![‘Pinkie Pie’ notches second full Chrome exploit worth $60k at Pwnium 2 hackathon [updated]](https://img-cdn.tnwcdn.com/image?fit=1280%2C720&url=https%3A%2F%2Fcdn0.tnwcdn.com%2Fwp-content%2Fblogs.dir%2F1%2Ffiles%2F2012%2F10%2Fpwnium2.jpg&signature=4803592eb486e599f77d5ec684204da1)
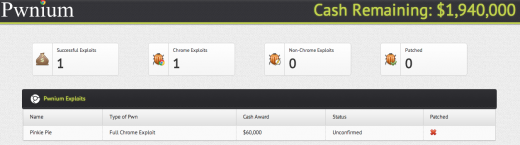
After outsmarting Google earlier this year, a teenager hacker has managed another successful exploit of the Chrome browser at today’s Pwnium 2 hackathon competition. The hacker, who goes by the alias “Pinkie Pie”, achieved a full Chrome exploit, which should win him a $60,000 cash prize.
In March, Pinkie Pie and Sergey Glazunov both won $60,000 for their exploits at the first Pwnium competition. Google established the Pwnium competition as an alternative to the Pwn2own contest in order to add the requirement that participants provide details of their exploit.
The company had offered to hand out up to $2 million to those who discover vulnerabilities at Pwnium 2, which took place as part of the Hack In The Box security conference in Kuala Lumpur, Malaysia.
Google software engineer Chris Evans is in attendance and has promised to discuss any exploits and vulnerabilities found during the hackathon at a follow-up talk at the conference. Google will “be actively analyzing” any submissions in order to bulk up the security of its browser.
Update: Pwnium 2 has now closed with just the one submission from Pinkie Pie. Google has confirmed that it will pay the $60,000 prize and has already patched the flaw.
In order to qualify for the cash, his exploit must meet the following criteria:
• Be an unreported and original exploit, which has not been shared or partially shared with anyone else or submitted in any other contests until it has been submitted to, and judged by, Google.
• Be an exploit relying on an unreported and original bug, bugs or security feature in Chrome or in Chrome when used in connection with Windows, Flash or other software e.g. drivers.
• Be a remote exploit accessible through the Chrome browser, which works and is reliable.
• Be present in the most recent supported channel(s) of Chrome, running on the latest version of Windows7 on the provided test machine.
• Be a critical vulnerability of high impact.
• Be authored or created by You.
• Be submitted with corresponding documentation that details each bug exploited.
(hat tip Gunther_AR)
Header image credit: Hack In the Box
Get the TNW newsletter
Get the most important tech news in your inbox each week.





