Up to this point, iOS users have been relatively safe from malware on their devices. Apple SVP Phil Schiller recently felt good enough about it to tweet a link to a report that put most of the onus of mobile malware on Android.
But researchers from security company Skycure say they’re concerned about a feature of iOS that could be used by malicious actors to read information, passwords and even encrypted data from devices without customers knowledge. They’ve detailed the new vulnerability in a presentation at the Herzliya Conference today and a company blog post.
It’s worth noting at the beginning that Skycure’s product, still in development, is a mobile firewall with a cloud component designed to secure devices against attacks just like these. This isn’t all that unusual, as many security firms like Sophos and Intego produce research reports along with consulting and security products. So, consider it noted.
Configuration Profiles (mobileconfigs) are small files installed with a single tap on iOS devices. They’re essentially instruction lists which can alter many settings, including network configurations and they’re used by thousands of companies around the world including app developers, corporations with IT departments and more.
Their use is officially approved by Apple and there is nothing innately malicious about any given profile. But, if put to the right uses, they do open up the ability to read usernames and passwords right off of a screen, transmit data that would normally be secure (over HTTPS) to a malicious server where it can be read and a lot more.
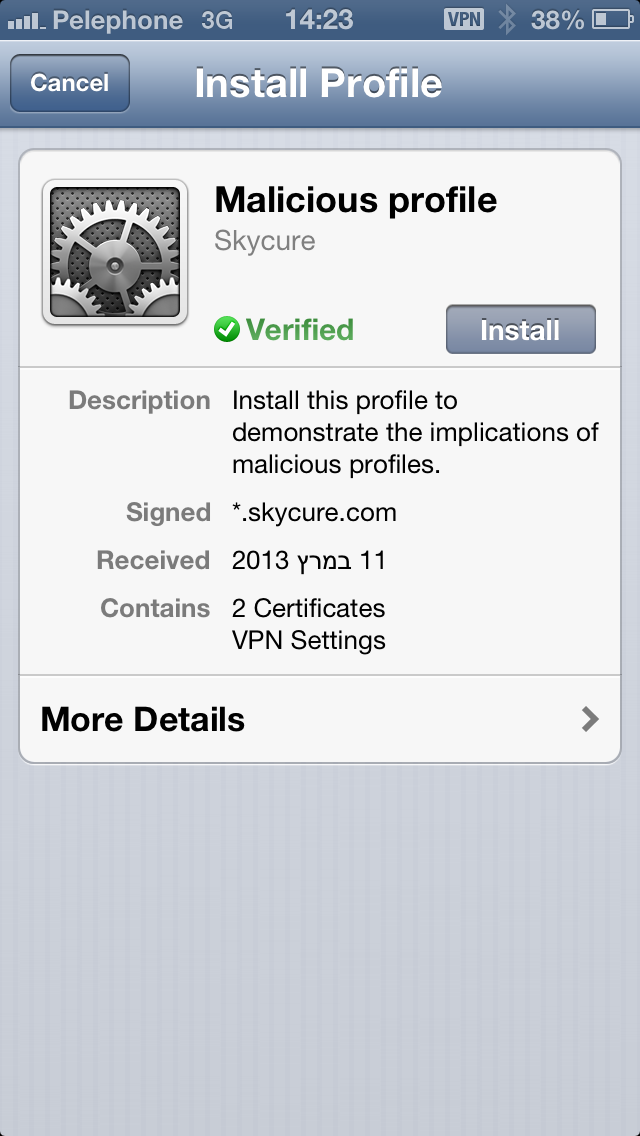
In a demonstration, Skycure’s CTO Yair Amit and CEO Adi Sharabani (with my permission) sent me to a website where I tapped a single link. A configuration profile was presented to me and I installed it with another tap. The screen looks basically like this:
If this is sounding a lot like a phishing attempt, which requires an action on the part of a user in order to infect or grant access to a hacker, then you’re on the right track. This is not a ‘drive by’ attack that can be accomplished just by visiting a website. But, as we’ll cover later, there are still many vectors by which a hacker could interject a ‘bad’ profile into what would normally be considered a legitimate workflow.
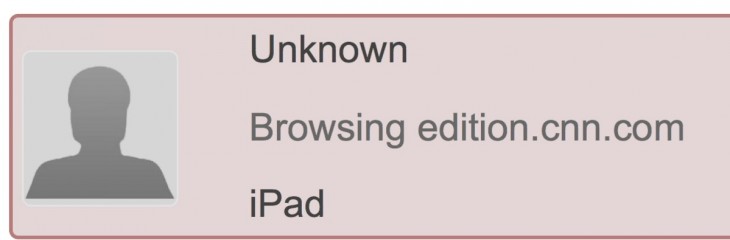
After the profile was installed, Sharabani demonstrated to me that he could not only read exactly which websites I was visiting, but also scrape keystrokes, searches and login data from apps like Facebook and LinkedIn. To be perfectly clear, this is not a vulnerability within iOS, instead it uses standardized frameworks to deliver a profile that has malicious intent.
iOS has typically been far more secure than other platforms because of its heavy use of curation on the App Store, but also because it has been built from the ground up to use sandboxing. This means that apps are cordoned off, unable to reach outside of their data box or to affect any other apps that have not given them explicit permission to do so.
Configuration Profiles step outside of that protection and can do things like route all of a victim’s traffic through a third-party server, install root certificates allowing for interception and decryption of secure HTTPS traffic and more.
Sharabani provides a couple of scenarios by which people could be convinced to install what seems like a harmless configuration profile, only to be a victim of a traffic re-routing attack:
- Victims browse to an attacker-controlled website, which promises them free access to popular movies and TVshows. In order to get the free access, “all they have to do” is to install an iOS profile that will “configure” their devices accordingly.
- Victims receive a mail that promises them a “better battery performance” or just “something cool to watch” upon installation.
Here’s an example of how a site could be configured to deliver a malicious Configuration Profile:
The attacks, Sharabani tells me, can be configured to use a VPN, APN proxy or a wireless proxy (WiFi), so just because you’re not on a WiFi network doesn’t mean that the profile can’t send your traffic to a third-party. This also means that (unlike a VPN, where there is an indicator in your status bar), you could also be affected by the hack without your knowledge. Of course, you would still have had to install a profile in the first place.
And that’s where the third scenario that Skycure points out comes into play. In its research, the firm came up with a list of cellular carriers that ask clients to install a special profile that configures their device to work with that network’s data servers. Of course, those sites could end up being compromised to deliver corrupted profiles, but it’s bound to be harder to do if it’s the carrier’s own servers doing the distribution.
Which is why a procedure that was in place at several AT&T stores Skycure visited was so eyebrow-raising. The stores regularly handed out a printed document that directed users to download a profile from Unlockit.co.nz, a site which hosts APN configuration files, mostly for international travelers. This is a third party site and the profile installation is not done over a secure connection. At one store, an installation was even performed from the site by an employee over a public WiFi network.
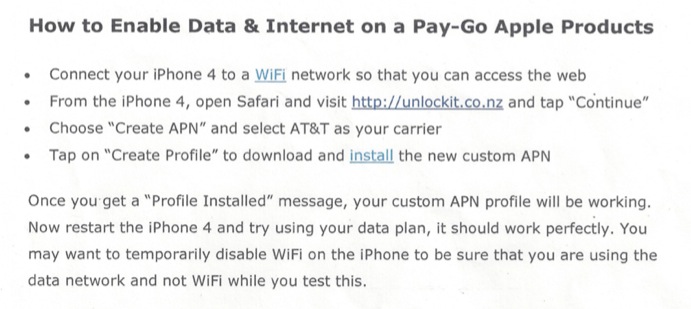
Skycure says that it has disclosed what it found to AT&T and has worked with them to address the issues it uncovered. But a carrier’s sloppy APN configuration procedures are really just a tip of the iceberg. People with a general knowledge of the way that wireless networks work and a desire to travel likely search the web for ‘APN settings’ hundreds or thousands of times a day. Any one of the sites returned that delivers a profile could end up hosting a malicious profile.
These types of attacks are, in some ways, the most insidious. Because so many companies rely on configuration profiles to do their business, it’s not as if they can up and stop using them. So precautions have to be taken.
As of now, no evidence has been found of a Configuration Profile attack in the wild. And, to be extremely blunt once again, you are not at risk at all if you don’t install any profiles to your device, period. And if you have to, make sure that those profiles are from a trusted source and are verified. You should also only download and install profiles from ‘secure’ HTTPS links.
The disclosure of the issue, Sharabani says, is really about raising awareness, rather than starting a panic. While the attacks can be powerful and harmful, the Configuration Profile attack, much like phishing, relies on user ignorance. Just as you wouldn’t type your password into a page provided as a random link, don’t install profiles from websites that you don’t know and avoid them completely if at all possible.
Because of the deep integration of Configuration Profiles into the workflows of IT departments and other companies, it’s unlikely that they’ll be going away any time soon. So the best defense for now is knowledge and care.
This article has been updated to utilize the accurate ‘Configuration Profile’ term.
Get the TNW newsletter
Get the most important tech news in your inbox each week.