The founder of security-focused messenger Signal, Moxie Marlinspike, revealed today that he found and exploited vulnerabilities in software from Cellebrite, a company that specializes in digital forensics tools that have been used by authorities around the world to extract data from phones.
In a blog post, Marlinspike claimed that he found one of the company’s devices in a package that fell out of a truck — that’s some luck, huh? He added the Cellebrite device has multiple bugs that could be used to take over it.

Here’s how he actually did it: They placed an innocuous-looking — albeit specially formatted — file on the device that Cellebrite’s software would eventually scan. After that, the attackers could remotely execute any arbitrary code that could modify the unlocker device’s report.
Our latest blog post explores vulnerabilities and possible Apple copyright violations in Cellebrite's software:
"Exploiting vulnerabilities in Cellebrite UFED and Physical Analyzer from an app's perspective"https://t.co/DKgGejPu62 pic.twitter.com/X3ghXrgdfo
— Signal (@signalapp) April 21, 2021
Plus, the code can modify past and future reports to make authorities question the authenticity of the device.
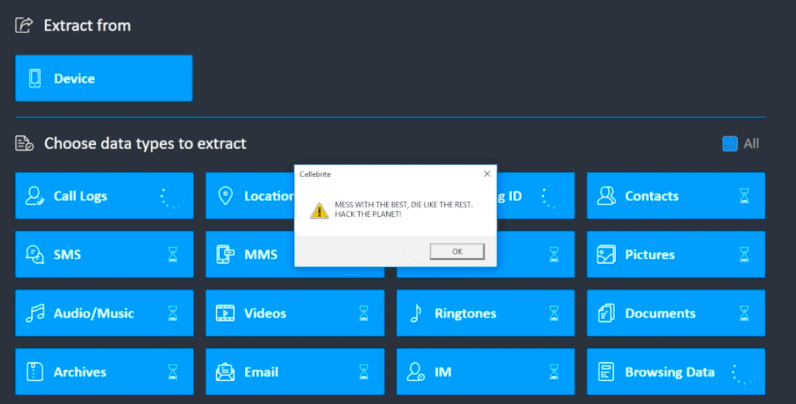
To demonstrate the possibilities of the hack, the Signal team used the MessageBox Windows API to display the message that read: MESS WITH THE BEST, DIE LIKE THE REST. HACK THE PLANET!
Marlinspike also found signed packages of iTunes version 12.9.0.167 — possibly extracted from the Windows Installer — that could trigger a copyright violation against Cellebrite from Apple, if it turns out the forensics firm had included these packages without the company’s permission.
In a response to the incident, a Cellebrite representative told Ars Technica that the company holds regular audits of its software, but didn’t specifically comment on the hack:
Cellebrite is committed to protecting the integrity of our customers’ data, and we continually audit and update our software in order to equip our customers with the best digital intelligence solutions available.
To further fuel the fire, Marlinspike said that Signal will responsibly disclose all vulnerabilities to the company if it could “do the same for all the vulnerabilities they use in their physical extraction and other services to their respective vendors, now and in the future.”
Signal’s discoveries come months after the data extracting company announced that it added support to parse Signal data to their Physical Analyzer software.
While Cellebrite has made hefty claims of its devices and software working with a range of phones over the years, security researchers have claimed that it’s been easy to execute code on those extractors. This new incident could have authorities question Cellebrite devices’ accuracy and safety, and the findings its products bring forth in investigations.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




