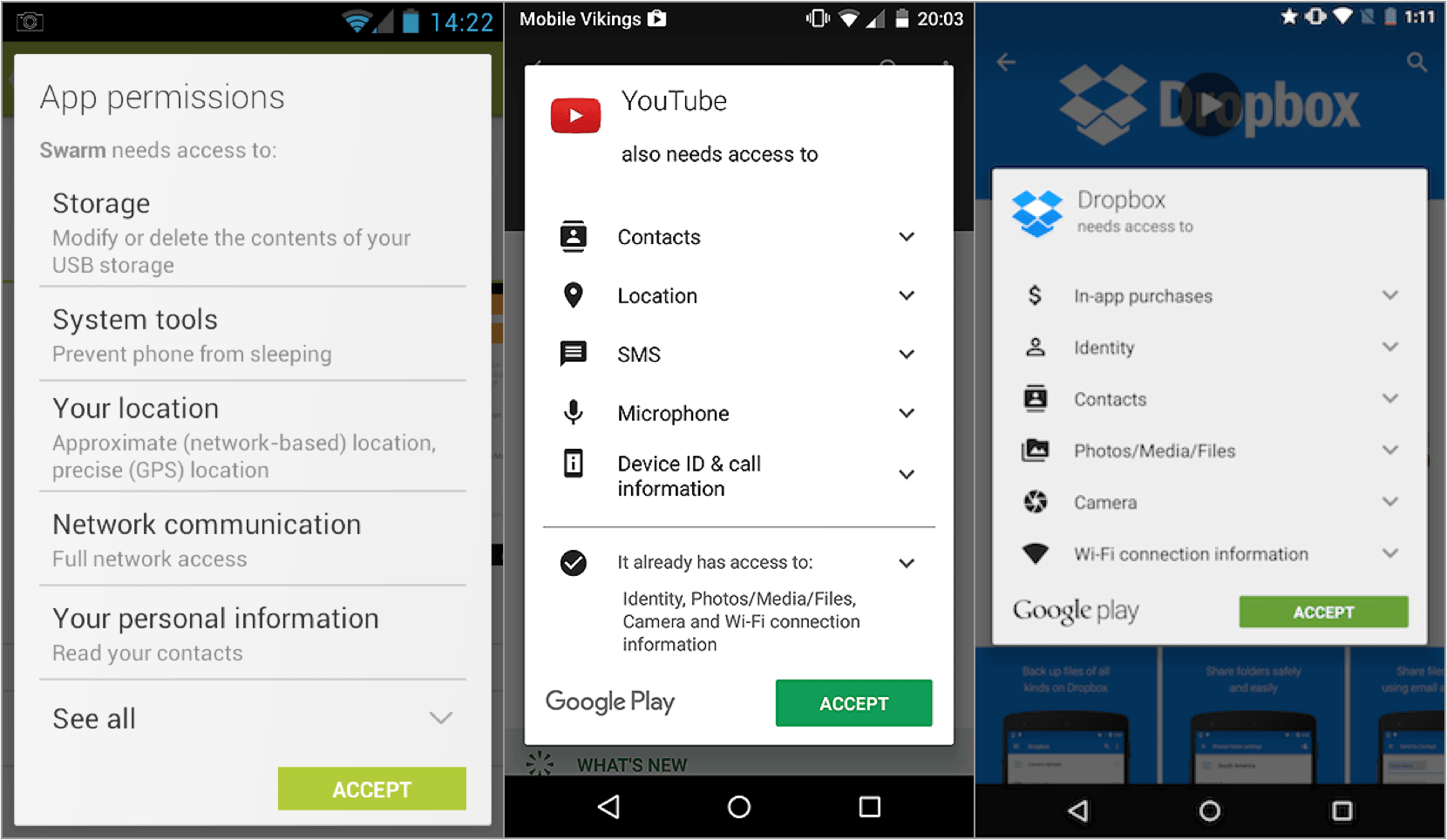
This presents an opportunity for hackers, should they gain access to the unsecured device through means such as WiFi hacking or a lost/stolen device. Unless companies have the means to wipe employees’ lost devices remotely (and few do), an experienced hacker can easily gain access to your unencrypted corporate data.
Tackling the shadow IT dilemma
Experts have been predicting for years that hackers, cybercriminals and other malicious actors are poised to ramp up their efforts in exploiting shadow IT vulnerabilities. That being said, there are measures, strategies, and tactics that I tell IT leaders to employ to help insulate themselves from the above risks and minimize the prevalence of shadow IT apps in their organizations to begin with.
First, the establishment of internal policies and procedures designed to educate employees about the dangers of shadow IT usage, and potentially establish penalties should they do so. This could cover areas from the use of third-party cloud storage services and USB devices to establishing procedures for handling company data on their mobile devices.
I recommend making sure all new employees are trained on these procedures, in addition to conducting refresher sessions on a regular basis.
The next thing is to compose an approved IT vendor list that all employees are aware of and have access to. If employees and managers would like to begin using an app not currently on the list, encourage them to submit that vendor to your IT department where you’ll be able to conduct proper vetting and configure the app with proper security protocols.
When onboarding a new vendor, formulate a breach notification plan in the agreement so that you’ll both be able to take swift action in the event of an actual cyber attack.
Finally, I’d recommend an audit of all current technical assets and capabilities to minimize risks presented by shadow IT usage. Any hardware used by employees should be tagged and be made traceable, when possible.
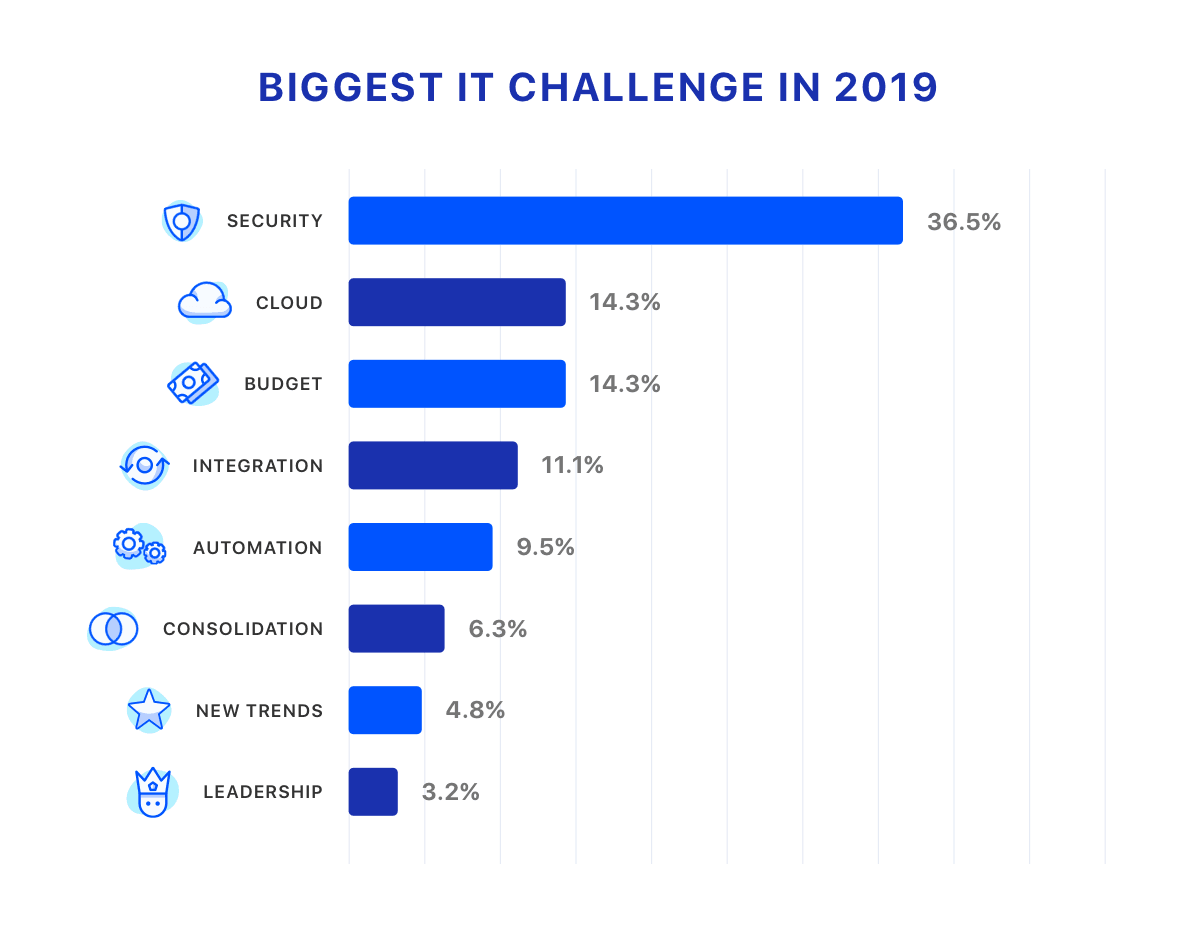
More importantly, take stock of apps that anyone in the organization is using to handle work-related data. Only 28 percent of IT leaders are actually using some kind of SaaS management tool to get the kind of visibility into shadow IT that’s necessary to adequately protect their data and systems, according to a recent survey from Torii. This despite IT leaders saying that security is their number one concern for 2019.
Closing thoughts
It’s time for everyone to wake up the cybersecurity threats that shadow IT usage presents. Shadow IT is the equivalent to a “silent killer” that makes critical data and systems vulnerable without executive or IT leaders knowing it.
The remedy is for organizations to familiarize themselves with the vulnerabilities typically associated with shadow IT, develop the right internal policies, and employ the right technologies to shed light on the potentially harmful unauthorized use of unapproved SaaS apps.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




