
US authorities have accused two Chinese nationals of laundering more than $100 million worth of stolen cryptocurrency for a hacking outfit linked to North Korea.
According to docs unsealed Monday, the US Treasury Department and the Department of Justice sanctioned and indicted Tian Yinyin and Li Jiadong, charging them with serving in an elaborate criminal network in support of the DPRK’s “cyber heist” program.
In total, police say the pair, who charged a fee for their services, successfully cashed out $34 million in Chinese yuan via bank accounts. They’re also said to have bought $1.4 million worth of Apple iTunes gift cards with stolen Bitcoin provided by the notorious Lazarus Group — the crew attributed to the hacking of Sony Pictures in 2014 and thought to be the most profitable cryptocurrency-stealing syndicate in the world.
[READ: North Korean hacker group Lazarus is using Telegram to steal cryptocurrency]
“The hacking of virtual currency exchanges and related money laundering for the benefit of North Korean actors poses a grave threat to the security and integrity of the global financial system,” said US attorney Timothy J. Shea.
An undisclosed portion of the laundered funds was allegedly used to pay for “infrastructure” used in North Korean hacking campaigns targeting the wider financial industry.
Cryptocurrency exchanges targeted with fake ID docs
Related press releases allege Yinyin and Jiadong attempted to cover their tracks by registering with cryptocurrency exchanges using doctored photographs and falsified identification documents.
Authorities identified 113 different cryptocurrency accounts and addresses used to wash the illicit digital assets between December 2017 and April 2019.
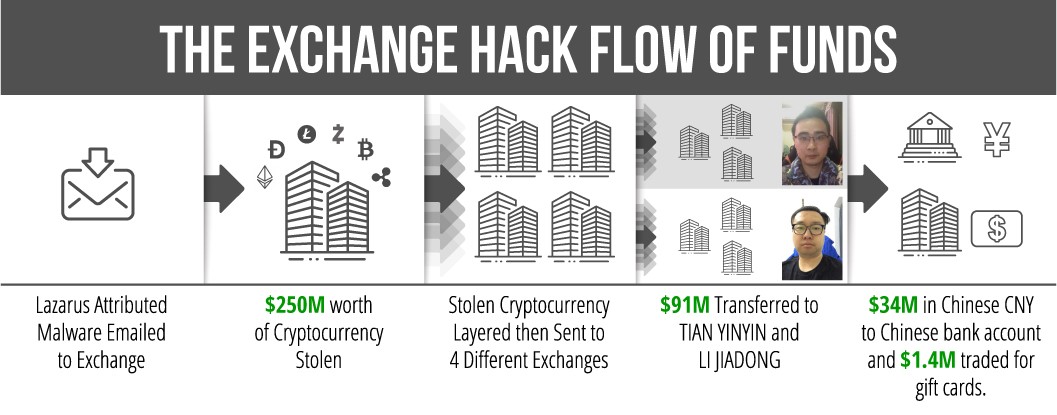
The US is seeking to recover the funds, which were worth $250 million at the time, having already seized some of it. “The defendants conducted business in the United States but at no time registered with the Financial Crimes Enforcement Network (FinCEN),” reads the DoJ’s statement.
Most of the funds laundered allegedly came by way of hacking cryptocurrency exchanges. Investigators found the duo received roughly $91 million stolen from a cryptocurrency exchange in April 2018, and $9.5 million from another exchange stolen at an undisclosed time.
Last year, Hard Fork reported on a new tactic employed by the Lazarus Group to infiltrate online exchanges: phishing staff with trojanized cryptocurrency trading software that allows unfettered access to private keys and other sensitive data. It appears this is the method used by the crew in the April 2018 hack.
Police also tied Yinyin and Jiadong to approximately $48.5 million in cryptocurrency stolen from a South Korea-based exchange in November 2019. That exchange is likely Upbit, which lost 342,000 ETH (worth $50 million at the time) to hackers in that month.
On top of these allegations, the US Treasury Department delisted two Russian firms — Independent Petroleum Company and one of its subsidiaries — for shipping more than $1 million worth of petroleum products to North Korea.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





