
Malicious apps impersonating Turkish cryptocurrency exchange BtcTurk are circumventing Google’s recently adopted security enhancing measures.
According to researchers, the apps are accessing one-time passwords (OTPs) and SMS-based two-factor authentication (2FA), was well as some email-based 2FA systems.
By impersonating the cryptocurrency exchange, the apps are able to phish for users’ login credentials.
Instead of intercepting SMS messages to bypass 2FA protection on users’ accounts and activity, the malicious apps take the OTP from notifications appearing on the comprised device’s display.
Worryingly, besides being able to read the 2FA notifications, the apps are also to dismiss them, meaning victims are unable to notice the fraudulent transaction taking place.
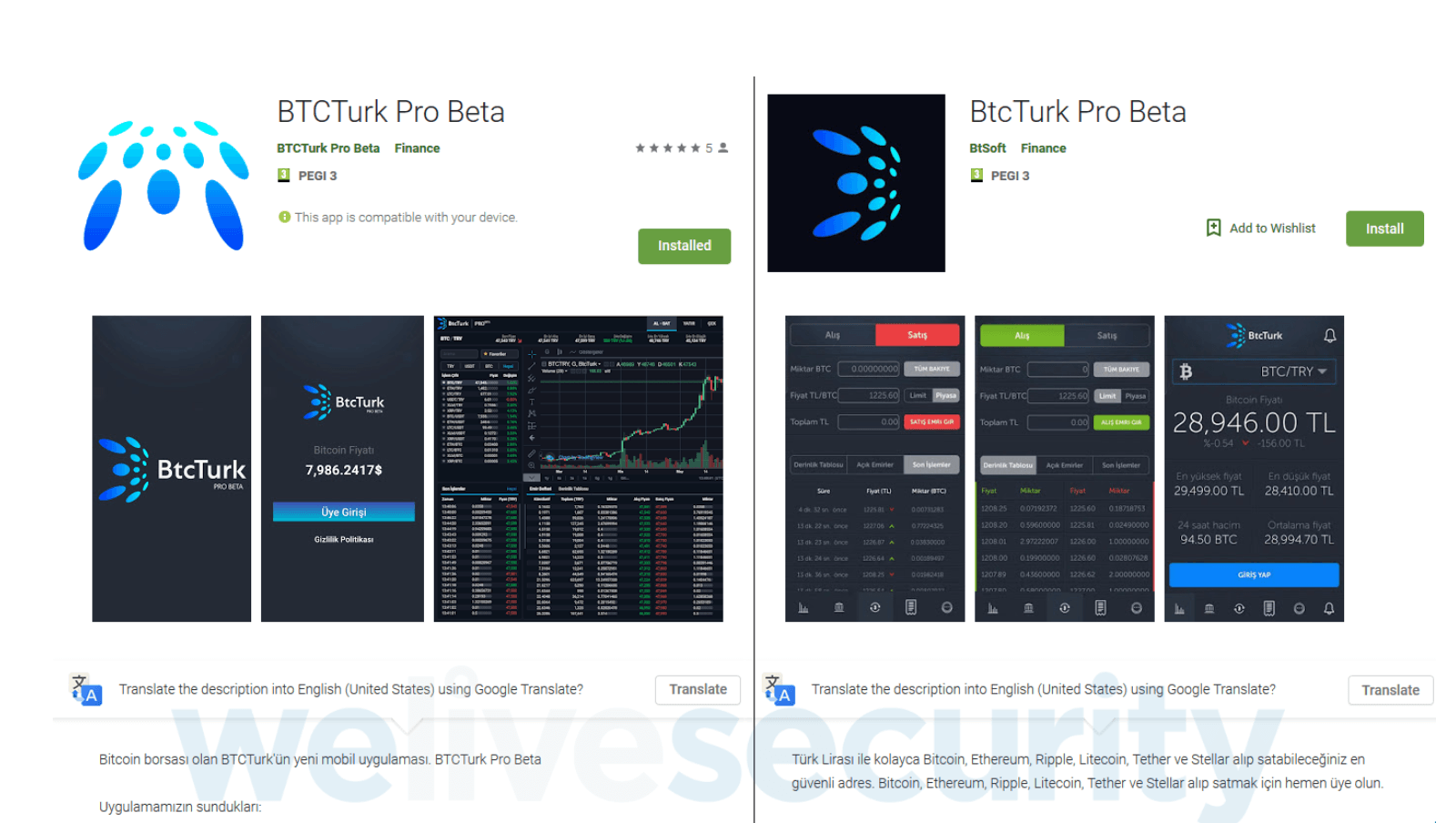
The first malicious app that was analyzed by ESET was uploaded to Google Play on June 7 as “BTCTurk Pro Beta,” under the developer name “BTCTurk Pro Beta.”
It was installed by over 50 users before it was reported by ESET to Google’s security teams. In fact, it’s worth noting that BtcTurk’s official mobile app is linked to the company’s exchange service and is only available to users in Turkey.
Several days later, on June 11, the second app was uploaded under the name “BtcTurk Pro Beta.” Attackers used “BtSoft,” a different developer name this time.
Essentially, the two apps use a similar guise, but researchers have pointed out they are seemingly the work of different attackers. This second app was reported on June 12, after it had been downloaded by less than 50 people.
Undeterred, the attackers uploaded a third app with identical functionality, this time using “BTCTURK PRO” as the app name and resorting to the same developer name, icon and screenshots. This version was reported on June 13, 2019.
The discovery comes after ESET analyzed another malicious app impersonating Koineks, another Turkish cryptocurrency exchange. The app used the same malicious technique to bypass SMS and email-based 2FA but unlike the most recent versions lacks the ability to dismiss and silence notifications.
In the meantime, Android users are being advised to remain vigilant, uninstall any suspicious apps, and change their passwords.
The discovery comes a little under a month after ESET researchers found at least two apps on Google Play had been specifically designed to steal users’ coins.
Prior to that, security researcher Harry Denley unearthed a phishing campaign that tricked victims into downloading a malicious Chrome extension, programmed to get hold of users’ private keys.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





