We’ve written before about China’s unique app store eco-system, which has seen hundreds of independent Android app stores sprout in response to the surge in sales of Android-powered phones and Google’s Play limited presence, and the vulnerabilities of the system have again been highlighted with the discovery of a new virus capable of making unauthorised payments, which is said to have affected more than half a million users already.
Following its discovery of another bill-racking virus, MMarketPlay, six weeks ago, anti-virus specialist TrustGo has identified sophisticated malware that is capable of making payments, accessing bank/card details and past payment and bill history.
Dubbed ‘Trojan!SMSZombie’, the virus was first identified on July 25 by the firm, which claims to be the first security specialist to locate it and offer a method to remove the malware — which ‘barricades’ itself onto infected devices.
 Infected apps have been located in GFan, one of China’s most prominent app stores, among other places and are said to have infected more than more than 500,000 users to date.
Infected apps have been located in GFan, one of China’s most prominent app stores, among other places and are said to have infected more than more than 500,000 users to date.
While that’s a drop in the ocean for China Mobile’s 683 million subscribers, it has the potential to make a large number of unauthorised transactions and cause trouble and annoyance for many.
The creators of the malware have been careful to avoid attention by giving users huge bills, and TrustGo says that, so far, they have recharged accounts for online gaming sites and other services by making “relatively low” deposits from infected phones.
In a post on its blog, TrustGo explains how the virus — which lurks in wallpaper apps and ‘activates’ post-download — quietly gains access to users’ SMS functionality before exploiting a vulnerability within China Mobile’s SMS payment gateway to carry out transactions and access data:
The SMSZombie virus has been hidden in a variety of wallpaper apps and attracts users with provocative titles and pictures. When the user sets the app as the device’s wallpaper, the app will request the user to install additional files associated with the virus. If the user agrees, the virus payload is delivered within a file called “Android System Service.”
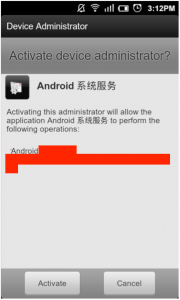
Once installed, the virus then tries to obtain administrator privileges on the user’s device. This step cannot be canceled by the user, as the “Cancel” button only reloads the dialog box until the user eventually is forced to select “Activate” to stop the dialog box. These privileges disable users’ ability to delete the app, causing the device to return to the home screen even after choosing to uninstall the app.
Given that many in China use SMS to make payments, it’s feared that access to these messages gives the malware’s makers details of bank cards and accounts:
Using a configuration file that can be updated by the malware maker at anytime, the malware can intercept and forward a variety of SMS messages. Because these messages often include banking and financial information, users accounts can easily be hacked further.
TrustGo says that infected users, and others concerned with being hit by Trojan!SMSZombie can to turn to its suite of Mobile Security apps — which scan phones for viruses in real-time — or visit its dedicated site which details how to remove the malware: trustgo.com/en/smszombie-eliminate.
The company is updating its apps to automatically handle the virus, and it anticipates that this functionality will be added with an app update that is scheduled for release before the end of the month.
“By waiting to deliver malicious code until after installation, this virus is difficult to detect. Sophisticated malware like this highlights the fact that the openness of the Android platform is a double-edged sword. Users are able to access an amazing breadth and variety of apps, but must take precautions to ensure the apps they want have not been compromised by hackers,” Li said.
Related news: Apple comments on text message spoofing, points out limitations of SMS and benefits of iMessage.
Get the TNW newsletter
Get the most important tech news in your inbox each week.