A new set of flaws discovered in the Intel Thunderbolt port has put millions of machines at risk of local hacking. This new research by Eindhoven University’s Björn Ruytenberg suggests that if a hacker gains access to a machine for just five minutes, they could bypass login methods to gain full data access.
Thunderbolt ports are present in machines with Windows, Linux, and macOS. So, that covers a lot of computers. Ruytenberg said all Thunderbolt versions and systems shipped between 2011 to 2020 are affected and no software patch can fix these vulnerabilities. So, Intel would need to redesign silicon in order to fix these flaws.
[Read: Small errors in coronavirus testing might lead to surprisingly big problems]
There’s not much you can do here. However, with open-source software called Thunderspy, developed by Ruytenberg and their team, you can check if you’re affected by the Thunderbolt bug.
These tools are available for Windows and Linux systems. Unfortunately, there’s no tool available for macOS users.
Windows
- Go to the Thunderspy website through your desktop browser and click on “Thunderspy for Windows” to download the tool.
- Right-click on the folder, and extract the Zip file to your preferred location.
- Double click on the Spycheck icon to run the tool.
- Select the language and accept the open-soruce GPLv3 license.
- Thunderspy tool will then try to detect the Thunderbolt controller on your system. During the process, the tool might ask you to install additional custom drivers or enter in power saving mode.
- After the inspection, Thunderspy will present an analysis summary. You can click on “Report” to get a more detailed report.
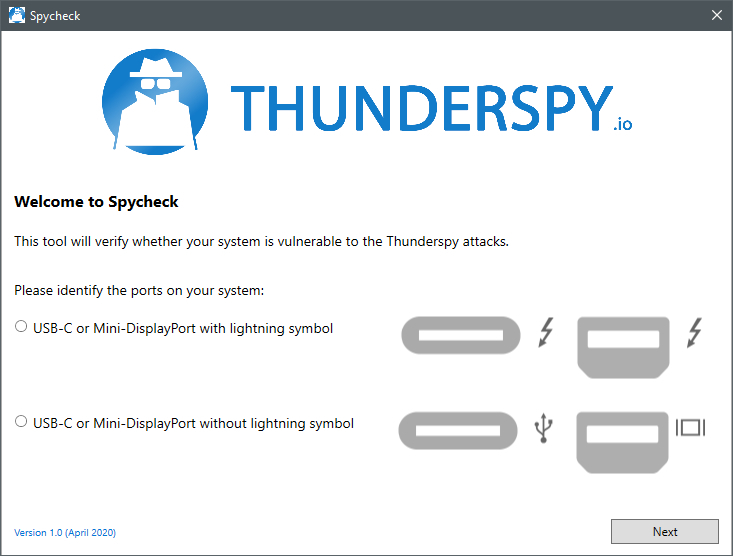
Linux
- Go to the Thunderspy website through your desktop browser and click on “Thunderspy for Linux” to download the tool.
- Open the command terminal, and run “$ sudo python3 spycheck.py” command.
- Please note that to run this command, you will need root privileges. To run the tool without root, simply remove ‘sudo’ from the above command.
- After you run the command, Spycheck will show you a detailed report. You can export the report to JSON through “-o FILE.json” command.
While you can’t do anything to patch these vulnerabilities, you shouldn’t use unknown Thunderbolt devices, or leave your computer unattended in public places. Hibernate or power off your system when you’re stepping away from it rather than putting it in sleep mode.
If you’re an advanced user or want to contribute to the Thunderspy tool, you can check its code on GitHub here. You can read Ruytenberg’s full research here. Intel also wrote a blog with recommendation for customers.
Get the TNW newsletter
Get the most important tech news in your inbox each week.