Almost everyone has had their social media accounts compromised at least once in the past, where their accounts automatically share scam links to friends and followers. Today’s attack on Buffer showed just how easy it is for a reputable company to cause its users to become victims of social media attacks, despite having done nothing wrong.
It’s hard to know what to do in these situations so we’ve prepared a primer on how you can deal with attacks if your social media account were to be compromised.
How to tell your account has been compromised
Sometimes it can be hard to tell that your account is compromised, especially if the attacker is only making small changes or sending out a message from time to time. Some common signs of your account being compromised are:
- Automated likes, favorites, follows/unfollows or friend requests
- Private messages being posted to your friends (this can be hard to spot unless someone points it out to you)
- Unexpected email/push notifications from the social network, such as warning that your email address has been changed
- Purchases appearing that you didn’t make or new games/apps being added
- Status updates/tweets that you didn’t make
- Changes to the profile or pictures on the account
Giving out your password
As a general rule of thumb you should never give your social media password to any website except the one it’s intended for. Applications that connect to Twitter should never directly ask for your password, instead they should ask you to sign in using the official website of the network you are using. Twitter and Facebook both use social sign on buttons that redirect to their login page for authentication, so that you don’t need to give your credentials to a third party.
Some attacks — known as phishing attempts — impersonate a website after you click on a compromised link (such as in a direct message or chat) and ask you to log in using a fake login screen. Once this is done, attackers are able to log in as you on the social network and change your information or share messages from your account.
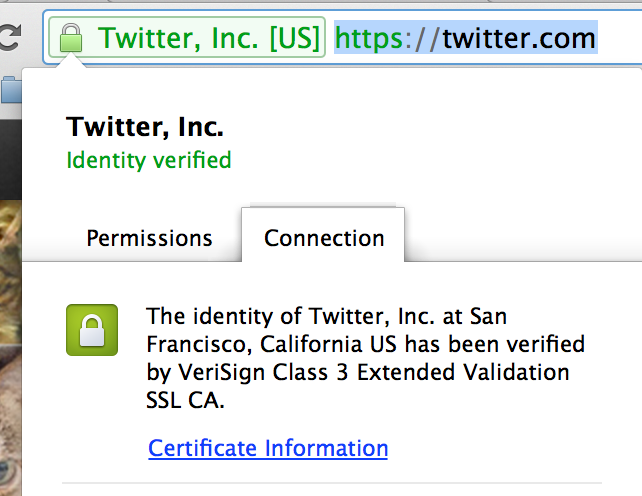
The best way to combat these is knowing if the site you’re visiting is the one you intended to visit. The easiest way is by checking the address bar in your browser matches the site you expected to visit, then checking if it also has a matching security certificate. If you were intending to visit Twitter and the URL is anything other than ‘Twitter.com,’ you should not enter your password as it will likely be used to compromise your account.
A common technique used to lure you to do this is when you receive a URL from a friend that is hidden behind a link shortening tool like Bit.ly. There are tools such as LongURL that allow you to expand that shortened URL to see what is hidden behind it before clicking. If you weren’t expecting a link or it looks suspicious using this method can be a good way to ensure it is legitimate.
Authenticating Apps
When you authenticate an application to your social media account you’re putting all your trust in someone else’s ability to manage your social network. Even if their intentions are good, sometimes things are out of their control and your account could be compromised. A good example of this is when Buffer — a social post scheduling tool — was hacked this week causing thousands of personal and corporate accounts to tweet weight loss tips.
There isn’t much users could do to prevent the kind of attack that happened with Buffer but it’s always worth ensuring the applications you are using are trustworthy and reviewing the approved list on a regular basis.
Many applications that promise more followers for free on Twitter actually end up spamming all your existing followers with links, for example, so ensure that what you are authenticating is well regarded before using it. Revoking applications you no longer use is a good way to prevent anything happening to your account before it happens.
What to do if your account is compromised
It can be hard to keep a cool head when your account gets a mind of its own but it’s easier to get back in control than you probably think. We recommend following these simple steps:
- Change your password immediately and make sure it is unique to the account you are using as well as your email address’ password to ensure access cannot be obtained via the reset password form of the website
- Visit the applications page of the social network and remove any apps you don’t recognize. If the account continues to behave erratically we recommend you revoke access to all applications.
- Ensure your email address is still set to the default of the account so that you’re able to sign in
- Run a virus scan on your PC to ensure you aren’t infected with a virus
- Contact the people your account has messaged to let them know that your account was compromised and that it wasn’t you sending the messages
Here’s a quick list of links to the applications pages of major social networks:
If it’s too late and you’ve completely lost control of your account there are a few ways that can work to get it back:
- Reset your password using the ‘forgot password’ link on the front page of the site
- Contact support via email or phone:
Other things you can do to prevent attack
There are a few other things you can do to prevent attacks on your account but they require some forward thinking and annoyance when you are logging in. The first of these is ensuring you always use unique passwords for each account and never share passwords across networks. This means if one account is compromised it’s not possible for attackers to gain access to your other ones as well.
Second, most social networks also now support something called two factor authentication. This is a system which requires both your password and a number generated by a device (such as your phone) to get access, which makes it almost impossible for an attacker to break into your account (unless they have a pre-authenticated application!).
Facebook, Google+ and Twitter all have their own versions of this: Facebook and Twitter will send an SMS to your phone with a number that you use to log in while Google uses an application on your phone to generate a number.
All in all, if you’re careful who you give the keys to your account to it can be easy to protect yourself online. It just requires a little forethought.
Photo credit: ra2studio/Shutterstock
Get the TNW newsletter
Get the most important tech news in your inbox each week.