Google today announced its plans to sunset the SHA-1 cryptographic hash algorithm as Chrome uses it in certificate signatures for HTTPS. The company hopes to start the process later this month with version 39’s release in November and finish it when Chrome 41 arrives in Q1 2015.
When the CA/Browser Forum published their Baseline Requirements for SSL in 2011, SHA-1 was essentially deprecated. In other words, CAs have long been told to move away from SHA-1. Google Chrome will hopefully encourage those straggling behind to hurry up.
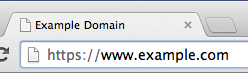
Here is the timeline for using the HTTPS security indicator to highlight that SHA-1 doesn’t cut it anymore:
- Chrome 39 (First build on September 26, 2014): Sites with end-entity (“leaf”) certificates that expire on or after January 1, 2017, and which include a SHA-1-based signature as part of the certificate chain, will be treated as “secure, but with minor errors.” They will get a lock with a yellow triangle, which is also used to highlight other deprecated and insecure practices.
- Chrome 40 (First build on November 7, 2014; Stable after holiday season): Sites with end-entity certificates that expire between June 1, 2016 and December 31, 2016 (inclusive), and which include a SHA-1-based signature as part of the certificate chain, will be treated as “secure, but with minor errors.”
Sites with end-entity certificates that expire on or after January 1, 2017, and which include a SHA-1-based signature as part of the certificate chain, will be treated as “neutral, lacking security.” They will get a blank page icon (also used for HTTP). - Chrome 41 (Expected in Q1 2015): Sites with end-entity certificates that expire between January 1, 2016 and December 31, 2016 (inclusive), and which include a SHA-1-based signature as part of the certificate chain, will be treated as “secure, but with minor errors.”
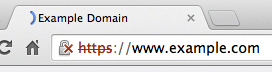
Sites with end-entity certificates that expire on or after January 1, 2017, and which include a SHA-1-based signature as part of the certificate chain, will be treated as “affirmatively insecure” while their subresources will be treated as “active mixed content.” They will get a lock with a red X and a red strike-through text treatment in the URL scheme.
SHA-1 was designed in 2005, and is widely considered too weak for proper security measures. “Collision attacks against SHA-1 are too affordable for us to consider it safe for the public web PKI,” Google explains. “We can only expect that attacks will get cheaper.”
Instead of waiting for that to happen, Google is taking a proactive approach to protect its users.
See also – Three years in, Google has paid researchers over $2 million in security rewards and fixed more than 2,000 bugs and Google begins offering financial rewards for proactive security patches made to select open-source projects
Image credit: shankrad/Flickr
Get the TNW newsletter
Get the most important tech news in your inbox each week.