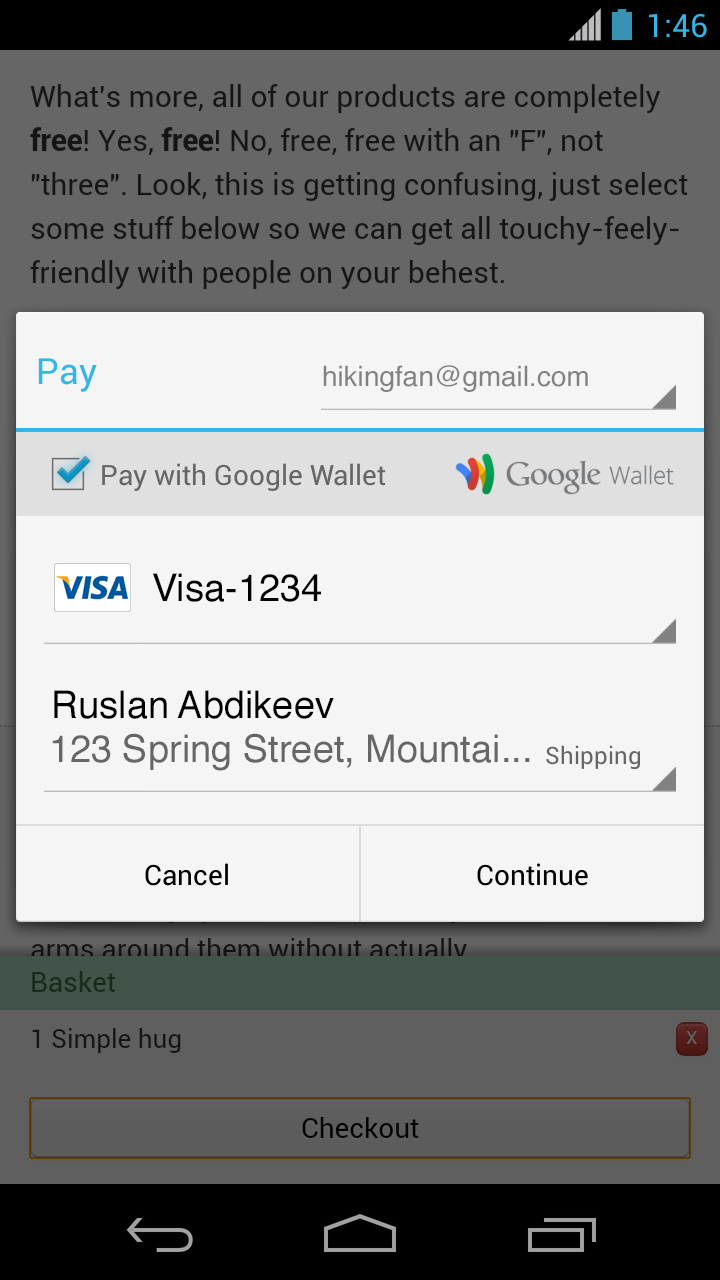
Google today released Chrome version 31 for Windows, Mac, and Linux. The new version includes support for Web payments, portable native code, and 25 security fixes. You can update to the latest release now using the browser’s built-in silent updater, or download it directly from google.com/chrome.
The first feature means users can now potentially fill out online forms with little effort. Web developers have been given programmatic access to the browser’s autocomplete information (with the user’s explicit permission) via a new function named requestAutocomplete(). Users can pick existing payment data stored with the browser or enter new details through a browser-provided interface, and then developers can continue with their existing payment processor.
As you can see above, the Web payments feature is available on Android. It also works on Windows and Chrome OS, and a Mac version “will be included in a future release,” although Google wouldn’t say when.
Next up, Google is pushing the performance of apps even further with Portable Native Client (PNaCl). You can read more about the launch over here.
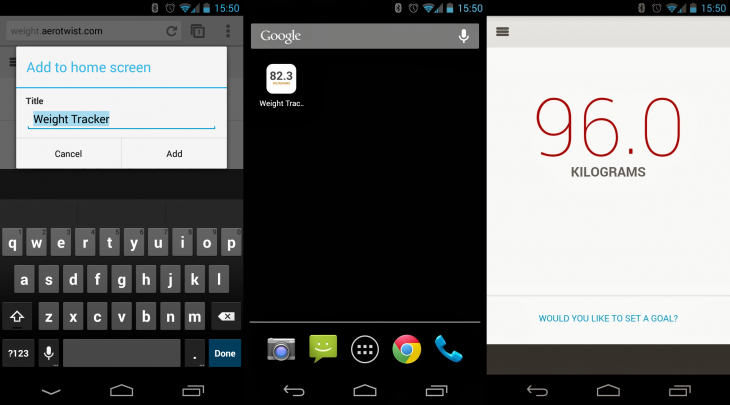
Chrome 31 for Android, which will be arriving soon on Google Play, has gained application shortcuts. In short, the feature lets users add website shortcuts to their Android home screen that open in a normal Chrome for Android window.
The only exception is if these sites include the mobile-web-app-capable meta tag. Those sites will instead open in a special fullscreen Chrome for Android window that doesn’t display tabs, buttons, menus, or the omnibox (see the right screenshot above).
As in previous releases, Google also included the usual bug fixes, stability improvements, and so on in Chrome version 31.0.1650.48. For more details, you can check out the full SVN revision log.
Last but certainly not least, Chrome 31 also addresses 25 security issues, of which Google chose to highlight the following:
- [$500][268565] Medium CVE-2013-6621: Use after free related to speech input elements. Credit to Khalil Zhani.
- [$2000][272786] High CVE-2013-6622: Use after free related to media elements. Credit to cloudfuzzer.
- [$500][282925] High CVE-2013-6623: Out of bounds read in SVG. Credit to miaubiz.
- [$1000][290566] High CVE-2013-6624: Use after free related to “id” attribute strings. Credit to Jon Butler.
- [$2000][295010] High CVE-2013-6625: Use after free in DOM ranges. Credit to cloudfuzzer.
- [295695] Low CVE-2013-6626: Address bar spoofing related to interstitial warnings. Credit to Chamal de Silva.
- [$4000][299892] High CVE-2013-6627: Out of bounds read in HTTP parsing. Credit to skylined.
- [$1000][306959] Medium CVE-2013-6628: Issue with certificates not being checked during TLS renegotiation. Credit to Antoine Delignat-Lavaud and Karthikeyan Bhargavan from Prosecco of INRIA Paris.
- [315823] Medium-Critical CVE-2013-2931: Various fixes from internal audits, fuzzing and other initiatives.
- [258723] Medium CVE-2013-6629: Read of uninitialized memory in libjpeg and libjpeg-turbo. Credit to Michal Zalewski of Google.
- [299835] Medium CVE-2013-6630: Read of uninitialized memory in libjpeg-turbo. Credit to Michal Zalewski of Google.
- [296804] High CVE-2013-6631: Use after free in libjingle. Credit to Patrik Höglund of the Chromium project.
Google also issued $2000 of additional rewards to miaubiz and Atte Kettunen of OUSPG for working with the company during the development cycle to prevent security bugs from ever reaching the stable channel. Google thus spent at least $13,000 in bug bounties this release. These fixes alone should push Chrome users to upgrade as soon as possible.
Top Image Credit: casasroger/Flickr
Get the TNW newsletter
Get the most important tech news in your inbox each week.