Earlier this week, we warned you about a new piece of malware that is spreading via Skype using the message “lol is this your new profile pic?” It tries steals to steal your money using both ransomware (restricts access to your computer and demands payment for it to be removed) and click fraud (imitation of a legitimate user clicking on an ad to generate revenue).
Now we’ve learned that the malware does more than that: it targets your user accounts on various Web services and can also do so in many languages. Furthermore, it’s still spreading, and fast.
To recap, GFI detects the malware as Backdoor.Win32.Hupigon, Sophos detects it as Troj/Agent-YCW or Troj/Agent-YDC, and Trend Micro just calls it a variant of the Dorkbot worm (also known as NRGbot). Now two more security companies have jumped into the fray: Kaspersky detects the threat as Trojan.Win32.Bublik.jdb and Symantec classifies it as W32.IRCBot.NG.
Kaspersky further goes on to say that the malware steals user account information from the following services: 1and1, Alertpay, Brazzers, Dotster, eBay, Enom, Facebook, Godaddy, iknowthatgirl, Letitbit, Moniker, Namecheap, Netflix, PayPal, Sms4file, The Pirate Bay, Torrentleech, Twitter, Webnames, Whatcd, Vip-file, Yahoo, YouPorn, and many more. The security firm adds more:
The Trojan has an autorun functionality to spread via USB devices. It’s able to spread via MSN Messenger too and all locally saved Skype passwords on the same infected machine by switching automatically between available accounts.
Based on one of the malware’s Google short URLs (goo.gl), Kaspersky noted that the attack was likely launched first on October 6, but the original report from GFI was on October 5. This either comes down to a timezone dispute or just different URLs, as cybercriminals behind threats like this one can easily swap the message or URL in question. Either way, the malware first showed up last week, and the important part is that it’s still going strong.
How strong? As I wrote last week, in the space of 10 minutes, GFI recorded 2,259 transmissions. Symantec meanwhile says that in just two hours, the number of clicks grew up to 484,111 clicks. The total number of clicks has surpassed more than 1 million, for the aforementioned link. Symantec meanwhile thinks the threat is at over 2.5 million clicks, across at least eight different goo.gl URLs.
Symantec meanwhile tries to break down the steps of the attack:
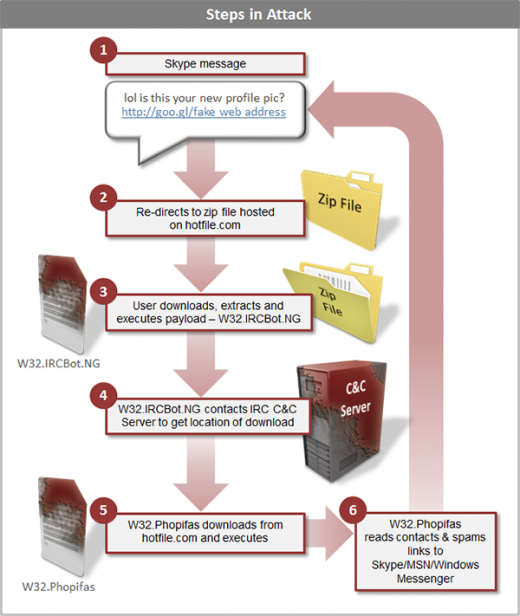
When the victim clicks on the goo.gl link they are redirected to a URL on Hotfile.com. The Hotfile.com site prompts the victim to download a .zip file which contains the malware W32.IRCBot.NG disguised as a legitimate instant messaging file. If the victim manually extracts the file and executes it, it contacts an IRC channel to receive commands. In our analysis we have observed the threat being commanded to download and execute another file from Hotfile.com. In each observed test it has been W32.Phopifas that is the second downloaded file, although it is possible that other malware may be downloaded depending on the victim’s geographical IP location.
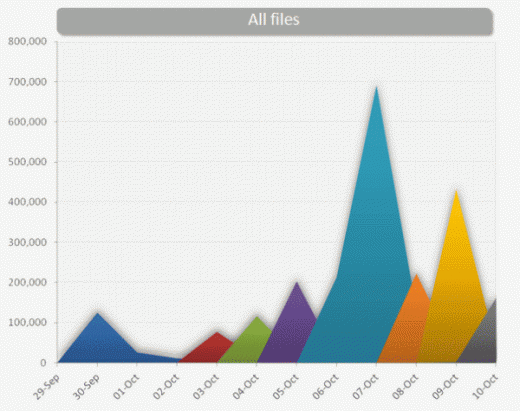
That doesn’t necessarily translate to infections, as of course many users have security solutions that stop the malware in its track. In fact, even when the original link is already dead, ignorant users still click on the shortened URL. Nevertheless, the takeaway here is the social engineering campaign is spreading very rapidly, and can quickly be adjusted. Here’s a graph from Symantec:
Along this same vein, the malware’s messages have been translated to more languages. Earlier this week Trend Micro said it was English and German. Now Kaspersky says it also speaks Latvian, Spanish, Portuguese, and Venezuelan. Symantec believes the malware supports over 30 different languages.
Curiously, most of the victims are in Russia, suggesting that may be where it was first sent out. Oh, and to add further to the internationalization, one of the variants tries to steal credit card information from an Ecuadorian bank.
Our suggestions remain the same for this malware: as a general word of caution, don’t click on links sent to you via Skype or any other instant messaging service. Furthermore, don’t download unknown archives and certainly don’t extract zip files to open files within, especially if you don’t know what they are.
Image credit: Christophe Libert
Get the TNW newsletter
Get the most important tech news in your inbox each week.