Subscribe to this bi-weekly newsletter here!
Welcome to the latest edition of Pardon The Intrusion, TNW’s bi-weekly newsletter in which we explore the wild world of security.
It’s always good to see more consumer tech companies stepping up to protect our privacy and security.
Previously, it was Apple, now it’s Mozilla’s turn. The company behind the Firefox browser has begun rolling out encrypted DNS over HTTPS (DoH) for US users by default. If you’re outside the US, you can manually turn it on in the settings.
Whenever you visit a website (say, thenextweb.com), that web address gets forwarded to a server that resolves it to an IP address. This is DNS — Domain Name System — and it functions pretty much like a phonebook for the internet.
There’s another way, though. You can fiddle with your network settings to explicitly configure your own DNS resolver.
All good, but here’s the catch: the address lookup isn’t unencrypted, which means anyone can snoop on your browsing habits.
This is where Firefox’s DoH comes in. The new feature — which makes use of Cloudflare or NextDNS servers — encrypts your browser’s DNS lookups, and makes it difficult for eavesdroppers to monitor which websites you visit.
Why is it important? Mozilla is making this change for privacy reasons: “DNS lookups are sent to servers that can spy on your website browsing history without either informing you or publishing a policy about what they do with that information.”
But the move is not without its share of controversy. Mozilla’s reliance on Cloudflare instead of trying to upgrade to a DoH-compatible server operated by the user’s existing DNS provider — something Google Chrome does — has attracted criticism for centralizing this whole process to just a few DoH resolvers.
On the other hand, is it even worth it? Even with DoH, your internet service provider (ISP) can still figure out the IP address of the destination, which reveals the actual website you are trying to connect to.
Mozilla was also called an “internet villain” last year by the UK’s Internet Services Providers’ Association because it would make it difficult for ISPs to identify malware-laced websites, terrorist content and child abuse imagery. The company, in response, has outlined a series of opt-in controls to handle such scenarios.
With the encryption battle already scaling new highs, Mozilla’s new efforts will doubtless face some resistance. But if it shifts the needle on privacy even a tiny little bit, it’s a good thing.
***
Do you have a burning cybersecurity question, or a privacy problem you need help with? Drop them in an email to me, and I’ll discuss it in the next newsletter! Now, onto more security news.
What’s trending in security?
In the past two weeks, a data breach at Slickwraps hit 857,000 users, the KidsGuard app was found to be stalkerware, and personal details of more than 10 million guests at MGM Resorts hotel were posted on a hacking forum.
- New cyber-espionage campaign alert! Iranian hackers are hacking VPN servers to plant backdoors in companies around the world. [ClearSky]
- The US linked “Sandworm” hacking group to Russian agency GRU’s Main Center for Special Technology, blaming it for cyberattacks that hit neighboring Georgia in October. [WIRED]
- Personal details of more than 10.6 million users who stayed at MGM Resorts hotels, including Twitter CEO Jack Dorsey and pop star Justin Bieber, have been published on a hacking forum. [ZDNet]
- Researchers disclosed the existence of 12 potentially severe security vulnerabilities, collectively named ‘SweynTooth,’ affecting millions of Bluetooth-enabled pacemakers and blood glucose monitors worldwide. Troubling enough, some are yet to be patched. That’s not all. More than 55% of medical imaging devices – including MRIs, XRays and ultrasound machines – are powered by outdated Windows versions. [WIRED / Threatpost]
- State-sponsored North Korean hackers — dubbed “Lazarus” aka “Hidden Cobra” — found using as many as six malware to “conduct illegal activity, steal funds & evade sanctions.” [Ars Technica]
- Yodlee, a major US financial data broker, claims it sells anonymous credit card data on Americans, but it’s not really anonymous: “The data includes a unique identifier given to the bank or credit card holder who made the purchase; the amount spent for the transaction; the date of the sale; the city, state, and zip code of the business the person bought from, and other pieces of metadata.” Takeaway: anonymized data is less anonymous than previously thought. [Motherboard]
- Phishing scam targeting Puerto Rico’s Industrial Development Company swindles the agency out of more than $2.6 million. [Associated Press]
- Google’s phishing resistant Titan security keys are now available in Austria, Canada, France, Germany, Italy, Japan, Spain, Switzerland, and the UK. [Google Security Blog]
- Chinese hackers have breached online betting and gambling sites in an campaign called “Operation DRBControl.” [TrendMicro]
- A hacker group — dubbed “APT-C-23” — catfished soldiers in the Israel Defense Forces (IDF) using display photos of young girls and directing them to download malware disguised as chat apps. [Bleeping Computer]
- How Estonia emerged as a source of cybersecurity inspiration after the 2007 cyberattacks. [WIRED]
- The Linux Foundation’s Core Infrastructure Initiative (CII) and the Laboratory for Innovation Science at Harvard (LISH) have revealed the most frequently used open-source components and the vulnerabilities they share. [ZDNet / CII]
- KidsGuard app has been found to be stalkerware — the irony! — after an unprotected database was found to secretly slurp all information on a target device, including its real-time location, text messages, browser history, access to its photos, videos and app activities, and recordings of phone calls. Here’s you can remove it. [TechCrunch]
- A misconfiguration by WhatsApp allowed ~470K group invite links to be indexed by search engines like Google. [TNW via Motherboard]
- Amazon-owned home security subsidiary Ring made two-factor authentication mandatory and paused the use of most third-party analytics services after a string of privacy and security blunders. Alas, it’s SMS based. But something is better than nothing. [Ring]
- “Raccoon” malware is being used to steal sensitive and confidential information including login credentials, credit card information, cryptocurrency wallets and browser information from almost 60 applications. [CyberArk]
- We may finally be closer to unearthing more about the xHelper malware that reinstalled itself on Android phones even after factory resets: A collection of files contained in hidden folders that, when executed, installed the malware. It’s not clear how the files survived factory resets, though. [MalwareBytes]
- PayPal fixed a bug in its Pay integration after hackers exploited it to carry out unauthorized transactions via PayPal accounts. [ZDNet]
- The fortnight in data breaches: the US Defense Information Systems Agency, Rallyhood, Samsung Electronics UK, Slickwraps, and Transmit Security.
Data Point
MalwareBytes 2020 State of Malware Report has found that threats against Macs outpaced that of Windows, with infections increasing year-over-year by more than 400% in 2019. Although some of it is also due to a growing number of Mac users in the same period.
In 2019, the average number of “detections” per Mac was 11, compared to an average of 4.8 in 2018, meaning the number of attacks targeting Macs had more than doubled. What’s more, adware related detections — one of the most dominant threat categories — jumped to 30 million, in comparison to Windows’ 24 million.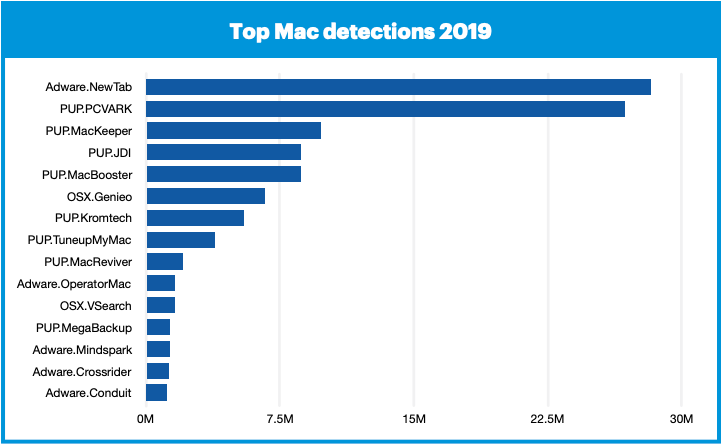
That’s it. See you all in a couple of days. Stay safe!
Ravie x TNW (ravie[at]thenextweb[dot]com)
Get the TNW newsletter
Get the most important tech news in your inbox each week.