If there’s one thing you need to know about the criminal economy, it’s this: no one is coming after you in particular. No one is trying to steal your identity.
It’s easy to frame identity theft as a personal experience because identity theft has clear personal consequences and a tangible personal impact. Here’s the thing, though: Identity theft isn’t personal. It’s business.
I’ve spent years working on and in the dark web fraud community, evaluating how information — often personal information — is discussed, marketed, valued, and traded. When I first started analyzing the dark web, I was stunned by how well structured the personal information economy was; how quickly it became mundane to see names, addresses, emails, and passwords, all laid bare day after day. We often see identity theft portrayed as a shady individual lurking near your local ATM, but on the dark web, the reality is far more enterprising than that.
What is the dark web?
The dark web includes the internet underground, only accessible through anonymizing technologies. These technologies mask user location and make it difficult to locate sites hosted within the dark web network. Takedowns often involve coordinated law enforcement efforts, as seen this summer with the takedown of a massive dark web marketplace called Alphabay.
The dark web is a network built on privacy, and that privacy is afforded to users and dark websites alike. The dark web is used for a number of things, and contrary to popular belief, most dark web activity is legal. A report from 2016 determined more than 50 percent of the dark websites themselves are legal — in fact, The New York Times recently launched a dark web version of its site.
A portion of the dark web, however, is made up of criminal enterprises — places where vendors can advertise stolen credit cards, user databases, step-by-step phishing guides, or new exploit kits. The same technology that protects legal users also provides a platform for trade in illegal goods and services.
A thriving criminal economy
The dark web economy, while full of scams and instability, is incredibly well organized. Administrators operate ecommerce platforms (think of a set-up like eBay), providing payment services, review functionalities, and dispute mechanisms. Some markets offer a variety of goods and services (choose between cocaine, streaming video accounts, utility bill templates — a one-stop shop!), while other markets specialize, often specifically focusing on drugs or fraud.
Vendors take pride in their listings, publishing glossy advertisements, offering holiday sales, and even bulk discounts. Meanwhile, as in other business enterprises, fraud buyers look for ways to operate at scale; they aim to automate their processes and maximize their return on investment — and that means ensuring purchases of valid social security numbers, working credit cards, and accurate passwords.
That’s what your data is to these criminals: a cog in the wheel of a growing enterprise. Criminals don’t care where the information came from, who it belongs to, or what the impact might be of emptying a bank account; they’re here to make money, and they’re going to make it with whatever details they have at their disposal. Criminals focus on maximizing their efficiency, which means they turn to the most easily operationalized data types (read: the easiest information to exploit).
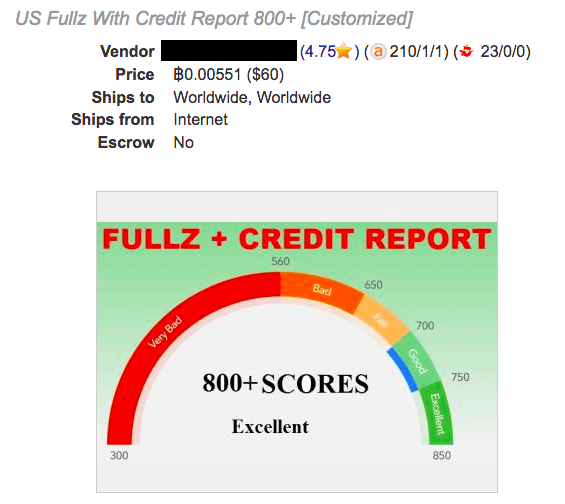
What kind of information is in high demand? Social Security Numbers (SSNs) are both valuable and immediately useful. SSNs provide easy access to other accounts; think about the last time you used your SSN to confirm your identity or to make a change to a password. SSNs can be used to look up other information (names, dates of birth, addresses, contact details). SSNs go for just a few dollars on the dark web — in fact, one market was selling the Social Security Numbers of children (plus two parents, bonus!) for just $10 a set. Hello, tax fraud!
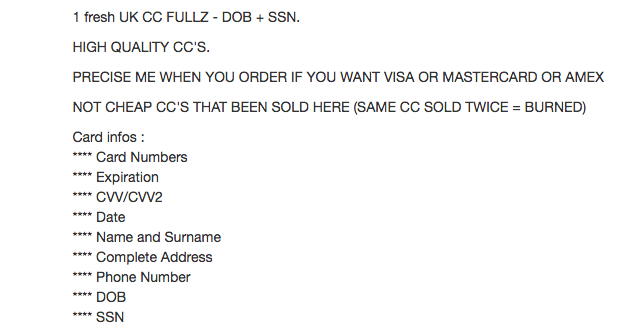
Full identity kits (“fullz”) are also valuable and readily traded. Fullz typically contain a name, date of birth, address, social security number, financial details, and occasionally other personal information. An average fullz costs between $5-25 on the dark web depending on the information included—pocket change for a criminal enterprise.
Fraud is alive and well online. So what?
What does this mean in practice? It means no one is coming after your information specifically, but you may still suffer the consequences as criminals go after information generally. Any time a new data set gets introduced into the criminal economy, that data is going to be used and reused, sold and resold — recycled through the community until it expires, and then sold again. Some information has a limited shelf life (e.g., a credit card, canceled as fraudulent charges appear), but some information is good for years, decades, or even lifetimes.
Lifetime data is the reason the Equifax breach is so potentially damaging; these weren’t just payment cards being exposed. This is the personal information for hundreds of millions of people. This is the information you carry with you for the rest of your life, information that is incredibly valuable and incredibly difficult, if not impossible, to change. As a consumer, I saw Equifax as a massive security failure and a breach of trust. As a fraud expert, I saw it as fresh stock for a thriving economy.
The Equifax data has not yet begun to circulate on the dark web in any discernable way. If and when it does, it won’t matter to the criminals that it came from Equifax. It won’t matter that it’s your data, or my data — this information is just fresh fuel for the fire.
What can you do? First, take control of your basic security. I’ll say the same things you’ve heard before (they’re important!): use strong passwords and use different passwords on every site (password managers are a life-saver for this). Take a step further, when you can, by using two-factor authentication whenever possible. The extra step to help you log in will help keep criminals locked out. Second, start thinking of identity theft as an industry, and look at breaches as new additions to the supply chain. For criminals, emptying your bank account or filing fraudulent tax returns is just another day at the office.
Get the TNW newsletter
Get the most important tech news in your inbox each week.