
It’s no secret cryptojackers prefer Monero, but now researchers have determined exactly how much they have gained with illicit cryptocurrency mining malware.
In a new study, academics from Universidad Carlos III de Madrid and King’s College London calculated that crypto-mining malware has generated roughly 720,000 XMR – or 4.32 percent – of Monero’s currently circulating supply, reports CoinDesk.
While the exact amount of generated revenue depends on when the criminals cash-out their earnings, the researchers estimated it to be worth nearly $57 million over the last four years ($1.2M per month).
Popular online code repository GitHub was recognized to host more of the mining malware than any other site.
A small group of wealthy bad actors are running the show
The research also analyzed where that XMR was being routed to. When hackers steal computing power to mine cryptocurrency surreptitiously, they can employ two possible strategies: joining a “mining pool,” or mine by themselves.
Using mining pools has advantages – it increases the odds of receiving payments for mining (as pools with more members are more likely to receive blocks to validate). It also reduces the need for specialized mining equipment.
What’s noteworthy is that an overwhelming majority of the XMR mined through cryptojacking campaigns has gone directly to one cryptocurrency mining pool: crypto-pool. To date, its members have mined at least 435,689 XMR (almost $47 million).
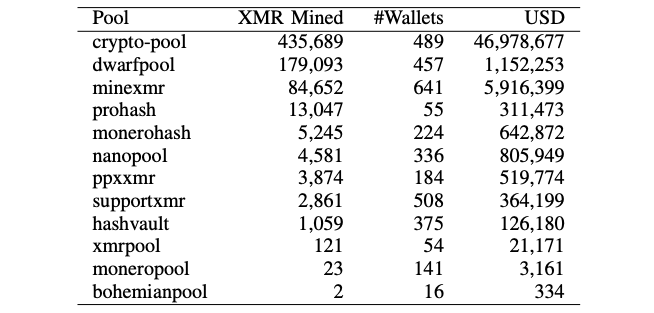
Researchers detected 2,472 cryptojacking campaigns, finding that 99 percent earn less than 100 XMR ($4.7K).
“We also observe that while majority of the campaigns earn very little, there are a few campaigns overly profitable,” they wrote. “This indicates that the core of this illicit business is monopolized by a small number of wealthy actors.”
GitHub hosts a lot of cryptocurrency mining malware
The researchers found hackers are using legitimate sites like GitHub and Dropbox to facilitate the spread of cryptocurrency mining malware.
Cryptojackers build special malware “droppers,” a variant of Trojan horse computer virus that forces a target to download and install more malware.
Most of the time, these droppers downloaded standard Monero mining tools hosted by GitHub.
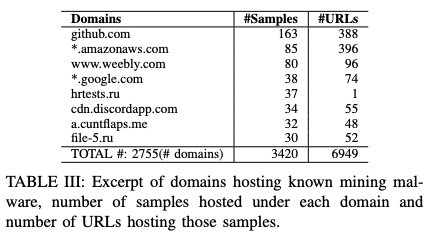
“We observe that GitHub is the most popular site used to host the crypto-mining malware. This is because GitHub hosts most of the mining tools, which are directly downloaded — for malicious purposes — by droppers,” the researchers wrote. “Additionally, GitHub is also used to host modified versions of the miners (e.g., by removing the donation capabilities or adding further capabilities).”
The paper lists other public repositories and file sharing sites favored by cryptojackers, including Bitbucket, Amazon Web Services, Dropbox, and Google.
The researchers also found Monero mining malware hosted as torrents, attachments in Discord channels, as well as obfuscated through various URL-shortener services.
Last September, the Monero community was forced to rebuke cryptojackers who had been terrorizing the internet, after government routers in the US were discovered to be housing mining malware.
Hackers also hijacked several municipality websites in India, forcing users’ browsers to illegitimately generate Monero with embedded malicious code.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





