Google is suffering from an epidemic of malicious cryptocurrency apps on the Play Store – and it seems the internet giant is struggling to curb the influx.
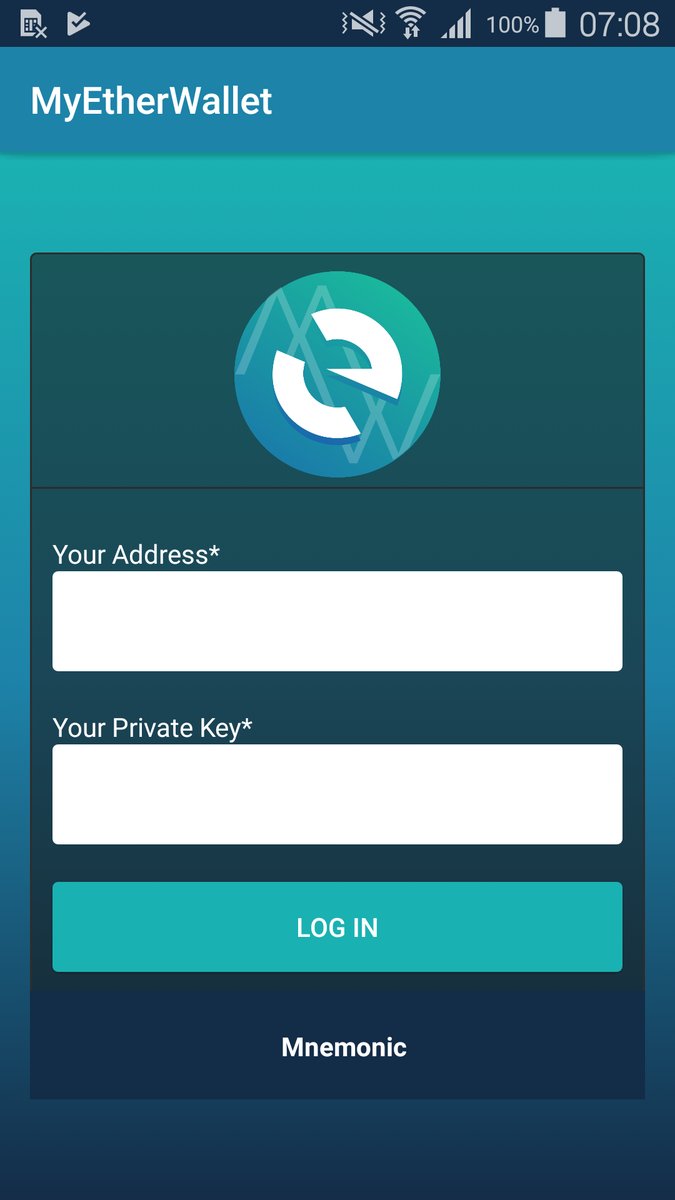
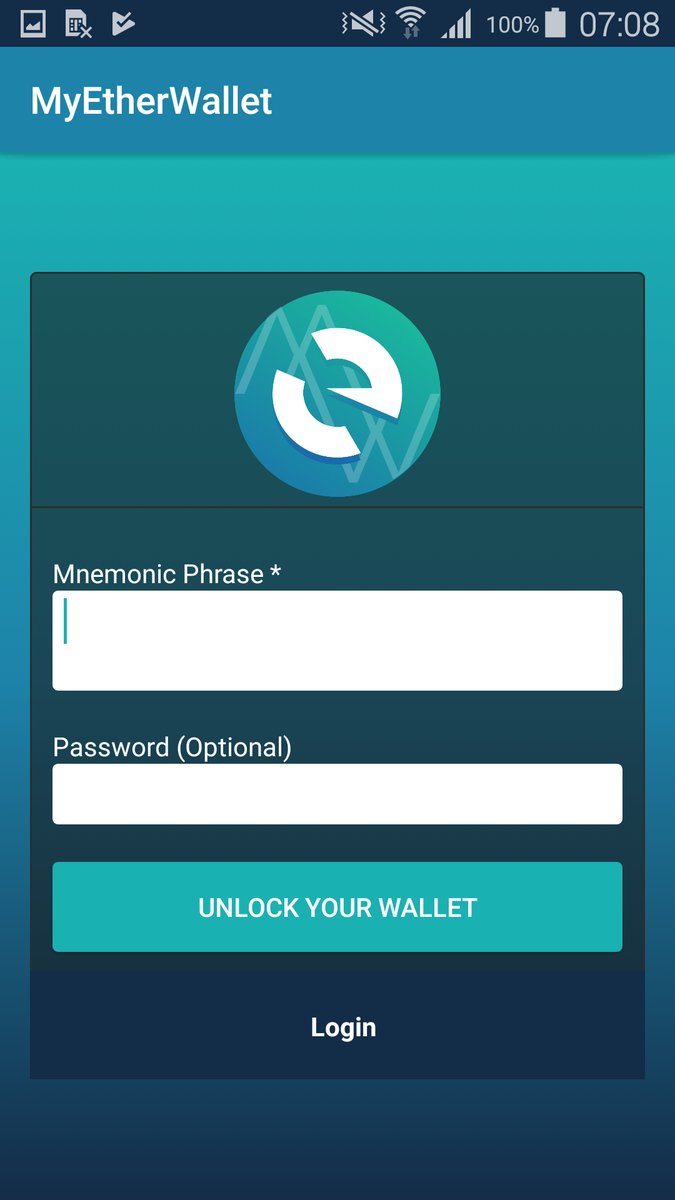
Security researcher Lukas Stafanko has come across another rogue copycat of popular cryptocurrency app MyEtherWallet designed to steal your private keys and surreptitiously drain your funds.
But here is the worst part: the malicious app purportedly remained available to download for four days before the Big G purged it from its software distribution platform, according to the researcher.
Fortunately, it appears that nobody downloaded the app during the four-day window it remained in the wild.
What is more problematic is that this is hardly the first time malware-infested software has slipped past Google’s security mechanisms.
In fact, this marks at least the third such occasion since the beginning of this year. Google was forced to remove another corrupted instance of MyEtherWallet back in January; more recently, the company purged a malicious Poloniex app designed to phish users’ credentials and private keys.
While data suggests that some of these malicious apps hardly got any traction, the MyEtherWallet copycat which made its way to the Play Store in January was downloaded between 100 and 500 times before it got taken down. One of the reasons it managed to garner some success was probably because it remained on the Play Store for almost a week.
Indeed, researcher Troy Mursch has since remarked Google has absolutely “no excuse” for failing to prevent malicious apps from popping up on the Play Store. “Slow abuse handling only provides more incentive for apps like this to be published,” Mursch said on Twitter.
I’ve seen @myetherwallet phishing sites stay up for months. No excuse for Google Play apps to remain for days however. Slow abuse handling only provides more incentive for apps like this to be published.
— Bad Packets Report (@bad_packets) April 18, 2018
For the sake of clarity, Google is not the only software distributor that has struggled to thwart the spread of malicious crypto apps on its platform.
Last December, another infected instance of MyEtherWallet made its way to the top of the Apple App Store; in fact, it was the third most popular app in the Finance section at one point.
Reports suggest that more than 3,000 people downloaded the shifty app before Apple eventually took it down.
This is NOT US. We have file reports and emailed and reported. Would appreciate the communities assistance in getting these scamtards out of our lives.
PS: We are #Foss4Lyfe https://t.co/SmI8cqNvxA
— MyEtherWallet.com (@myetherwallet) December 10, 2017
More recently, Apple had a similar mishap after it allowed a sketchy Calendar app with a built-in cryptocurrency miner on the App Store – despite the fact its policy strictly deems such monetization strategies “unacceptable.”
The real problem is that such blunders fly past Google and its Play Store at rates disturbingly higher than on any other platform.
Research from cybersecurity firm RiskIQ indicates it found 661 illegitimate cryptocurrency apps distributed across some 20 official software stores – including the Play Store and the App Store.
Out of these, a staggering 272 appeared on Google Play. By comparison, the second store on this list, APKFiles, accounted for 54 such apps.
In all fairness, cryptocurrency software comprises only a small chunk of all infected apps hosted on the Play Store. To give you some context, the company reportedly purged 700,000 “problematic apps” in 2017 alone; statistics suggest that Google houses a total of more than 3.5 million apps on its store.
In an effort to battle attackers, last year Google introduced its Play Protect security feature, designed to ensure there is nothing funny going on with apps downloaded from its software store.
While it is true that phishing sites have long lingered on Google Search, there is a certain (added) expectation of security that comes with downloading apps from official software platforms. We trust such apps because we assume that Google – or whoever is responsible for distribution – has vetted them.
But as Stefanko’s recurrent findings show, the mechanism is incapable of keeping up with the attackers’ ever-evolving methods: and unless Google finds a more efficient measure of counter-acting such ill-intended efforts, it is only a matter of time before someone gets burnt.
Get the TNW newsletter
Get the most important tech news in your inbox each week.