Subscribe to this bi-weekly newsletter here!
Welcome to the latest edition of Pardon The Intrusion, TNW’s bi-weekly newsletter in which we explore the wild world of security.
In the last newsletter, we talked about using AI to tackle the problem of malware.
That got me thinking about how we can come up with efficient machine learning (ML) models to detect malicious content, especially as they’re constantly evolving.
You know how it goes: cyber baddies find one way to sneak malware onto computers, and security folks build defenses to stop them. The villains then find another way to creep in, a new defense is built.
Break in, defend, repeat. It goes on and on.
I asked Adrien Gendre, Chief Solution Architect at predictive email defense firm Vade Secure, about this. As it turns out, it requires understanding the threats you’re likely to face as a business and model an appropriate solution.
“When malware signatures change frequently, the machine learning models built to detect them lose their predictive capabilities,” Gendre says. “It’s essential that we define the malicious behaviors so that ML models are efficient.”
But this also means the models are trained not just on proper data sets, but also on adversarial inputs, he warns.
Here’s the catch: having huge amounts of training data alone doesn’t mean anything. There needs to be proper data quality checks in place too.
“What we need is a sound supervised ML model that’s built on quality data,” Gendre says.
So what does all this translate to? Before embracing AI for cybersecurity, businesses need to understand how they’re used, if they’re efficient, and if they have been done the right way.
***
Do you have a burning cybersecurity question, or a privacy problem you need help with? Drop them in an email to me, and I’ll discuss it in the next newsletter! Now, onto more security news.
What’s trending in security?
- A new parody website generates random excuses to explain why companies got hacked and apologize to their users. [Why the fuck was I breached?]

- Privacy-focused search engine DuckDuckGo has rolled out Smarter Encryption, which routes you automatically to encrypted versions of websites. [DuckDuckGo]
- Throwback to a 2015 story about a hacker and modern-day Robin Hood: Hamza Bendelladj was sentenced in the US for using a computer virus to steal money from more than 200 American banks and financial institutions to give millions of dollars to Palestinian charities. [Al Jazeera]
- A small minority of Robinhood users gamed a bug within the free trading platform to get infinite money to trade stocks. [Bloomberg]
- Talk about going rogue. An employee of cybersecurity firm TrendMicro sold data belonging to 68,000 customers — less than 1% of the company’s 12 million customer base — to tech support scammers. [Ars Technica]
- This new attack employs obfuscation chains to evade antivirus protections and steal user passwords, track online habits and hijack personal information from Google Chrome, Safari, and Firefox. [Cisco Talos]
- Ransomware attacks popped up in different cities in Louisiana and Boston targeting government entities and hospitals. Another was directed at a major web hosting firm SmarterASP.NET.
- A peek into Microsoft ATP, the team tracking the world’s most dangerous hackers. [MIT Technology Review]
- Google had an independent cybersecurity subsidiary called Chronicle. Here’s the chronicle of how it went up in flames. [Motherboard]
- Apple is working on a fix for a bug in macOS that stores encrypted email messages in a plain text format. [Bob Gendler]
- This new MegaCortex Ransomware variant was found to encrypt your files, change your password, and threaten to publish your files if you don’t pay up. In a separate discovery, researchers detected an uncommon form of ransomware that’s being deployed in targeted attacks against enterprise servers.
- There’s finally an iOS app that can check if your iPhone’s been hacked. [iVerify]
- Security researchers found weaknesses in Android phones’ underlying baseband software that can be exploited to trick vulnerable phones into giving up their unique identifiers — such as their IMEI and IMSI numbers — downgrade a target’s connection in order to intercept phone calls, forward calls to another phone or block all phone calls and internet access altogether. [TechCrunch]
- Amazon patched a flaw in Ring doorbells that exposed the passwords for the Wi-Fi networks to which they were connected to in cleartext, allowing nearby hackers to intercept the Wi-Fi password and gain access to the network to launch larger attacks or conduct surveillance. [TechCrunch]
- 2019 is officially the worst year for data breaches — 5,183 data breaches were reported with 7.9 billion records exposed in just the first 9 months of this year. [Risk Based Security]
- ZombieLoad flaw returned from the dead as a new version that could allow any hacker who manages to run code on a target computer to force Intel chips to leak sensitive data — something the company neglected to fix for nearly 14 months. [Wired]
- An Iranian government-linked hacking group — dubbed “APT33” — has been using botnets for extremely targeted malware campaigns against organizations in the Middle East, U.S., and Asia. [Trend Micro]
- IT provider InfoTrax Systems detected a security breach only after one of its servers maxed out its storage capacity — the result of the hacker creating a data archive file that had grown so large that a hard drive ran out of space. [FTC]
Data Point
New statistics published by APWG have revealed that phishing attacks are at the highest level in 3 years. The total number of phishing sites detected in July through September 2019 was 266,387. This was up 46% from the 182,465 seen in the second quarter of 2019, and almost double the 138,328 seen in Q4 2018.
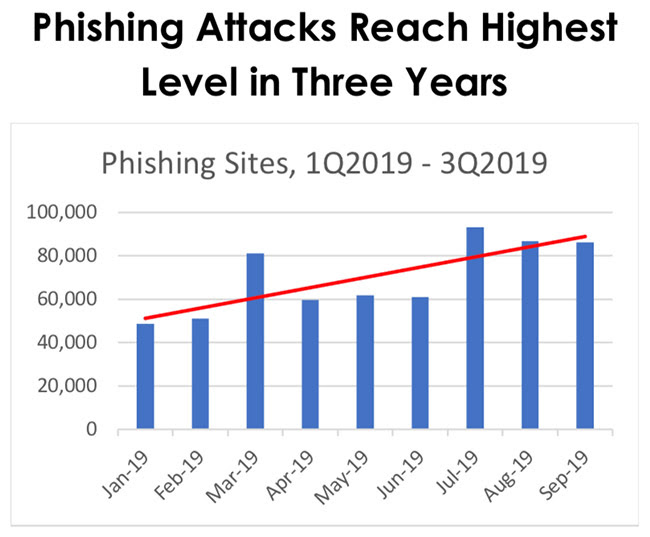
Takeaway: It’s no surprise that attackers are constantly looking for new ways to trick users into giving out personal information. Part of the reason phishing attacks continue to be successful is because there’s always going to be someone who will click a shady link. What’s needed is an urgent awareness about phishing campaigns that target them and help the public understand why they are at risk.
Tweet of the week
I was a victim of identity theft once. The perpetrator sent me some money, flowers and a sympathy card that said “Sorry I had no idea things were so bad”
— karanbir singh (@karanbirtinna) November 18, 2019
That’s it. See you all in 2 weeks. Stay safe!
Ravie x TNW (ravie[at]thenextweb[dot]com)
Get the TNW newsletter
Get the most important tech news in your inbox each week.