
The Russian surveillanceware saga continues. Canadian cybersecurity researchers have discovered a new set of Android surveillance tools originating from Russia. The kicker? The spyware can be found in numerous fake apps disguised as legitimate software from Google, Pornhub, Skype, and many other familiar brands.
The spying toolset, dubbed Monokle, was purportedly developed by St. Petersburg-based private defense contractor Special Technology Center (STC) known for its ties to Moscow-headquartered Main Intelligence Directorate (GRU), according to a report from security firm Lookout.
Indeed, STC was one of the three entities Barack Obama sanctioned for meddling in the 2016 US elections and providing “material support to the GRU’s cyber operations” almost three years ago.
“Monokle is an advanced mobile surveillanceware that compromises a user’s privacy by stealing personal data stored on an infected device and exfiltrating this information to command and control infrastructure,” the researchers say.

Unlike other similar spyware, Monokle leverages advanced, previously unseen methods to sniff data.
The spyware employs data exfiltration techniques in novel ways, making use of the Android accessibility services (designed for users with disabilities) to collect data from third-party apps. It also enables man-in-the-middle attacks, relies on predictive-text dictionaries to fine-tune attack vectors to victims’ interests, and sneaks in screenlock traps to pick up users’ PINs and passwords.
In fact, Monokle performs pretty much every attack you can find in the book of spyware, including snatching account passwords, recording and eavesdropping on conversations and calls, taking photos and videos, selectively downloading files, keylogging interactions, deleting arbitrary files, retrieving contacts, and even exfiltrating messages from apps like WhatsApp, Instagram, Skype, and other messengers.

The researchers have been monitoring Monokle instances in the wild since at least 2016, with attacks spiking around the first half of 2018.
Their investigation found evidence STC is building a Monokle alternative for iOS to target iPhone and iPad users, but the firm has yet to catch it actively exploiting Apple devices. This is in line with reports from Forbes, suggesting STC was recruiting iOS and Android developers in 2017.
While still actively deployed, the spyware has consistently maintained a low level of activity, suggesting Monokle is mostly used for “highly targeted” attacks.
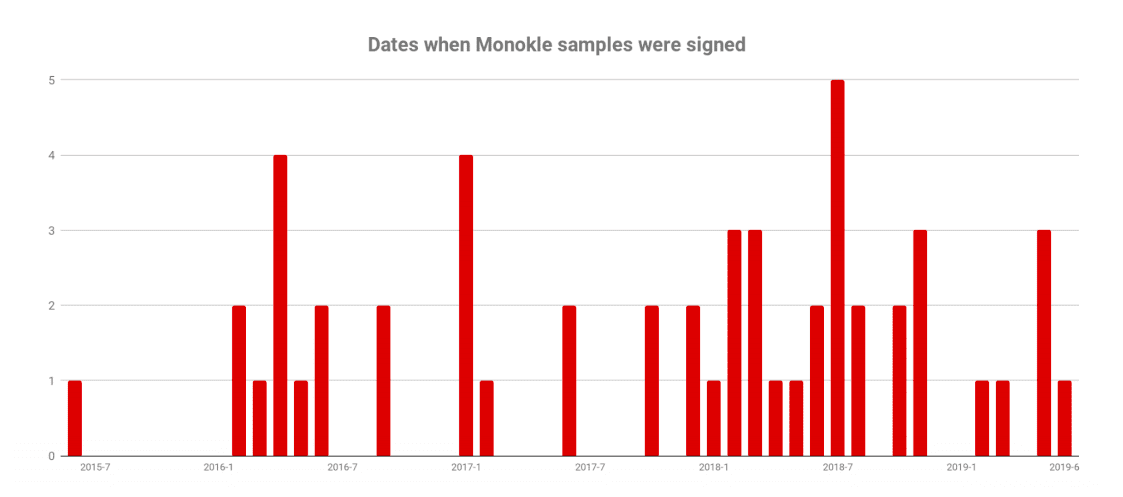
Lookout concludes Monokle is mostly targeting people interested in Islam and the the Ahrar al-Sham militant group in Syria, individuals associated with the Caucasus regions of Eastern Europe, and users of an app called UzbekChat.
This list, however, is far from exhaustive, according to their findings.
STC execs and the Russian government go way back
An investigation by Forbes found that STC’s executives are graduates of St. Petersburg’s Military Academy of Communications, a Russian Ministry of Defense school located within a five-minute drive of STC’s offices.
Its director Alexander G. Mityanin, for instance, went to the military school, where he received numerous medals by the Russian Ministry of Defense.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





