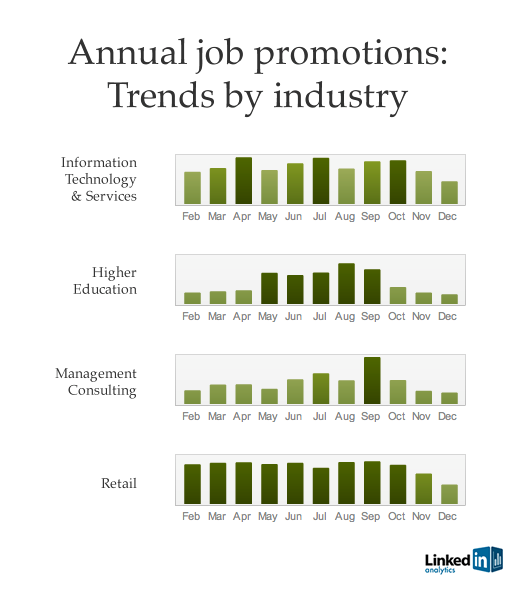
Okay, okay. Sony has had a lot to deal with of late, what with its Playstation network being hacked and subsequently being taken offline for quite some time. But we believe that Sony has been hacked yet again, this time its Sony Thailand’s website.
As security firm f-secure reports, Sony Thailand’s hdworld.sony.co.th URL has a phishing site running on it, leading to an Italian credit card company.
As you can see, visiting the site on Google Chrome reveals a blatant warning that the site is in fact a phishing scam:
The phishing site is in fact a sub-domain of Sony Thailand’s website, and it’s possible the hackers either have access to Sony Thailand’s DNS record or there could be a redirect in place on the servers itself, but we can’t be sure. We’ll update this as more information comes in and once we’ve spoken to a security consultant to learn how this could actually be possible.
Update
Okay, we’ve now spoken with Jobert Abma, an online security consultant from Online24. When asked how common this is, he said:
“It’s not as common as other vulnerabilities such as ‘usual’ web issues like data injection. But, when having mayor issues like file access, the success rate of such an attack becomes much higher.”
When asked how phishers actually carried out these hacks, Abma stated that the hackers simply looked for weaknesses in the application or infrastrucutre:
“It can be done through, for example, having file access. To grant such access, weaknesses in the application or infrastructure need to be found. As application issues, you’d mention database access to write files, including remote scripts, able to execute commands on the server and so on. As for weaknesses in an infrastructure, weak passwords or buffer overflows in software could be used to grant access.”
Following on from our chat with Jobert Abma, we spoke with Mikko H. Hyppönen from f-secure – the firm that found this latest hack. Hyppönen came across the site while investigating potential Playstation phishing scams. After confirming it was definitely a hack, Hyppönen gave his thoughts on how access was gained:
“If you have a large site with lots of legacy apps and mini-sites, it’s not unheard of for something like this to happen. In Sony’s case, it’s likely its a PHP or SQL hole rather than DNS access or htaccess edit on the server itself.”
Hyppönen also stated that this doesn’t necessarily mean that Sony.co.th or Sony.com got hacked, because the sub-domain in question may run on an external party’s server:
“I believe this particular site might run on some ad agency’s IP address. Nevertheless, it’s under Sony’s name, so technically, it’s Sony’s server.”
But it’s not just Sony that will suffer from this. It’s likely that part of the scam will involve spamming people with .it (Italy) email addresses whilst this phishing site is still live. And the hope for the scammers, of course, is they’ll hit someone who does hold the credit card in question.
So, not a good few weeks for Sony at all.
Get the TNW newsletter
Get the most important tech news in your inbox each week.