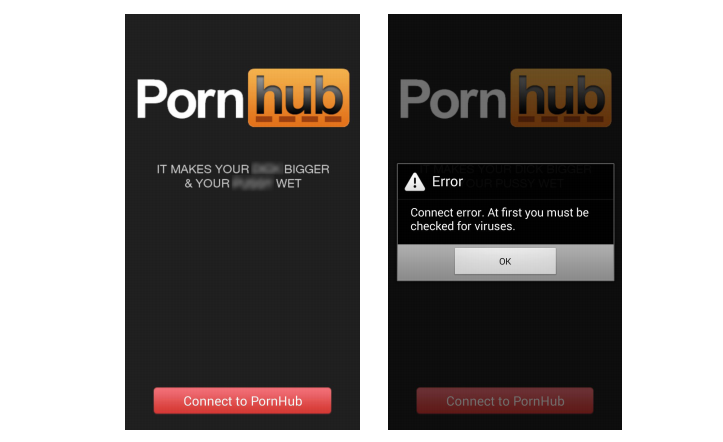
Better be careful where your lust takes you tonight as hackers have found a new way to infect users. It appears the internet is currently flush with rogue Pornhub apps designed to lock you out your device and hold your smartphone hostage.
Researchers from cybersecurity firm ESET have discovered a new attack vector [PDF] that seduces unsuspecting victims into installing malware by disguising infected Android software as legitimate Pornhub apps for mobile.
The anti-virus software firm claims that though Google usually vets apps submitted to the Play Store for malware, what makes this particular attack vector so successful is that the Big G currently bans X-rated software from the platform.
While Pornhub does indeed have an official app for Android, it currently remains unavailable on the Play Store as Google forbids pornographic apps from appearing on its software distribution platform – which has pushed users to look for alternatives from untrusted distributors.
But here’s the deal: Filtering out XXX content from the Play Store has also enabled hackers to easily prey on unsuspecting victims as their targets are now actively seeking alternatives in the wild. In a way, Google’s restrictions end up putting people at danger since the majority of such attacks usually take place outside of the Play Store.
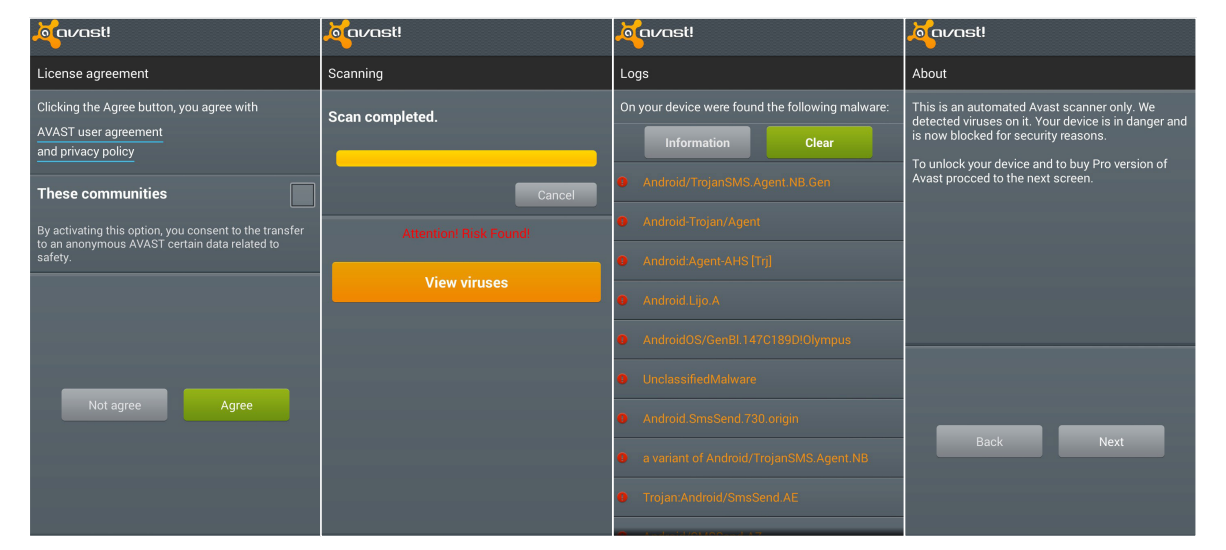
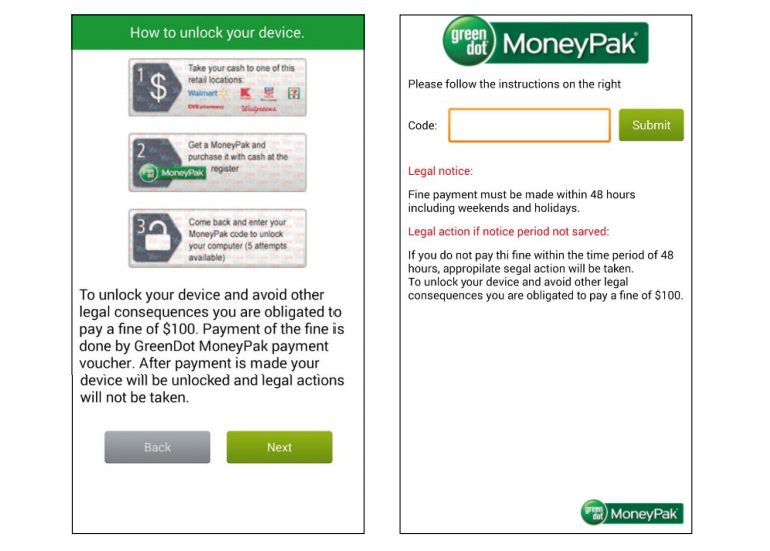
Once installed, the malicious app refuses to play any videos before it has been “checked for virus.” But instead of scanning for malware, the so-called virus check-up proceeds to install ransomware that locks you out of your device and prompts you to pay $100 in Bitcoin to regain access.
ESET has published guidelines on how steer clear from this specific malware, accompanied by some advice on how to remove the virus in case your handset has already been infected.
In addition to actively avoiding third-party software distributors, the cybersecurity firm recommends installing apps solely through the Play Store and keeping regular backups of your files – and especially photos.
Depending on the severity of the attack, there are also a few things you can do if your device has already been breached.
Booting up your device into Safe Mode – where third-party apps are immediately blocked – will allow you to easily wipe out the malware. The researchers further warn that, “in the event that the application has been granted Device Administrator privileges,” users will have to revoke access before deleting the app.
Malware that tampers with your screen lock functionality is more difficult to work around and will likely require resetting the lock screen via Google’s Android Device Manager or other alternative solutions. In case this proves insufficient, your last resort is to wipe the phone clean by performing a factory reset.
Check out ESET’s full report on its official website.
via RTLZ
Get the TNW newsletter
Get the most important tech news in your inbox each week.