A new piece of Android malware has been discovered that can intercept your incoming text messages and forward them on to criminals. Once installed, the trojan can be used to steal sensitive messages for blackmailing purposes or more directly, codes which are used to confirm online banking transactions.
The malware in question, detected as “Android.Pincer.2.origin” by Russian security firm Doctor Web, is the second iteration of the Android.Pincer family according to the company. Both threats spread as security certificates, meaning they must be deliberately installed onto an Android device by a careless user.
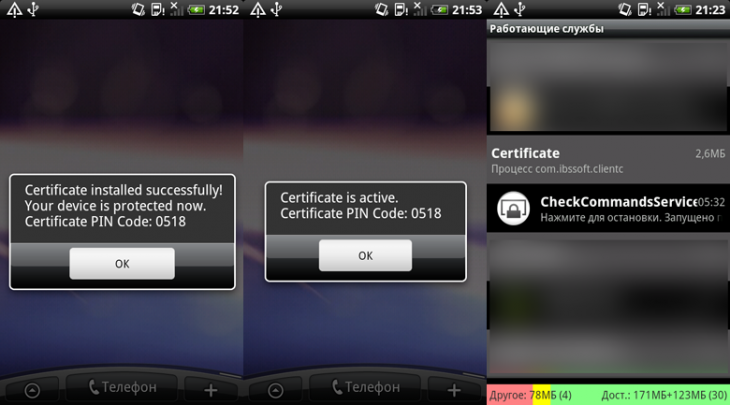
Upon launching Android.Pincer.2.origin, the user will see a fake notification about the certificate’s successful installation but after that, the trojan will not perform any noticeable activities for a while. Here are a few screenshots:
The malware is loaded at startup via CheckCommandServices, a service that runs silently in the background (right-most screenshot above). It will then connect to a remote server and send over the following information about the mobile device to those behind the attack: handset model, device’s serial number, IMEI, carrier, cell phone number, default system language, operating system, and availability of the root account.
The threat then awaits instructions that contain commands in the following format: command:[command]. Doctor Web has found criminals can send the following instructions to the trojan:
- start_sms_forwarding [telephone number]— begin intercepting communications from a specified number
- stop_sms_forwarding — stop intercepting messages
- send_sms [phone number and text] — send a short message using the specified parameters
- simple_execute_ussd — send a USSD message
- stop_program—stop working
- show_message—display a message on the screen of the mobile device
- set_urls – change the address of the control server
- ping – send an SMS containing the text ‘pong’ to a previously specified number
- set_sms_number—change the number to which messages containing the text string ‘pong’ are sent.
The first one allows attackers to indicate the number from which the trojan should intercept messages, meaning this can be used for targeted attacks to steal specific messages. The third one from the bottom shows the criminals have planned for changing servers in case they believe the current one will be shut down.
Although Doctor Web doesn’t say so, the good news here is that Pincer2 is not likely to be very prevalent. It has not been found on Google Play, where most Android users should be getting their apps, and appears to be meant for precise attacks, as opposed to being aimed at as many users as possible.
In short, this malware threat isn’t one that you will likely be hit with, but it is an interesting example of how Android malware is evolving. Our advice is the same as always: only install apps that you know are safe.
Top Image Credit: Flavio Takemoto
Get the TNW newsletter
Get the most important tech news in your inbox each week.