
Researchers have uncovered a new kind of “advanced” phishing attack targeting Android phones that can trick users into installing malicious settings on their devices that are disguised as innocuous network configuration updates.
The spoofing attack, disclosed by cybersecurity firm Check Point Research today, has been found to be successful on most modern Android phones, including the Huawei P10, LG G6, Sony Xperia XZ Premium, and Samsung Galaxy S9. But any phone running Android can be targeted this way.
Given that Samsung, Huawei, LG, and Sony account for more than 50 percent of all Android phones, the scope of the attack is understandably far broader in scope.
According to the report, the phishing ploy leverages over-the-air (OTA) provisioning — a technique often used by telecom operators to deploy carrier-specific settings on new devices — to intercept all email or web traffic to and from Android phones using specially-crafted bogus SMS messages.
“A remote agent can trick users into accepting new phone settings that, for example, route all their internet traffic to steal emails through a proxy controlled by the attacker,” wrote researchers Artyom Skrobov and Slava Makkaveev.
The vulnerability can be exploited at all times throughout the day as long as the phones are connected to their carrier networks. Wi-Fi hotspots, however, are not impacted.
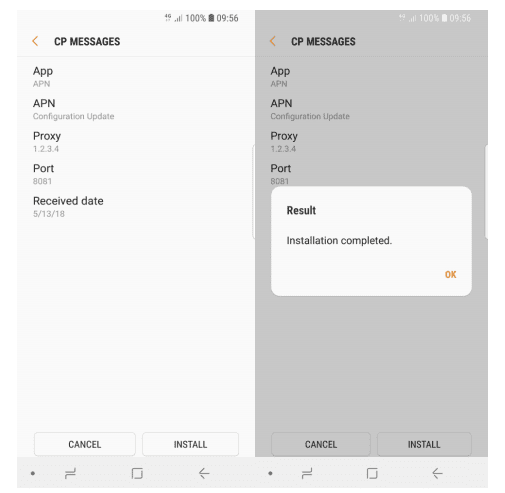
Troublingly, all a cybercriminal is needs is a GSM modem, which can then be used to dispatch a rogue provisioning message to the susceptible phones by getting hold of their international mobile subscriber identity (IMSI) numbers, a unique string tied to each device that tells apart every user of a cellular network.
The provisioning message follows a format — called Open Mobile Alliance Client Provisioning (OMA CP) — specified by Open Mobile Alliance. But they are also weakly authenticated, meaning a recipient cannot verify whether the suggested settings originated from their carrier or from a fraudster trying to execute a man-in-the-middle attack.
Samsung phones were the easiest to attack, with no form of authentication need to install an OMA CP message. As a result, an attacker could potentially change the MMS message server, the proxy address for Internet traffic, the browser homepage and bookmarks, the email server, and any directory servers for syncing contacts and calendar.
On the other hand, devices from Huawei, LG, and Sony were relatively more secure, since they required the sender of the provisioning message to provide the phone’s IMSI code before accepting the message.
However Check Point researchers noted they were easily able to identify a target’s IMSI number using a reverse IMSI lookup service available via commercial suppliers.
Additionally, with over a third of all Android apps having access to a device’s IMSI code via “READ_PHONE_STATE” permission, a threat actor can easily use a malicious app that leaks the IMSI code in this fashion to target specific users with fake OMA CP messages.
After Check Point privately disclosed its findings in March, all companies with the exception of Sony have issued patches or are planning to fix the vulnerability in upcoming releases. Samsung tackled the flaw in its May security update (SVE-2019-14073), while LG fixed it in July (LVE-SMP-190006).
Huawei intends to plug the exploit in its upcoming smartphones, per Check Point, but it’s not fully clear if the US-China trade war will cause additional complications. Sony, for its part, is currenty sticking to the current OMA CP specification, with OMA tracking this issue separately.
Threat actors have long gone after various methods to stage all sorts of phishing attacks. But the idea that an attacker can send custom SMS messages to modify the network and internet settings in the device via clever social engineering campaigns is a reminder that phishing attacks aren’t just limited to email.
Although the modus operandi detailed by Check Point requires human intervention, there’s no easy way for an unsuspecting user to determine the authenticity of these messages.
The takeaway, ultimately, is that you should be vigilant about installing anything untrusted on your device, especially things that are delivered via text messages or linked in texts.
“Threat actors are becoming better at extracting information outside of Wi-Fi hotspots each and every single day,” the researchers said. “We should all be on extra alert, especially when we’re not connected to public Wi-Fi hotspots.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.





